Cyberhaven is the original data lineage company
Static inventory is easy; true lineage is not. Secure your data based on every movement, not just its location.
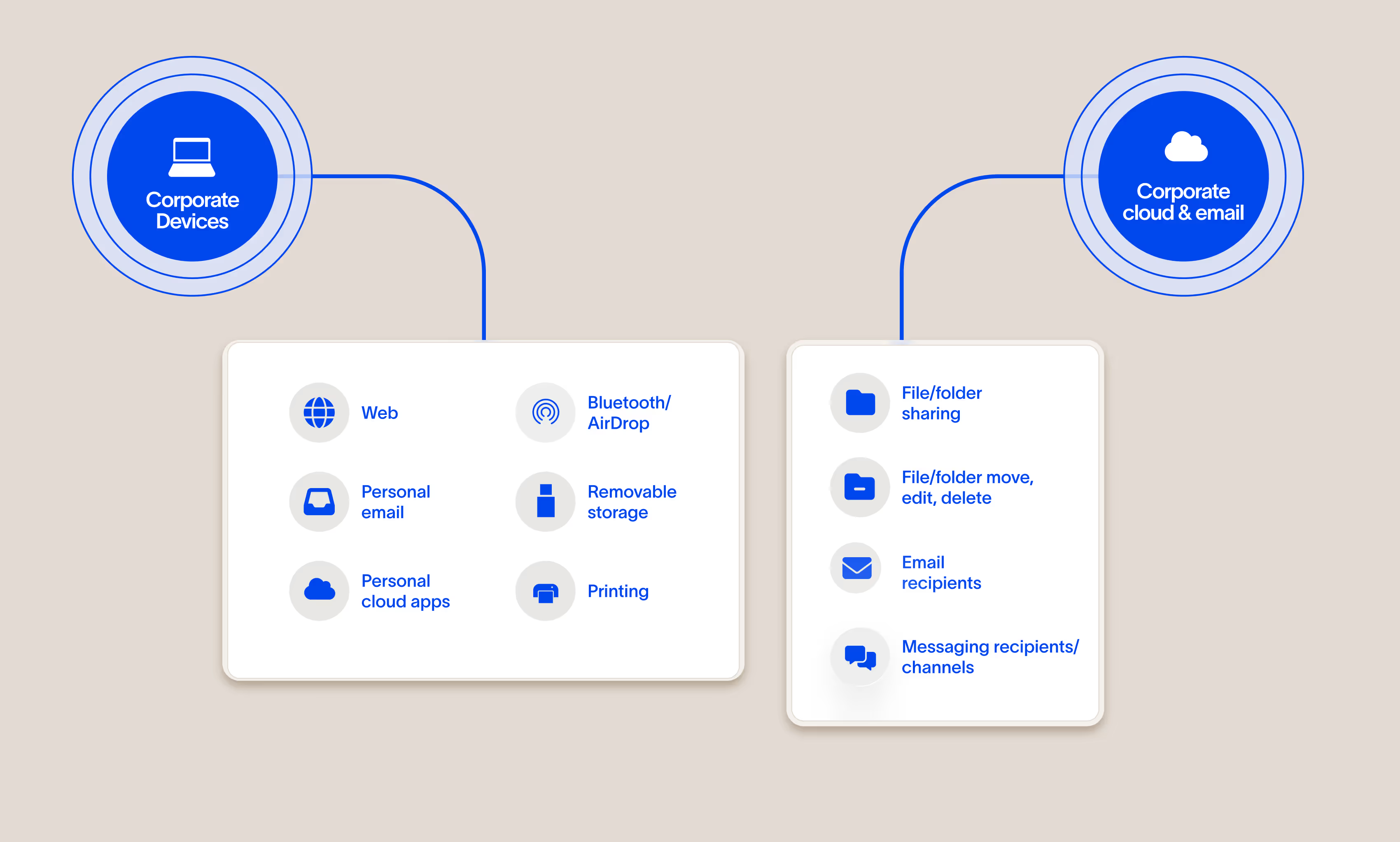
Collect all events for every piece of data
We see data everywhere it goes
Three deployment modes that together give full visibility and control over data
We developed an architecture that achieves complete visibility of your data, including as it transits unmanaged cloud apps and unmanaged devices.
Cloud API connectors
Cyberhaven connects to your sanctioned applications like Office 365 and Google Workspace to get visibility into content created and shared natively in the cloud.
Modern, lightweight endpoint agent
No, seriously. Our agent is designed from scratch to utilize modern operating system APIs and securely perform processing in the cloud so it doesn’t slow down devices or crash them. We support Windows, macOS, and Linux.
Browser extension
Supports all major browsers and collects telemetry for web-based cloud applications not available from other sources.
A flight recorder for data
These are just a few examples of the events we record for every piece of data:
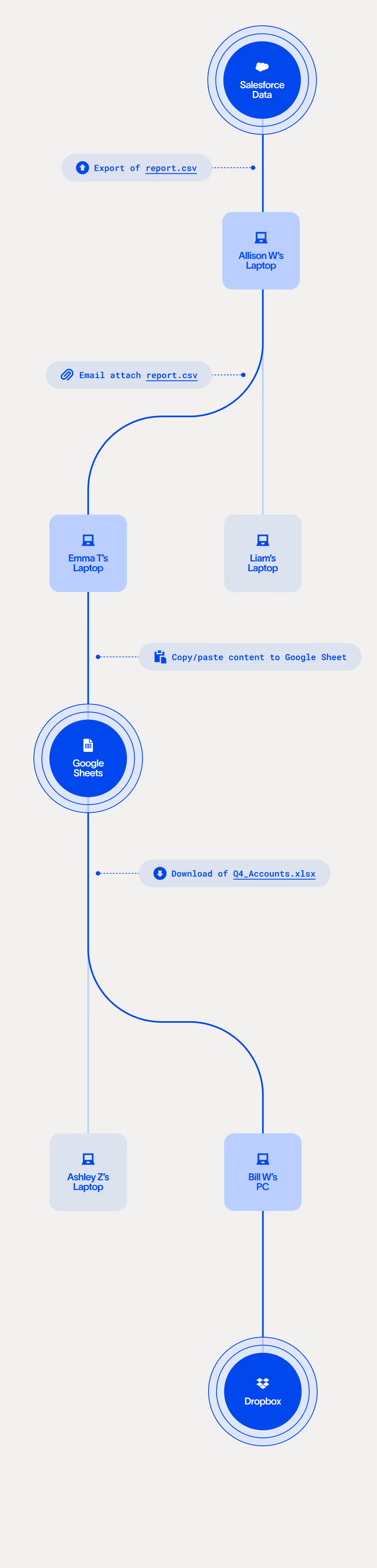
Trace data's lineage to classify and track it
Data lineage is a technology that’s only available from Cyberhaven. It traces data from its origin, providing the context we use to more accurately classify what type of data it is and protect it anywhere it goes.
data based on its origin in Salesforce.
Data lineage reveals a lot about the data and its importance
We can infer a lot about a piece of data based on where it originated, how it was handled, and the people who added to it without ever looking at its content.
Where it originated
Whether it’s the customer database in Snowflake, the source code repository in Github, or the product design board in Figma, specific types of data start their journey in specific places.
How it was handled
Data moves in recognizable ways, passing through the board meeting site in SharePoint, the client documents folder in Google Drive, or the employee offer letter account in DocuSign.
Who added to it
Different employees produce different work, from researchers who develop drug formulas, to designers working on new products, to accountants who compile financial results.
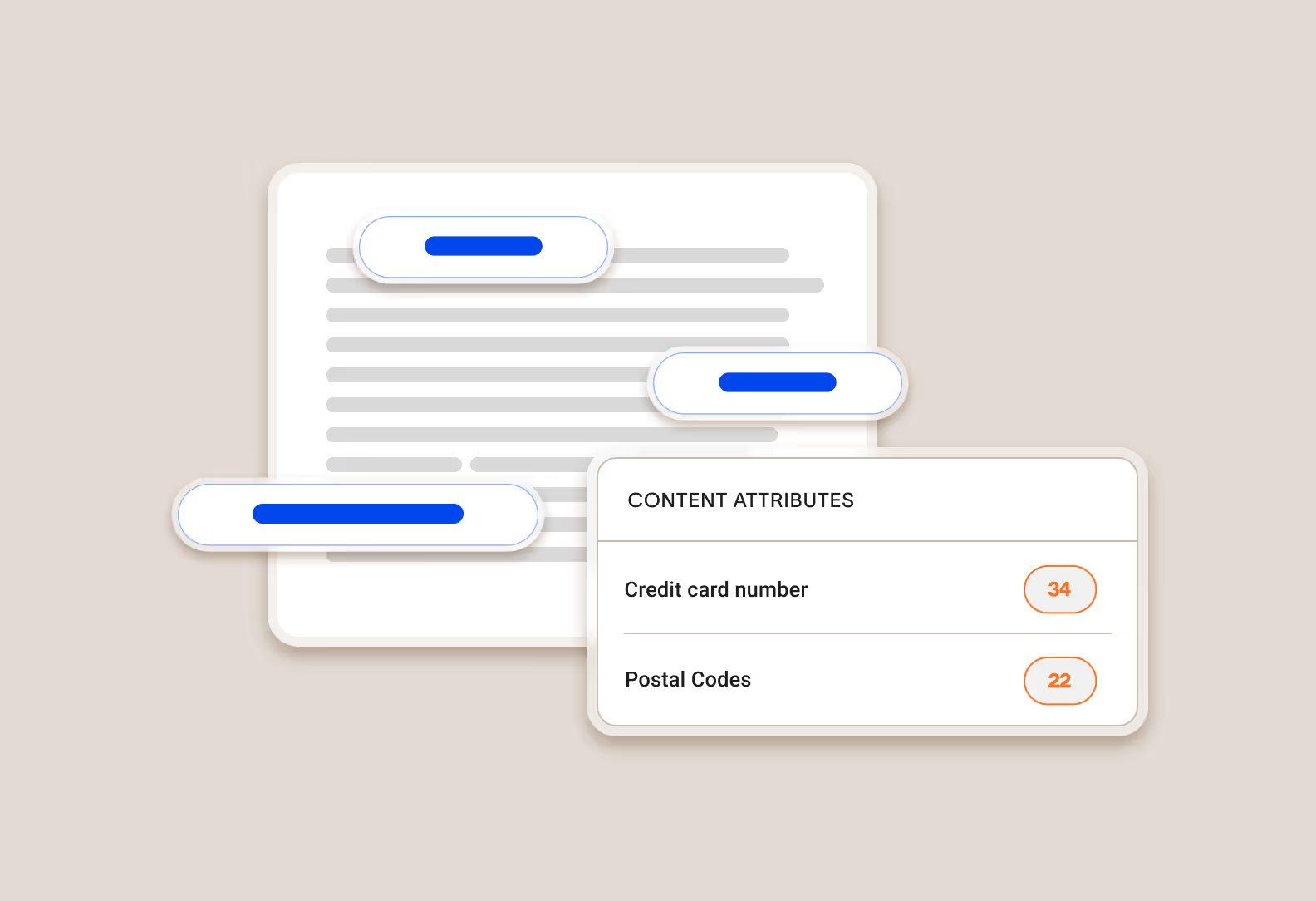
Content analysis adds to our understanding of the data
We extract text content present in the data and perform optical character recognition (OCR) on images to pull additional text content. Cyberhaven includes out-of-the-box content identifiers for common forms of PII, PCI, and PHI along with the ability to define your own patterns using regular expressions.
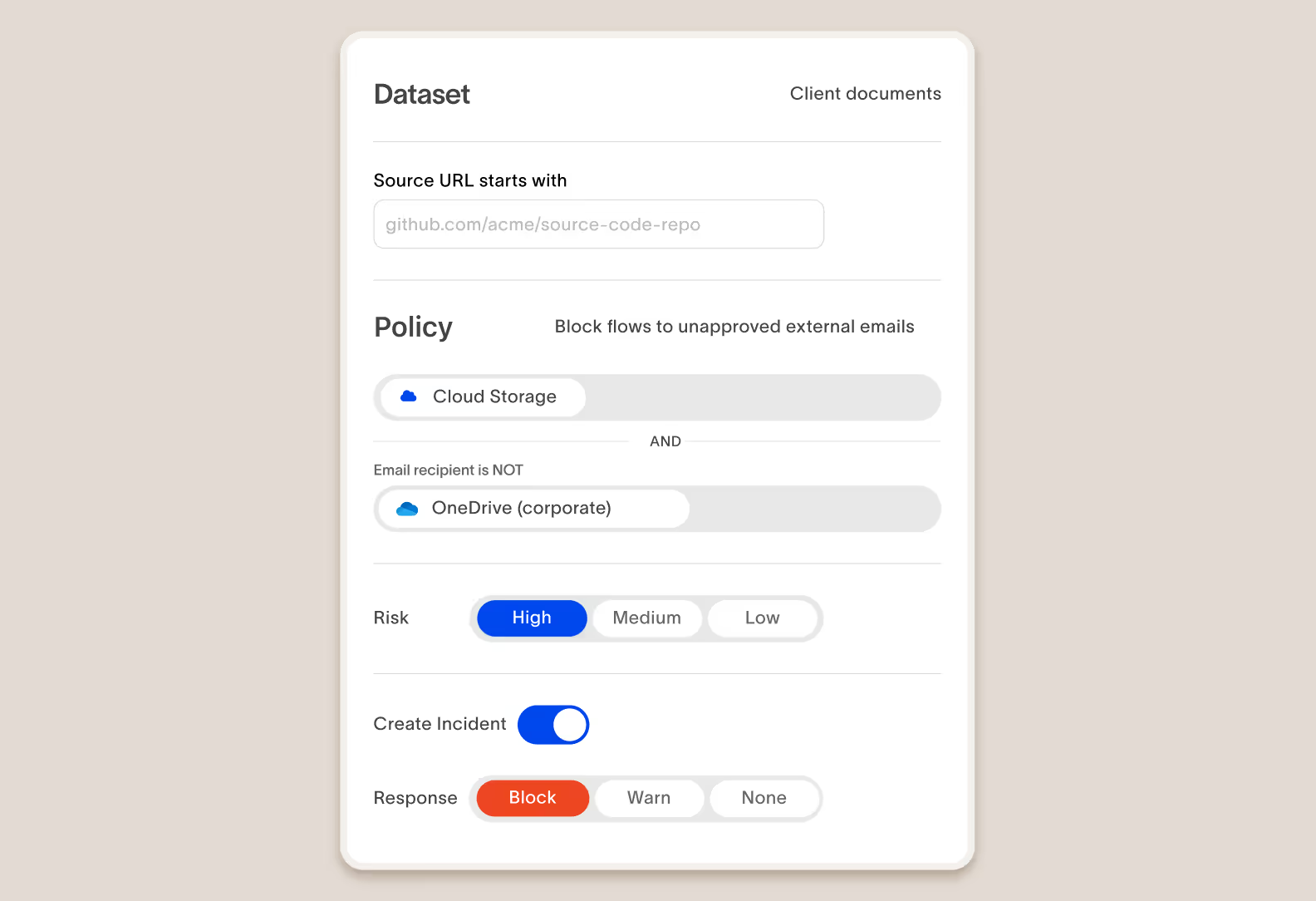
Enforce your data security policies
Our product allows you to define what is risky for your organization, enforce actions to protect data, and educate your workforce in real time.
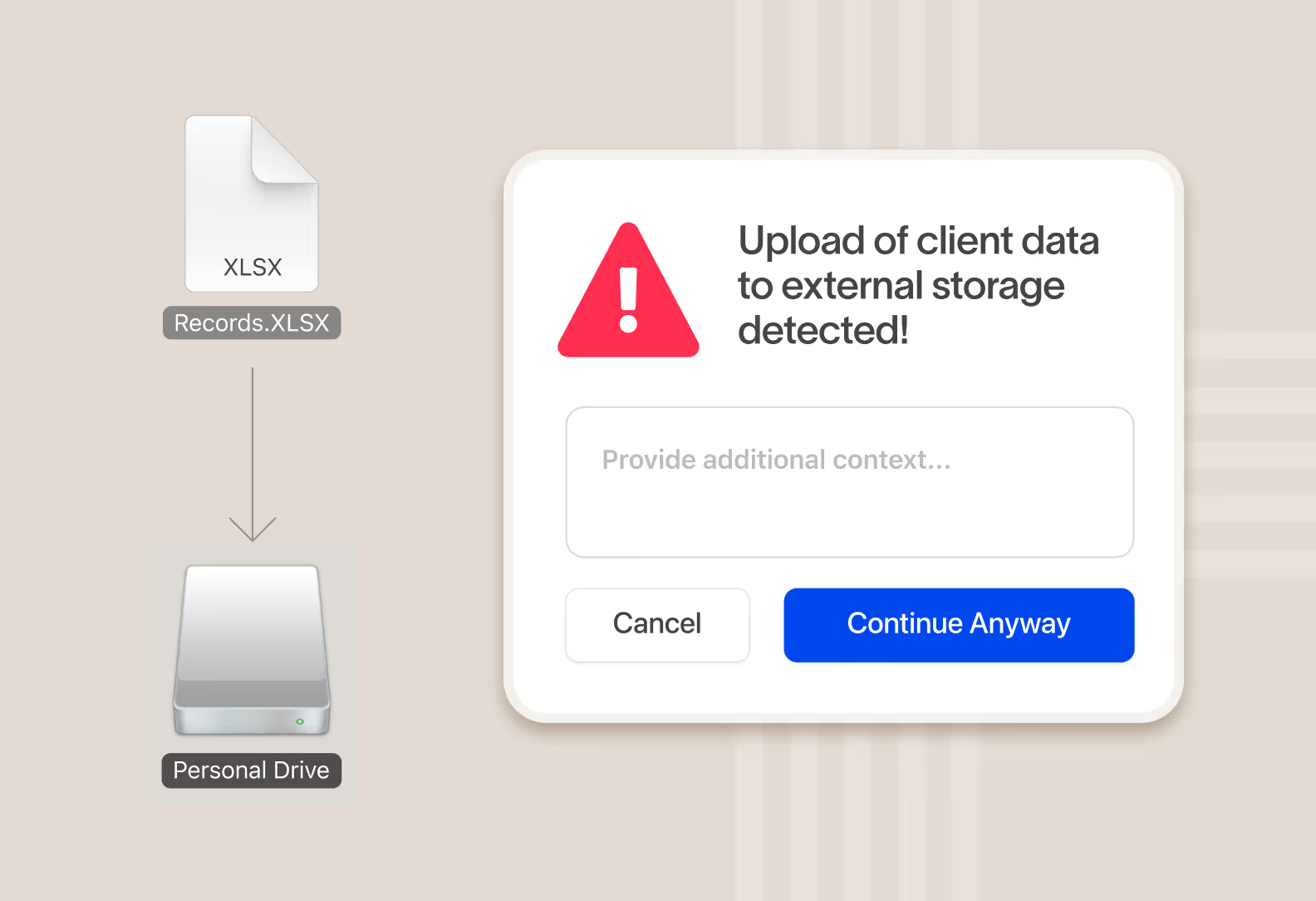
Stop risks as they happen
Take real-time action to protect data and educate users on the right behavior
When data is at risk of being exfiltrated, instantly take action and surface a message to the user educating them on company policy and acceptable behavior. An educated employee base leads to 80% fewer incidents and reduced risk to data over time.
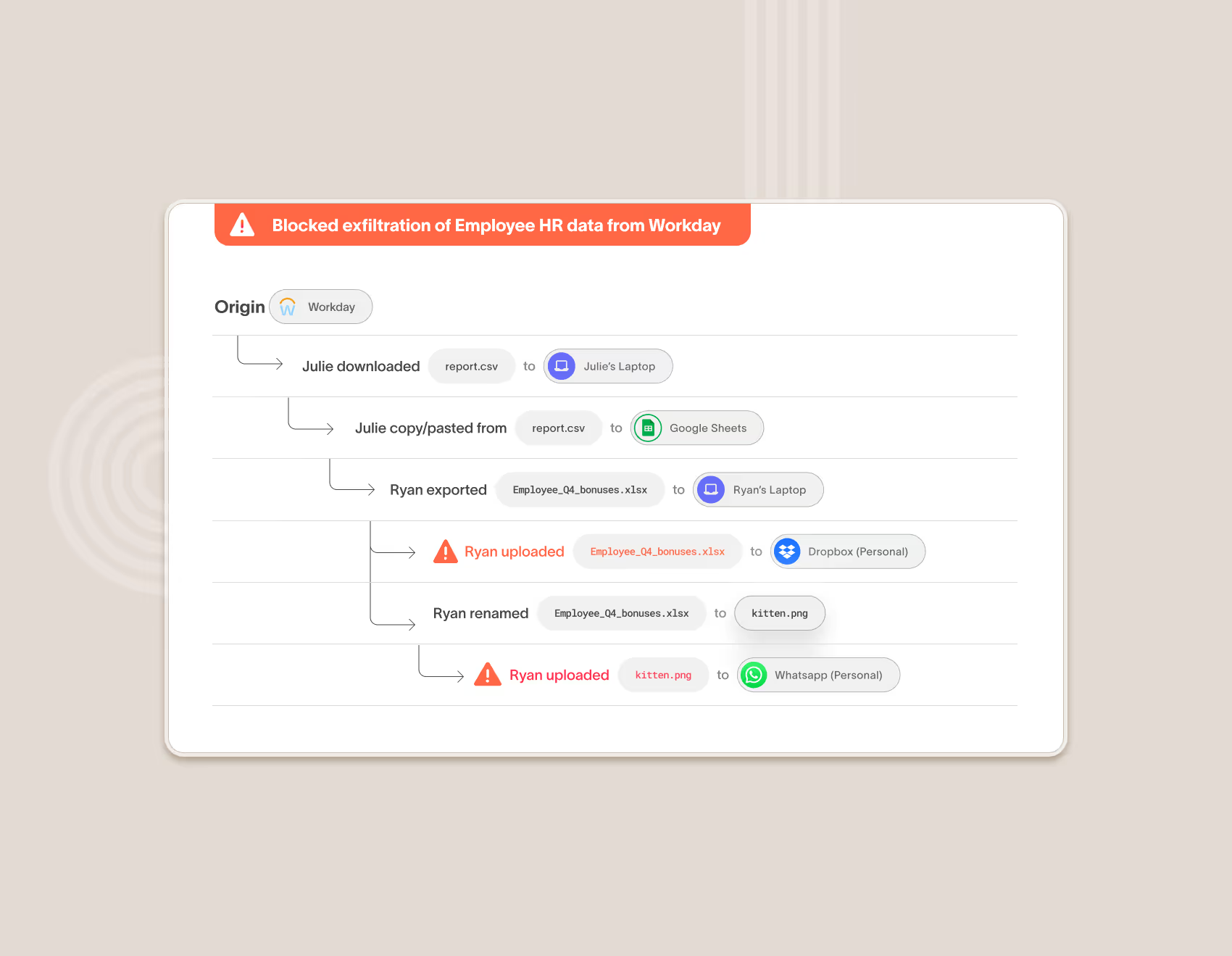
Get to the truth faster
Quickly investigate and understand user intent
Cyberhaven Incident Response provides a workflow to quickly investigate incidents with the full context of what happened to quickly understand user intent.
Forensic-level event collection without physical access to a device
Cyberhaven captures and displays events related to a user or a piece of data that until now has only been available with physical access to image a device.
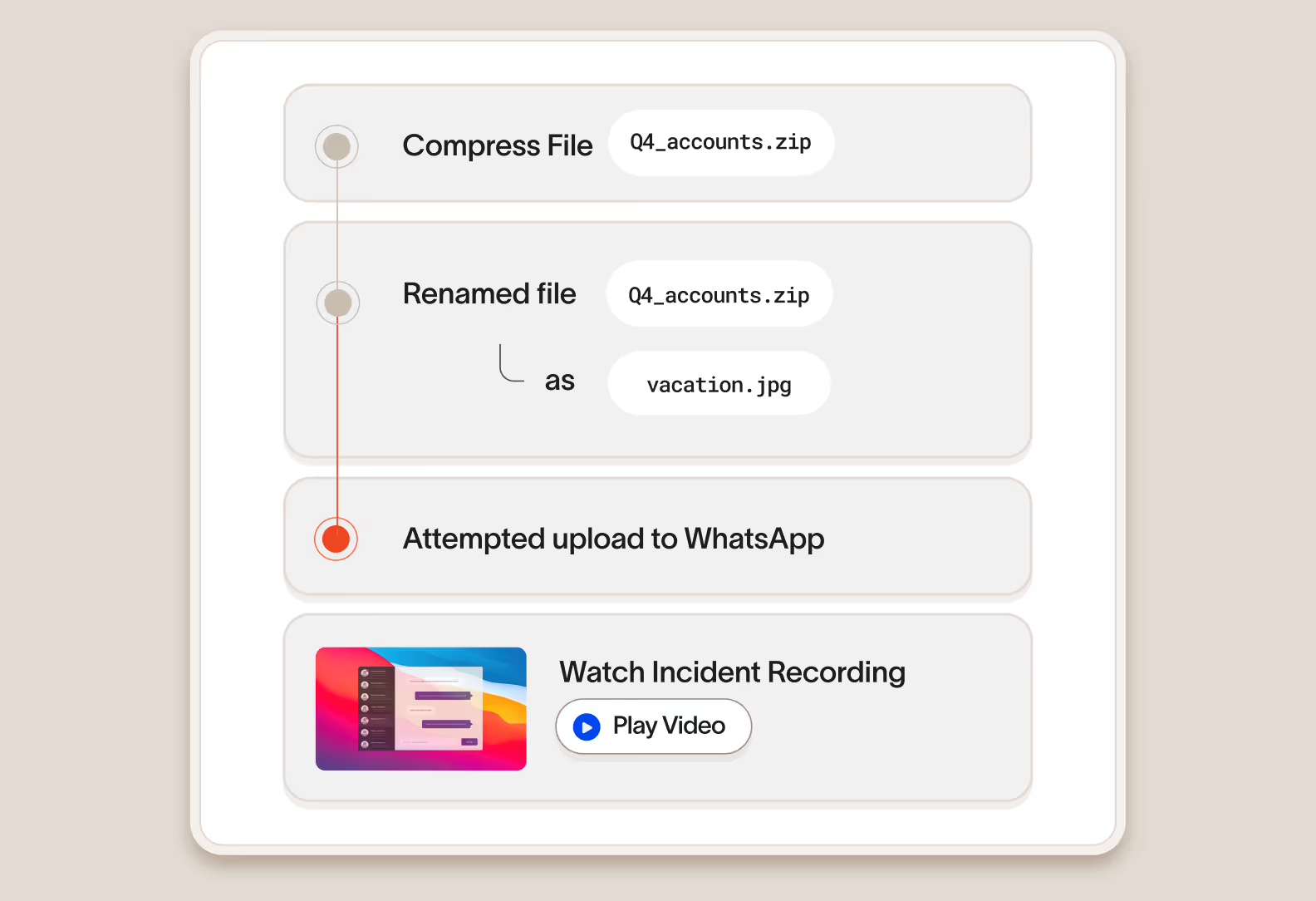
Screen capture and forensic file capture
Optionally, you can capture screenshots of a user’s device in the 30 seconds before an incident to better understand what happened along with the file itself to review its contents.
Review Cyberhaven incidents in your SIEM/SOAR or any third-party tool
Cyberhaven has native integration to SIEMs such as Splunk and also exposes incidents through an API so you can pull Cyberhaven incidents into any third-party security tool for review using your existing incident response workflow.
Works with your existing tools
Review Cyberhaven incidents in your
SIEM/SOAR or any third-party tool
Cyberhaven has native integration to SIEMs such as Splunk and also exposes incidents through an API so you can pull Cyberhaven incidents into any third-party security tool for review using your existing incident response workflow.








Unified visibility and enforcement
Cyberhaven AI & data security platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
