Detect and stop riskybehavior.
Instantly detect when a user handles important data in a risky way and stop them in real time while coaching them.
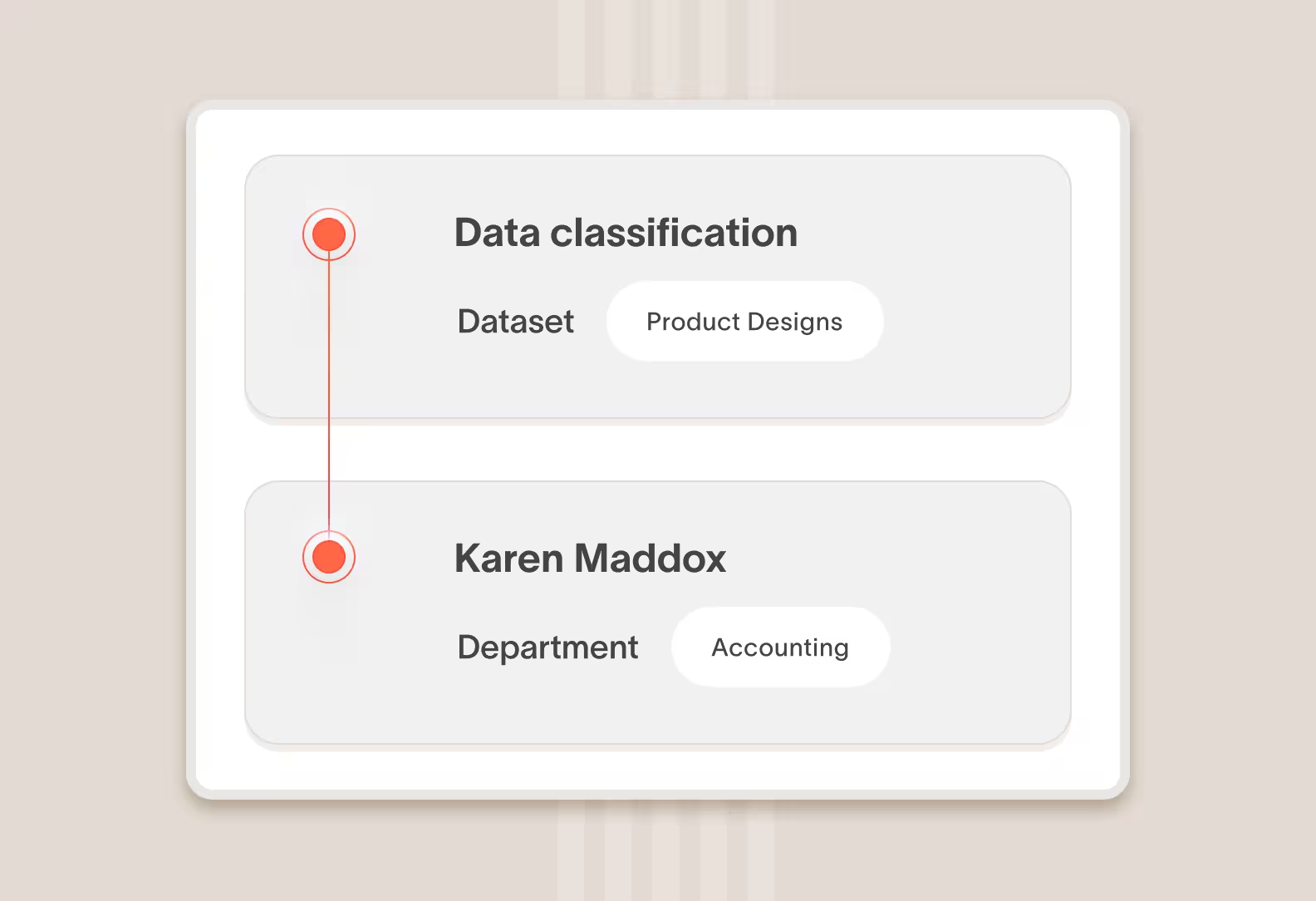
Behavior + Data classification
Accurately identify high-risk behavior involving sensitive data
Unusual behavior, like high upload volumes, can be indicative of suspicious behavior or be totally harmless. Cyberhaven looks at behavior in combination with what type of data is being handled to more accurately detect insider risks.
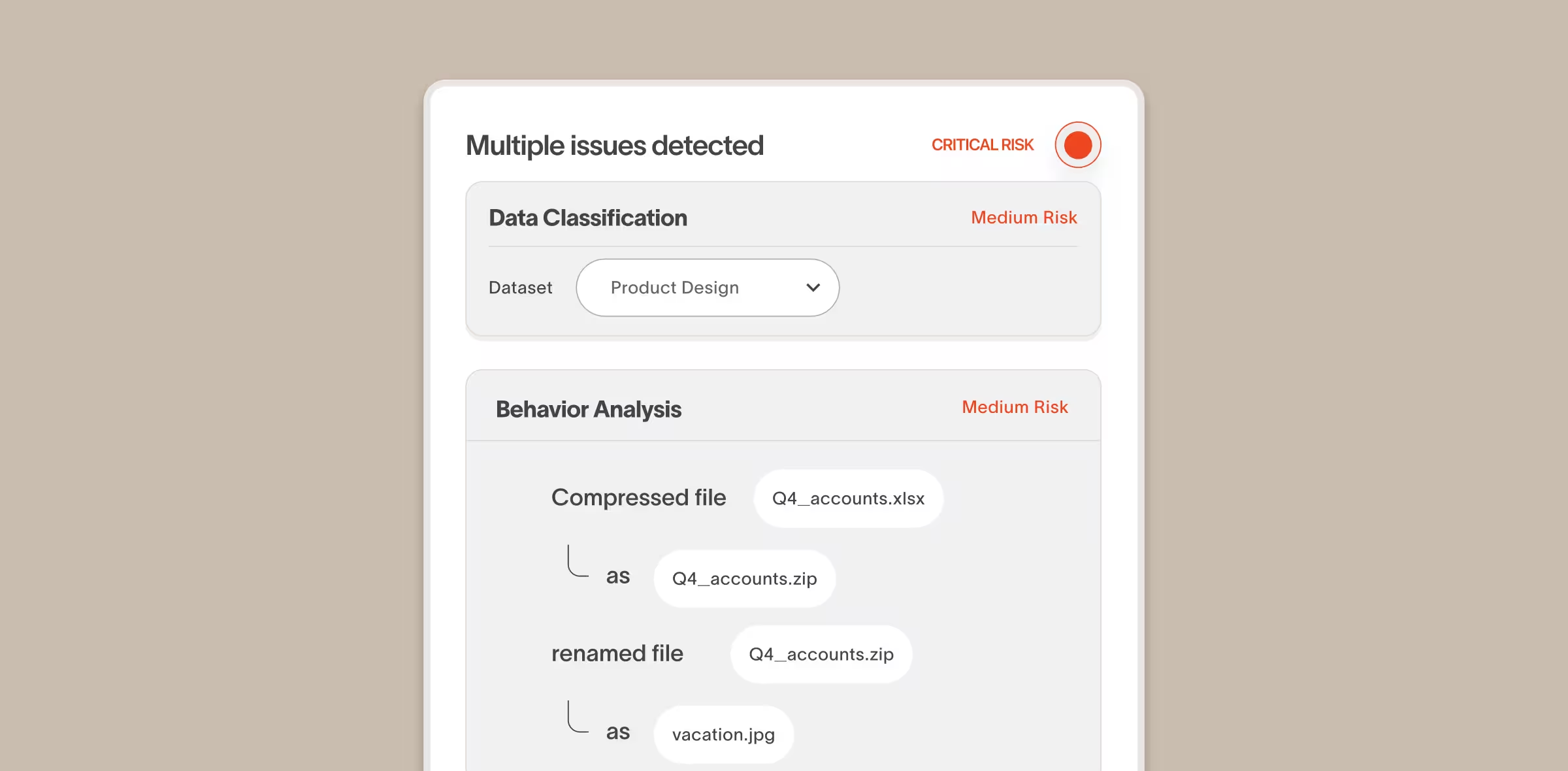
Tiered response
Automatically take action the moment an insider risk is detected
Cyberhaven takes instant, automated remediation action to stop risky behavior and coach users. The product has a full range of remediation options that can be tailored based on risk and data sensitivity.
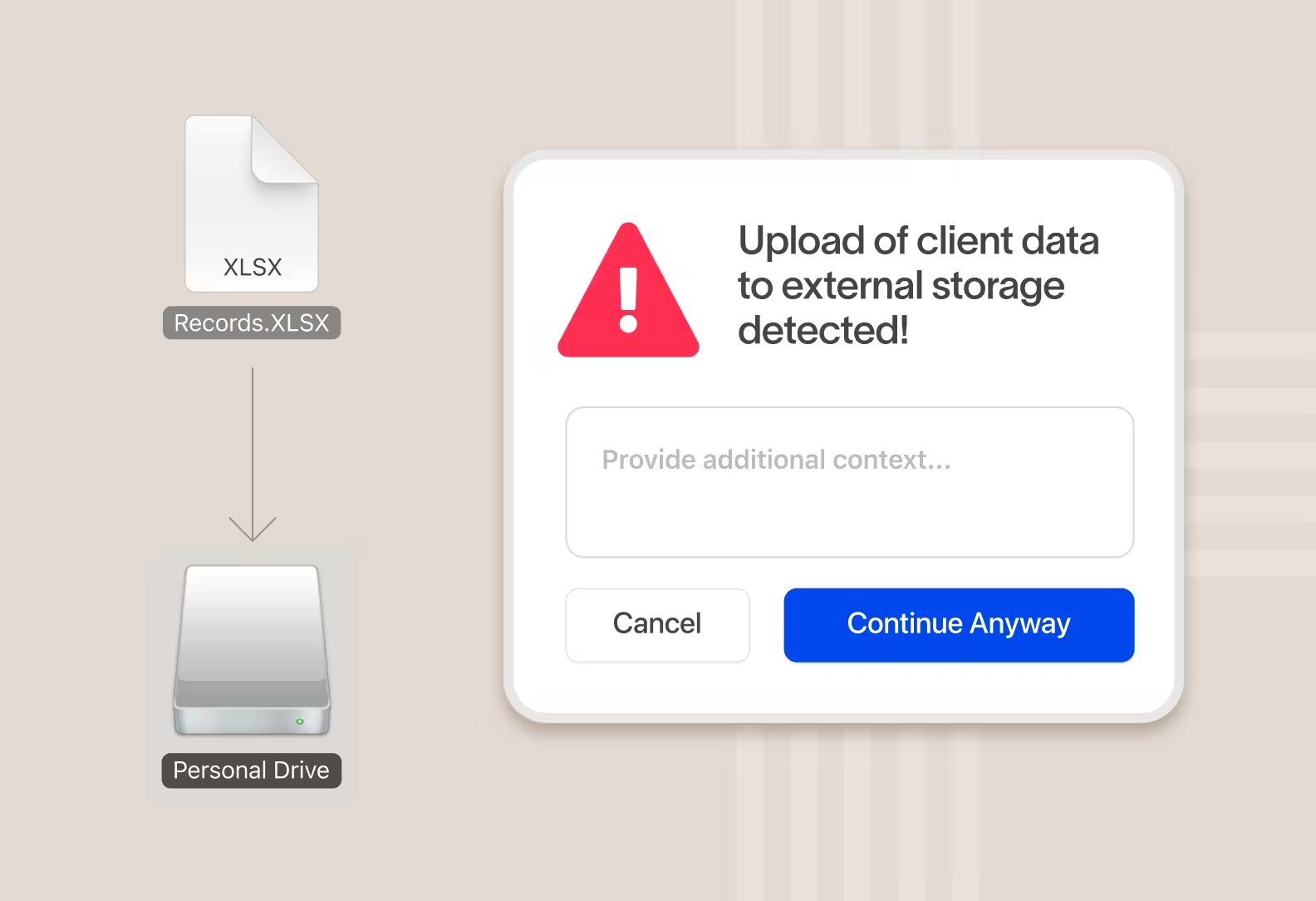
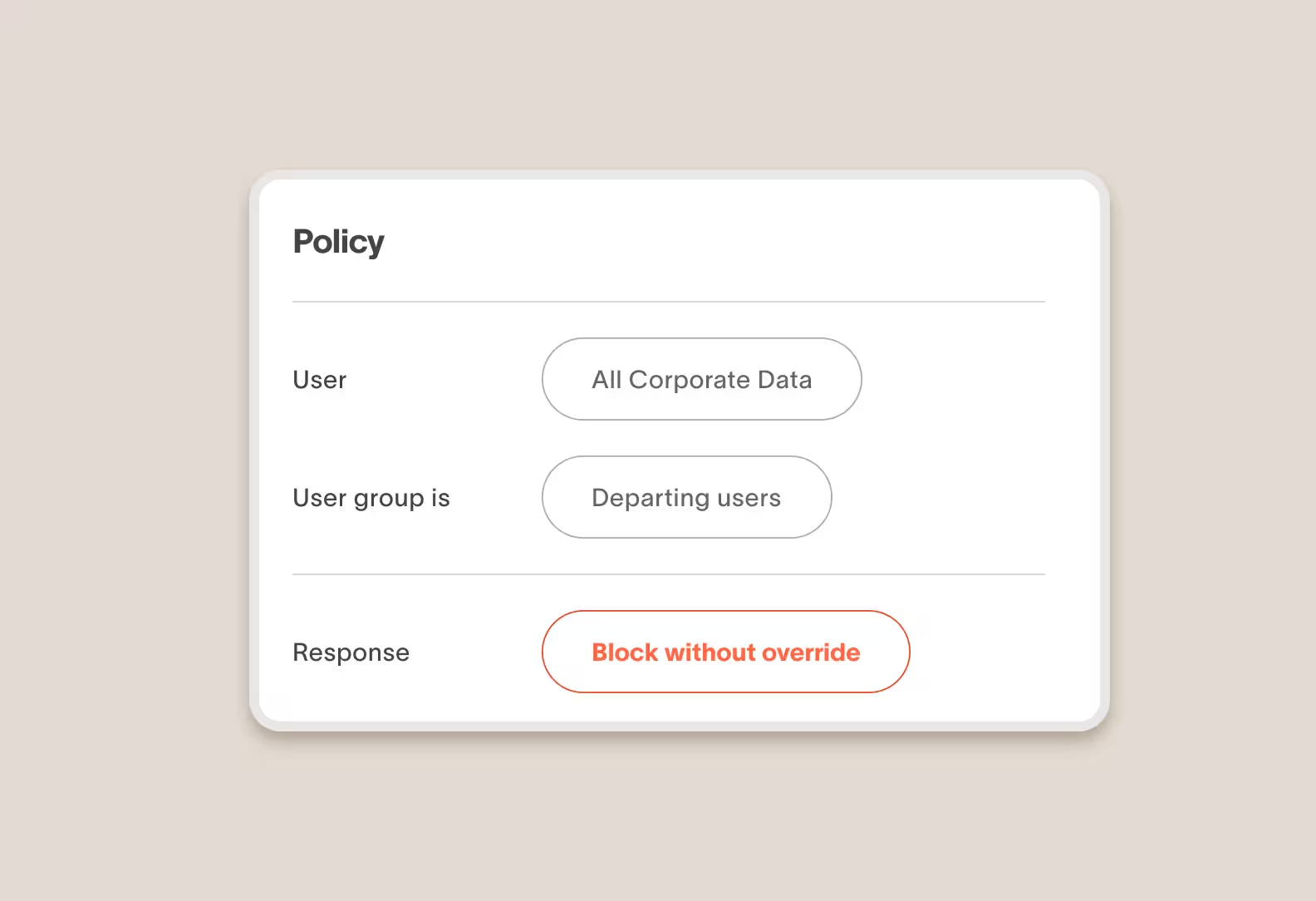
Block, with optional user override
Cyberhaven can block a risk action outright in real-time. Optionally, you can give the user the ability to override and continue by providing a business justification.
Coach users but don't block
Cyberhaven policies can also be used to coach users without stopping them, in cases where the risk or data sensitivity may not be high enough to intervene.
Silently alert security to investigate
Rather than disturbing the workflow of an employee, you can also configure policies to trigger an alert that can be investigated within Cyberhaven or your SIEM/SOAR.
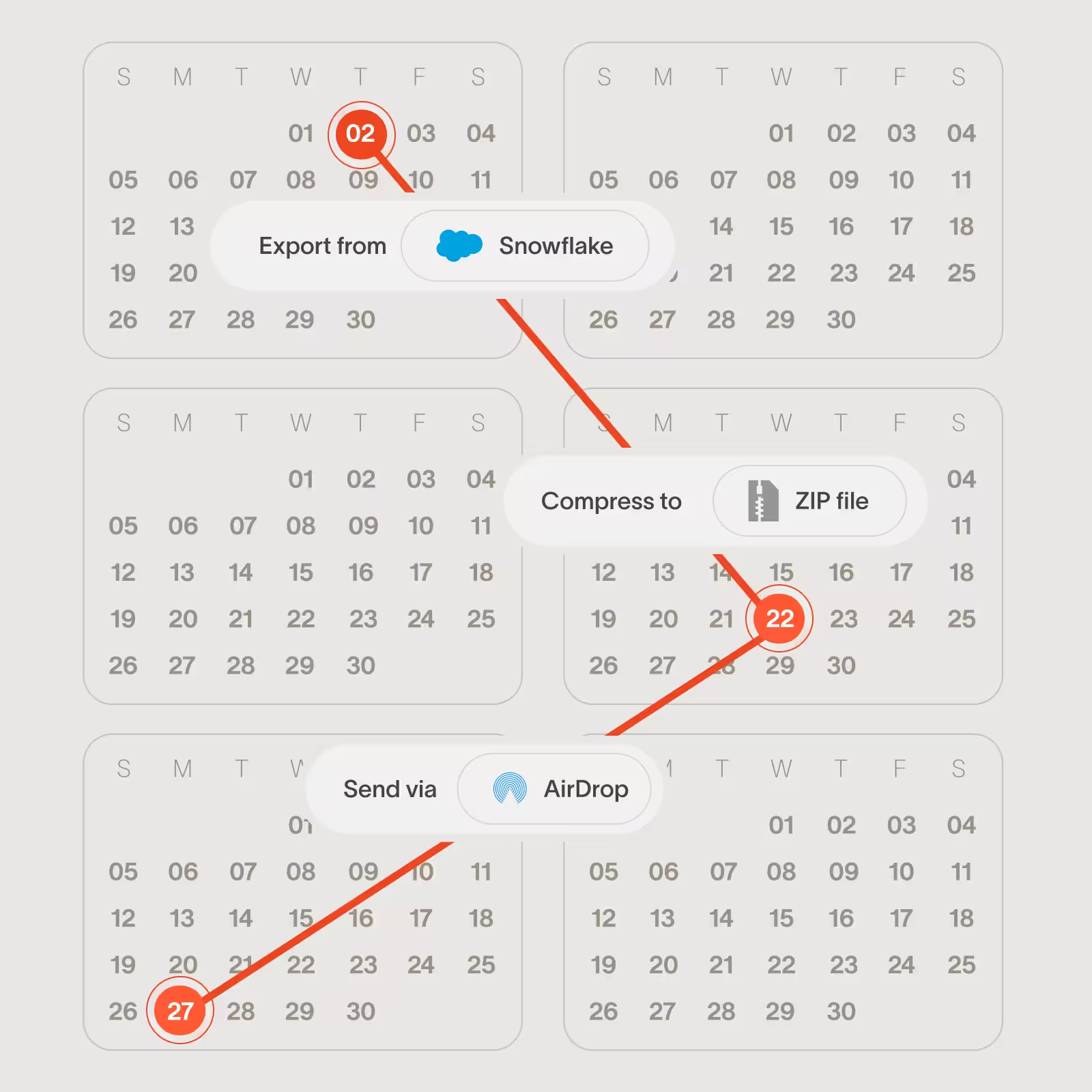
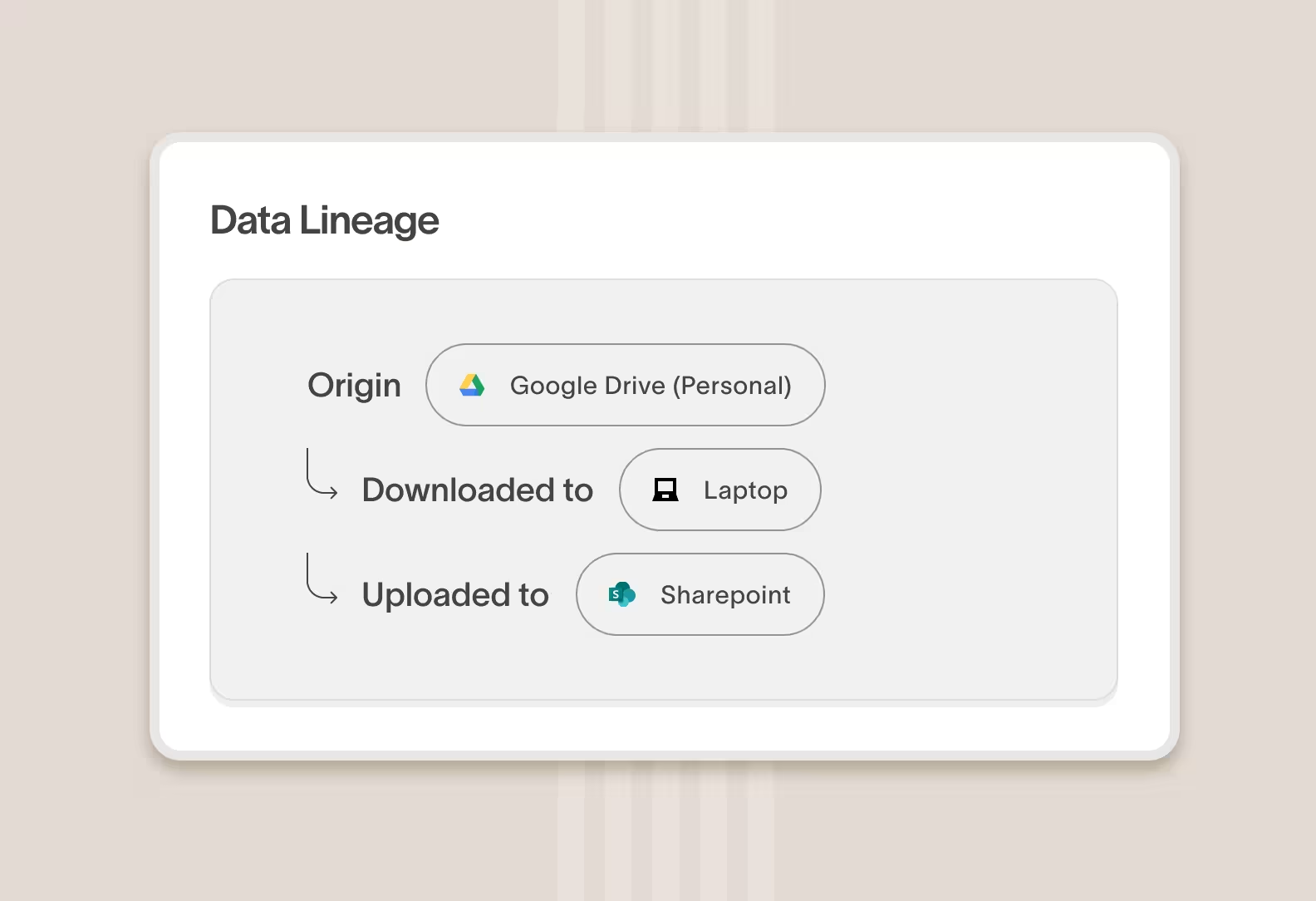
Identify insider risks that unfold over weeks or months, not just hours
Cyberhaven stores a record of events indefinitely and the product can correlate events and detect risk patterns occurring weeks or months apart, which is how many incidents happen in the real world.
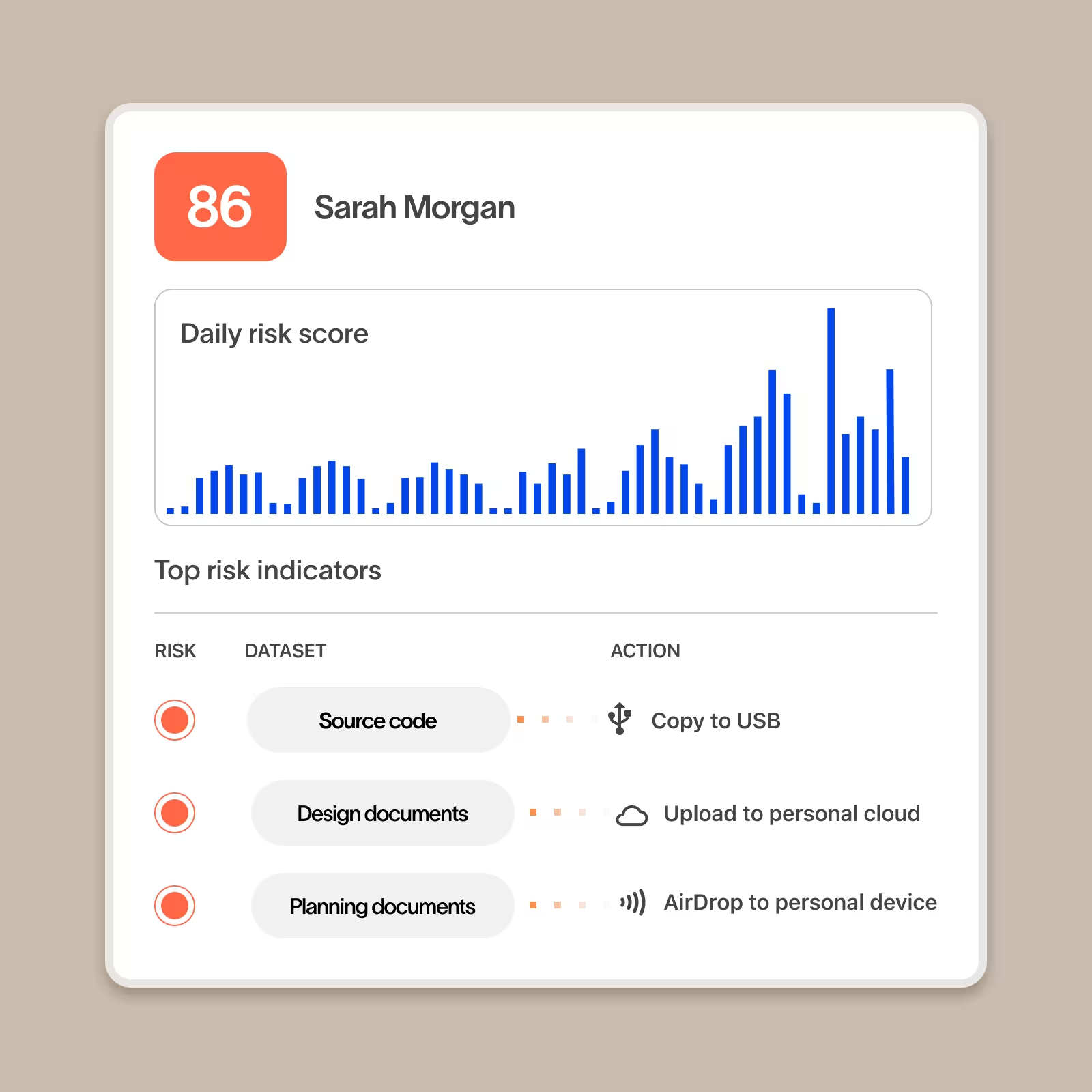
User risk scores that incorporate data sensitivity, not just behavior
Cyberhaven scores users not just on the actions they take but also what type of data is impacted. Risk scores also incorporate details about the user including watchlist membership and risk groups based on factors such as employee performance for a complete picture of a user’s risk.
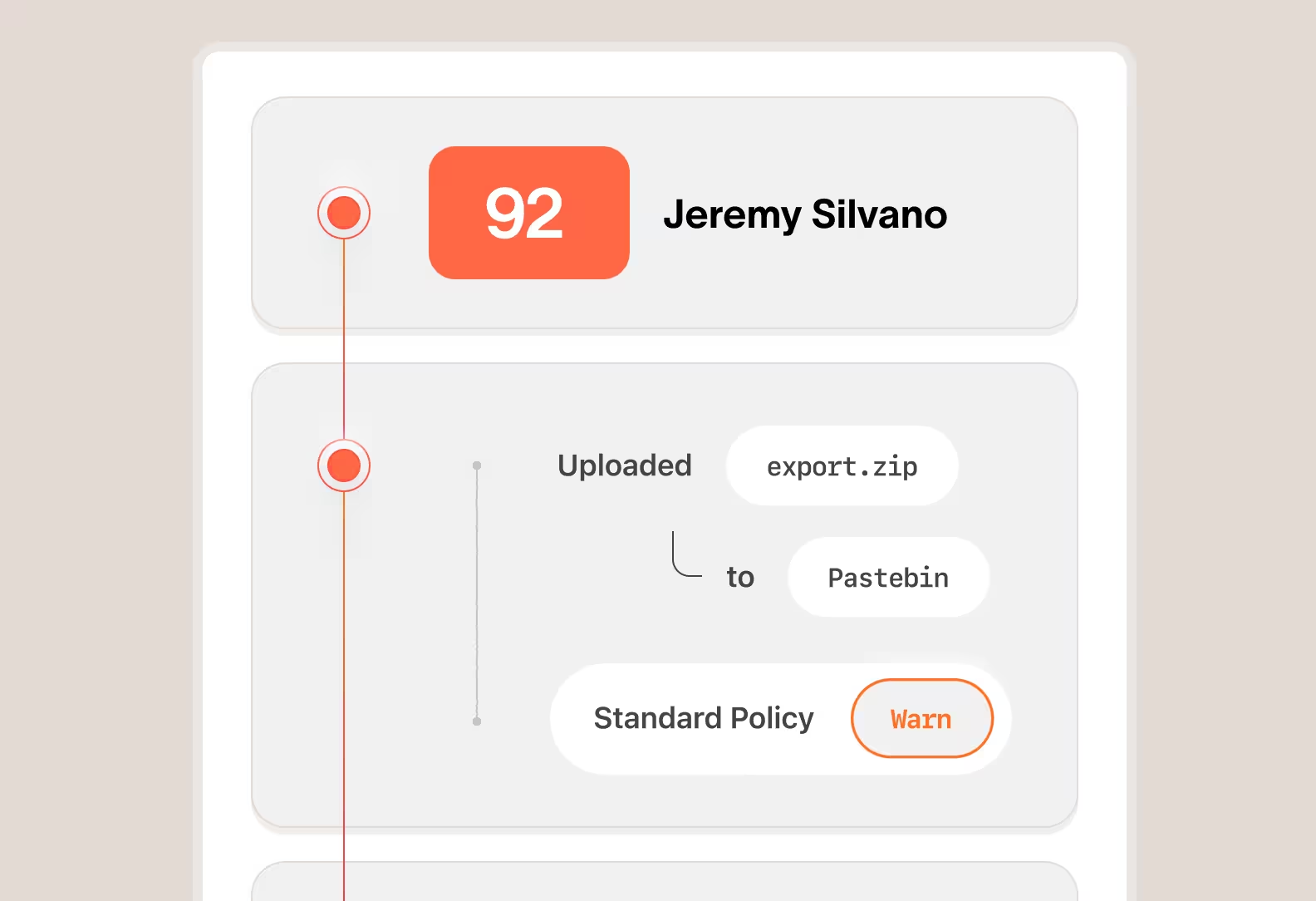
Stepped up response actions for users with a history of risky activity
With Cyberhaven, you can add users with a history of risky behavior to a user group that has elevated remediation. Instead of responding based on the risk of a single incident, the product will apply elevated remediation such as blocking the risky action instead of just warning the user.
Solution section
Solving the data security problem
Unified visibility and enforcement
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
