Accelerate internalinvestigations.
Quickly understand an incident to determine user intent with a complete record of events before and during an incident.
Incident view
See the full picture before
and after attempted exfiltration
Cyberhaven Data Detection and Response (DDR) provides analysts with the full history of events related to the data before, during, and after the incident.

An incident view with the context to understand what happened
Cyberhaven assembles the context that analysts need to quickly understand the incident across assets and across time.
The user's intent
One view that summarizes repeated attempts to exfiltrate the same data, changes to file extensions, and obfuscation attempts such as compressing in a ZIP file or encrypting data before exfiltration.
How they got a copy
Understand the journey the data took within the company including how the user got ahold of the data, revealing risks like incorrect permissions and oversharing.
Collusion with others
See patterns data transfers patterns between a user attempting to exfiltrate data and others within the company who may be working together to move sensitive data.
Incident replay
Replay the incident and
inspect the data being exfiltrated
Cyberhaven can optionally collect and present additional evidence to analysts to better understand what was happening during the incident.

Screen recordings
View what was happening on the user's device in the 30 seconds before an incident occurred to gain more context for an action.
Forensic file capture
Review a copy of the data involved in the incident. Customers can optionally store file evidence in their own cloud environment.
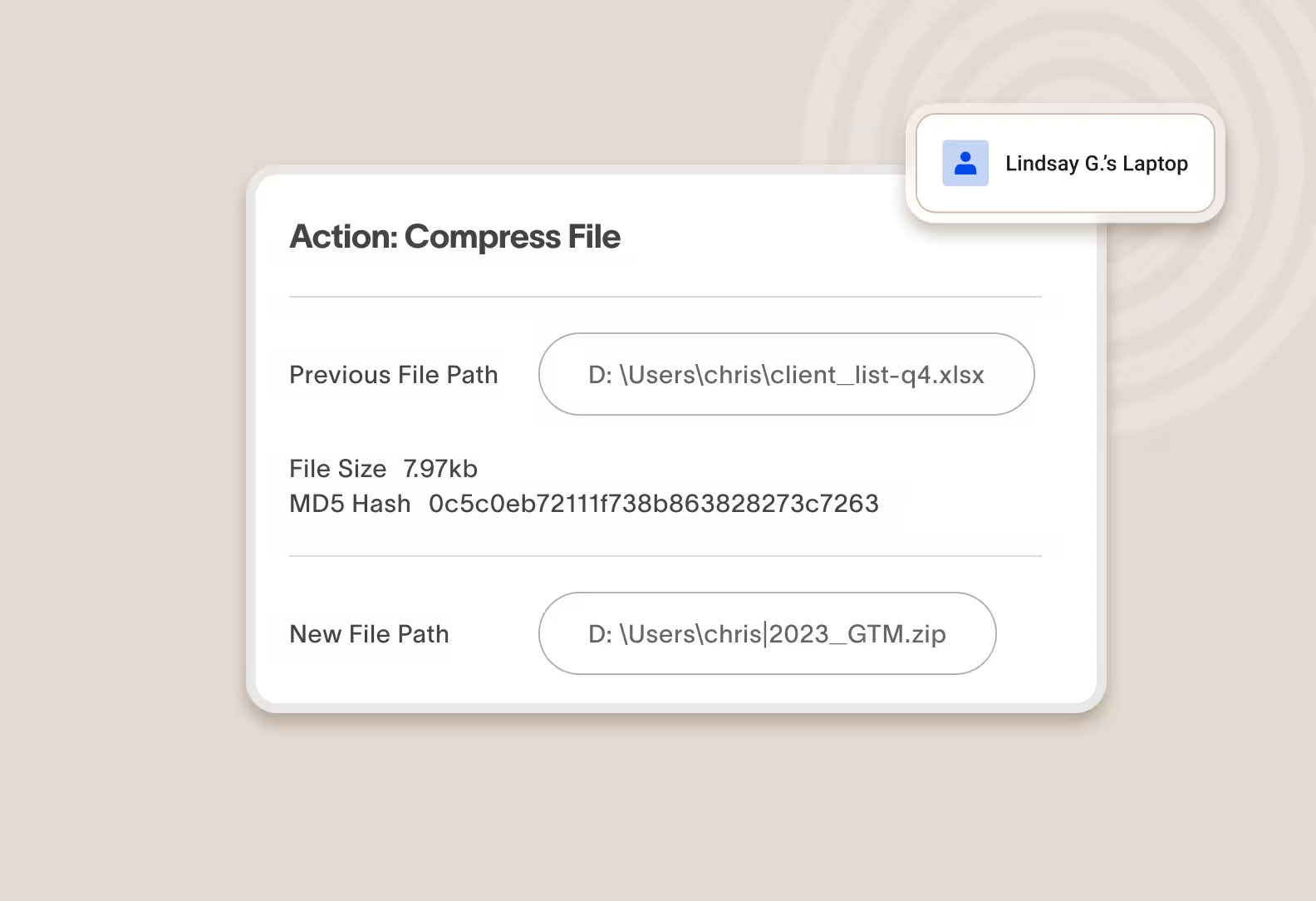
Forensically record user activity without physical access to a device
Cyberhaven captures every user action related to every piece of data and stores it securely in the cloud, so you can perform a post-incident forensic investigation without needing physical possession of a device.
Review Cyberhaven incidents in your SIEM/SOAR or any third-party tool
Cyberhaven has native integration to SIEMs such as Splunk and also exposes incidents through an API so you can pull Cyberhaven incidents into any third-party security tool for review using your existing incident response workflow.
What makes us different
Cyberhaven supports advanced investigation use cases like on one else
Unified visibility and enforcement
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.














.avif)
.avif)
