Data security for
today's cloud apps
Cyberhaven delivers cloud security built for the way apps work today and follows data to protect it after it leaves the cloud.
Beyond Traditional Security
The limits of CASB and SSE tools
Cloud Access Security Brokers (CASB) and Security Service Edge (SSE) products were designed using network technology that doesn’t work with new forms of encryption and they don’t protect data outside the cloud.
Is blind to data loss via apps with new encryption
More and more cloud apps use end-to-end encryption and certificate pinning, making it impossible for network-based cloud security products to see what data is going to them.
Cannot protect data after it leaves the cloud
Cloud security products can no longer see what happens to data after it leaves the cloud to a device or stop someone from taking it via email, USB storage, AirDrop, etc.
Uses separate policies from other data security tools
Many cloud security products were only built to solve cloud use cases, so they often have separate policy engines that are not well integrated with data loss prevention products.
Next-Generation Cloud Protection
Cyberhaven redefines cloud data security
We stop data loss via cloud apps that traditional cloud security tools can’t, and we follow and protect data even after it leaves the cloud.
Prevent data from going to encrypted apps that circumvent network controls
SWGs and CASBs can’t decrypt traffic to cloud apps that use end-to-end encryption or certificate pinning. We stop data exfiltration to these apps before data is encrypted and sent.
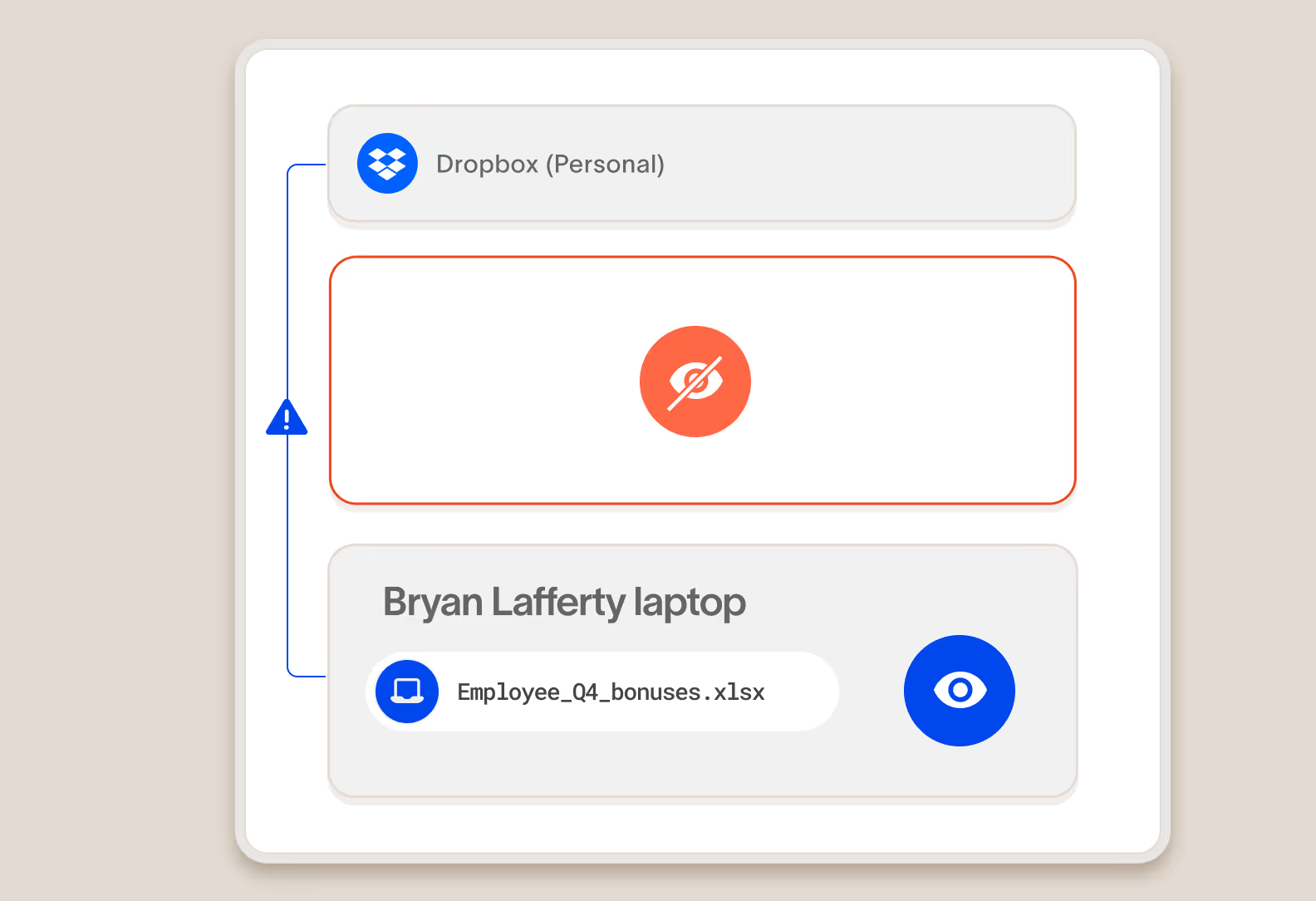
Protect important data as it moves from the cloud to devices, and between clouds
It’s not enough to protect data in the cloud, you also need to protect it when employees move it to devices, transform it, and it moves to other clouds. Cyberhaven follows the data everywhere in your extended enterprise to protect it.
Real-time action
Take real-time action to protect data and
educate users on the right behavior
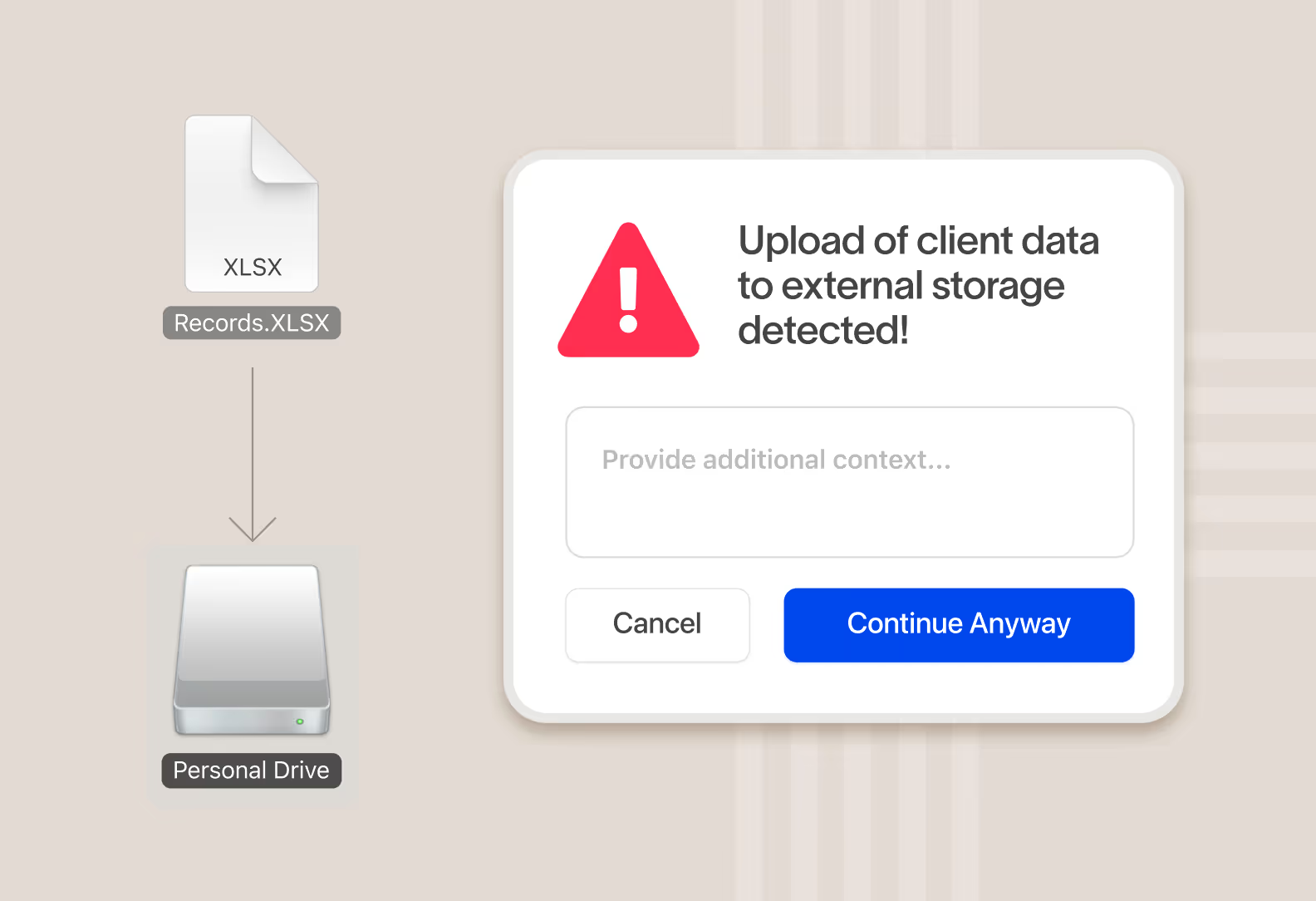
When data is at risk of being exfiltrated, instantly take action and surface a message to the user educating them on company policy and acceptable behavior. Real-time popups are more effective at coaching users than out-of-band email notifications.
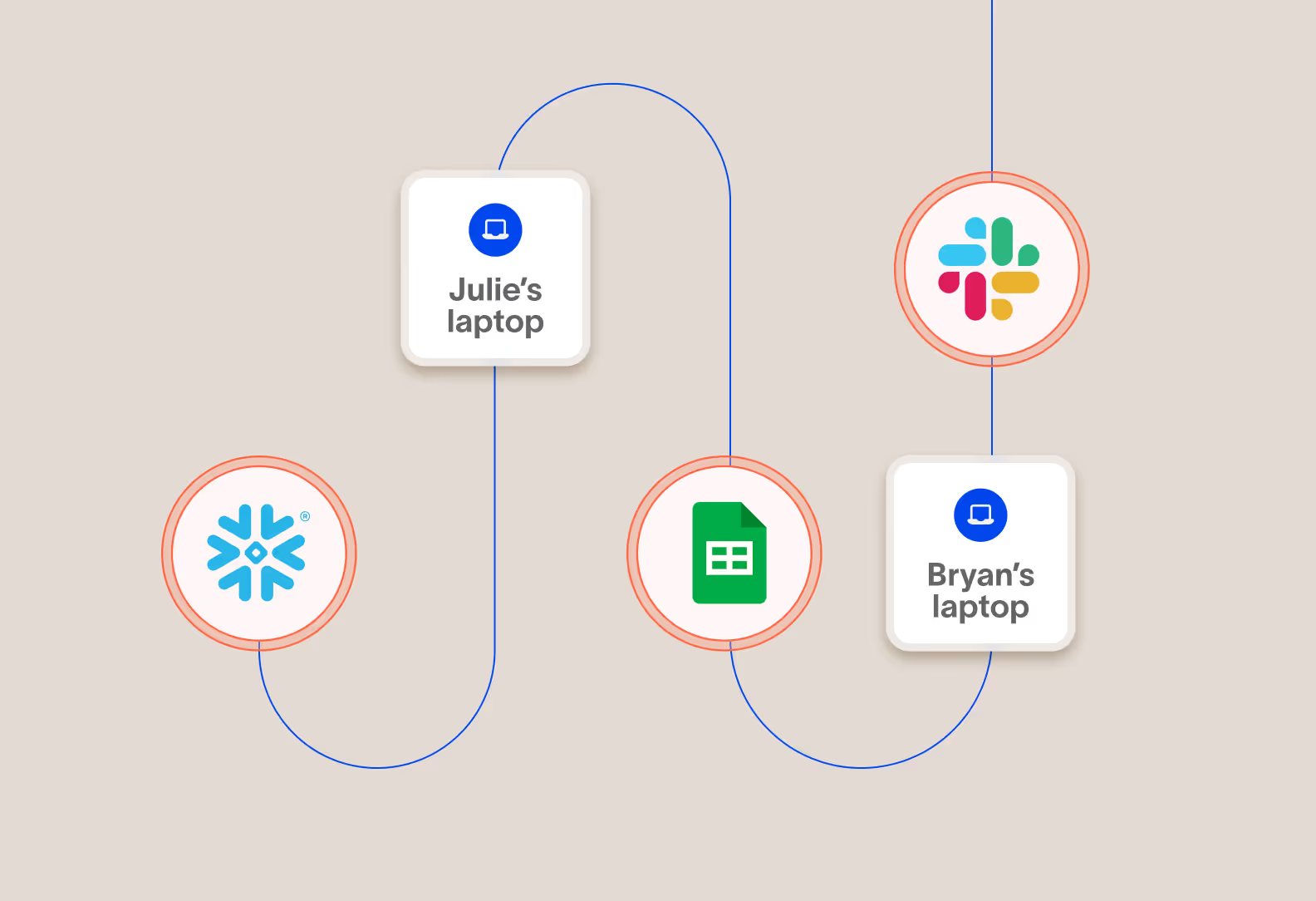
Prevent risky sharing of data in corporate cloud apps to the wrong people
Sharing and collaboration apps make it incredibly easy for employees to work together, but they also make it easy to share with the wrong people or give people the wrong permissions. Cyberhaven enforces sharing policies in real time to prevent data from leaving your control.
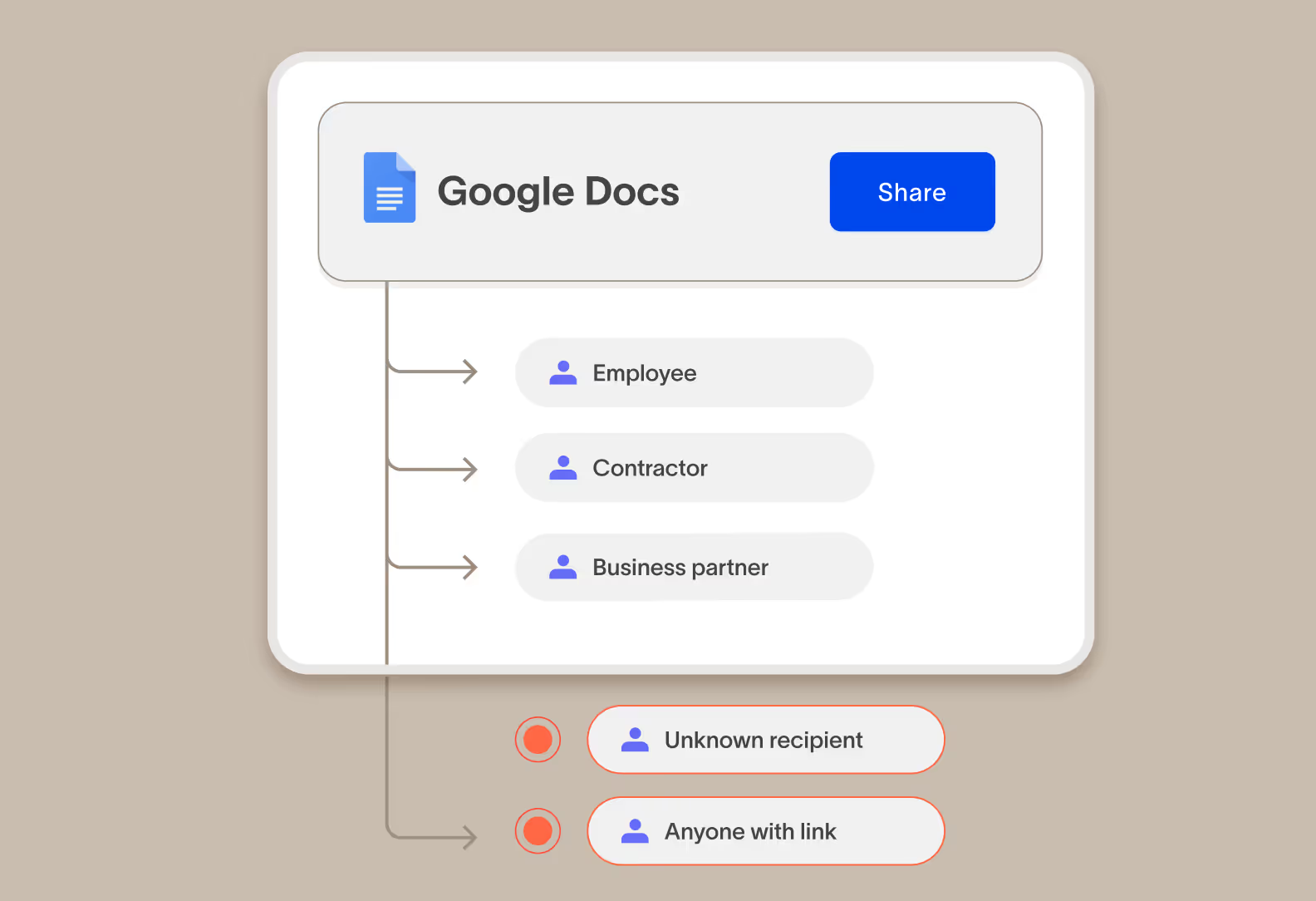
Allow important data in corporate instances of an app but not personal instances
Cyberhaven stops important company data from going to personal cloud apps, and we can tell the difference between a corporate instance of an app and a personal instance of the same app that’s not approved to store company data.
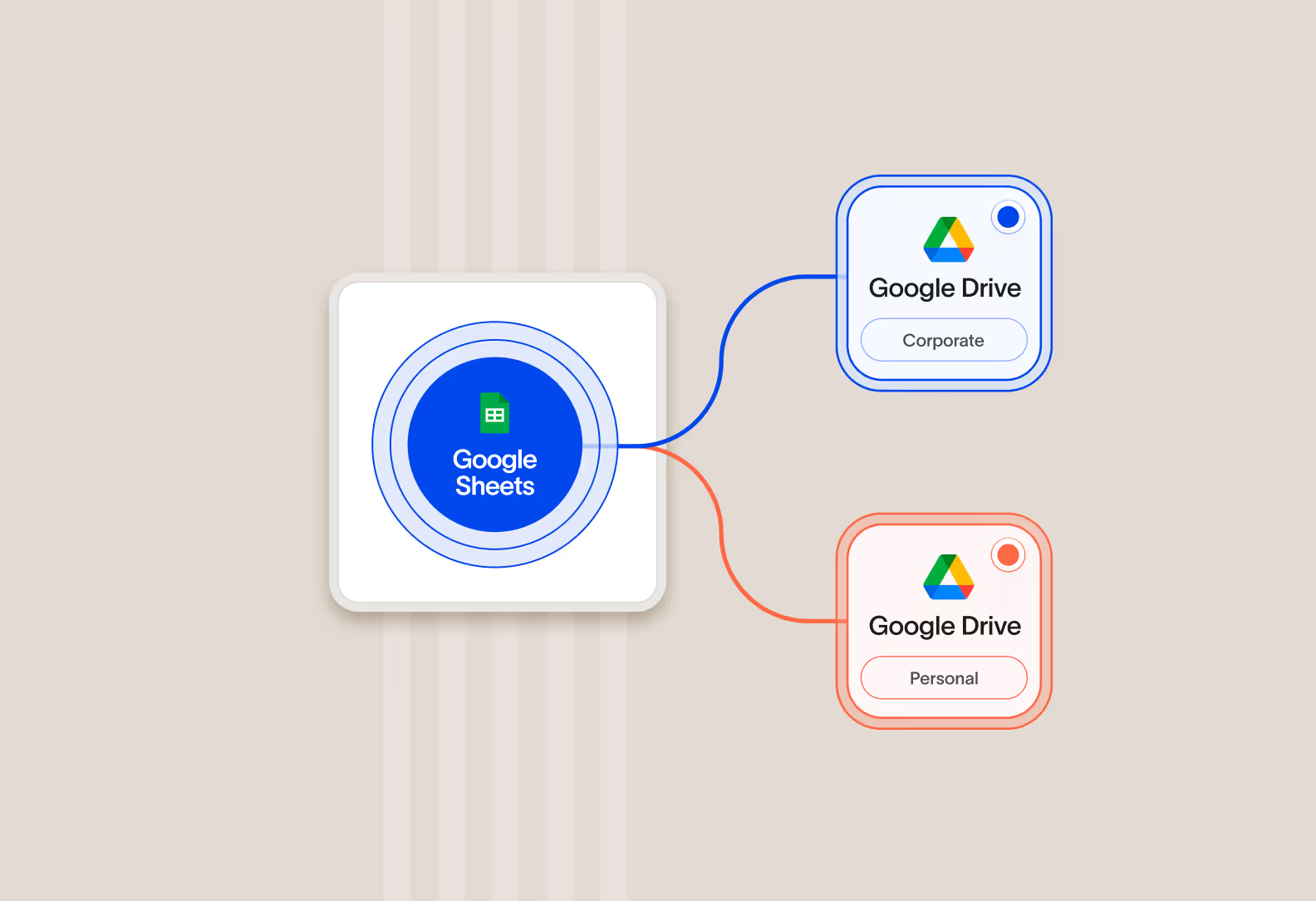
Discover new cloud apps and data stores employees are using
Cyberhaven detects and tracks usage of new cloud apps employees try to use with company data. You can enforce policies to protect data, redirect employees to approved alternatives, and identify unmet needs for new apps.
Everything else you expect from a cloud security solution
When we set out to redefine cloud data security, we included the standard features you expect.
Shared link protection
Ensure sensitive data remains confidential by preventing the creation of shared links with overly broad permissions.
Collaboration control
Manage data access seamlessly by setting permissions for internal, external, and other groups, ensuring data integrity and security.
Inline data protection
Maintain real-time vigilance with continuous scanning of data as it transfers to and from cloud applications, ensuring immediate threat detection and response.
Out-of-the-box policy templates
Get started quickly with dozens of out of the box policies for common use cases and industry-specific requirements.
Standard and custom content identifiers
Includes content identifiers for common PII, PCI, and PHI patterns, standard keyword lists, or create your own identifier with custom RegEx.
User directory integration
Integrates with on-premises and cloud-based directory services to support granular user group and department based policies.
Role-based access control
Includes standard out-of-the-box roles or create your own custom roles with any combination of permissions.
Reporting and analytics
Includes out-of-the box dashboards and a fully customizable reporting engine for advanced analytics.
SIEM integration and APIs
Natively integrates to SIEM tools such as Splunk and exposes incidents through an API so you can add them to any third-party security tool.
Unified visibility and enforcement
Cyberhaven AI & data security platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
