Stop data exfiltrationanywhere.
Block important data from leaving your control via cloud, web, email, removable storage, and more
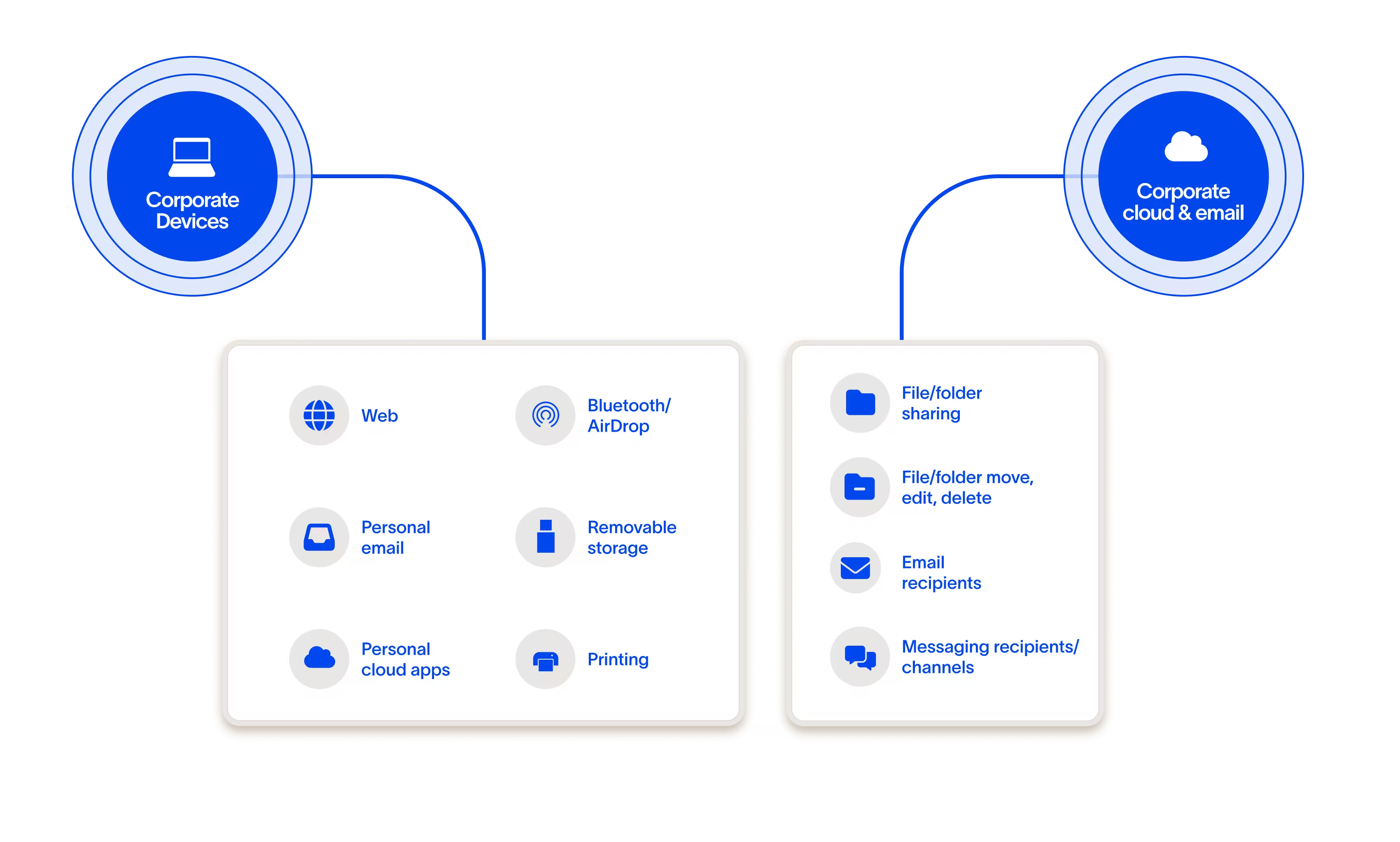
Complete coverage
One product to protect data across every exfiltration channel
Cyberhaven Data Detection and Response (DDR). makes it possible to stop exfiltration across all channels with one product and one set of policies
Data lineage
Go beyond content inspection to more accurately classify data
Content alone isn’t the full picture. The product analyzes content patterns along with the entire lineage of a piece of data to better classify and protect it.
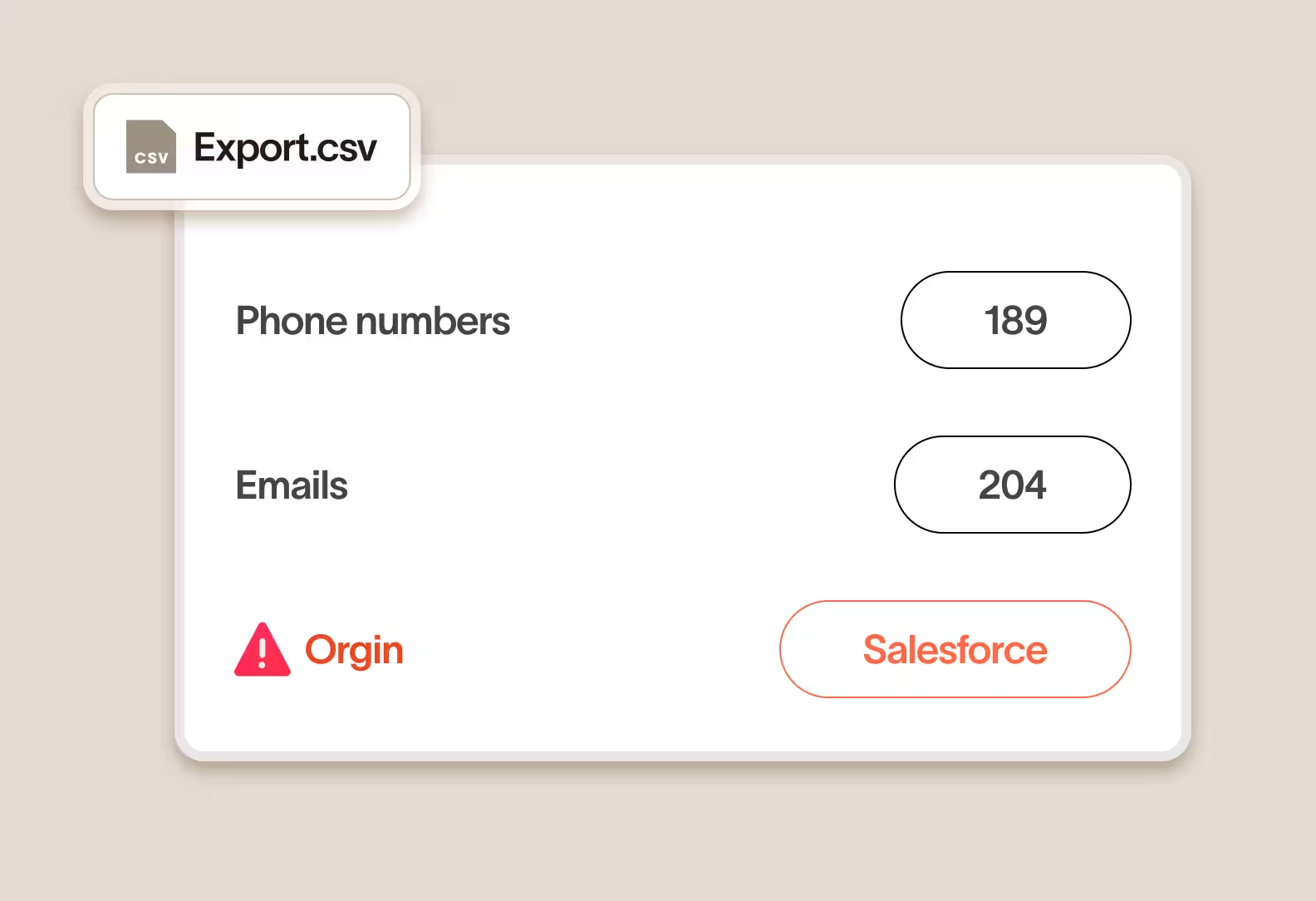
Classify any type of sensitive data
Cyberhaven classifies any type of data, even without a content pattern (for example, credit card numbers) or any text content at all.
Reduce false positives by 95%
Data lineage removes false positives created by common content patterns by layering in additional context.

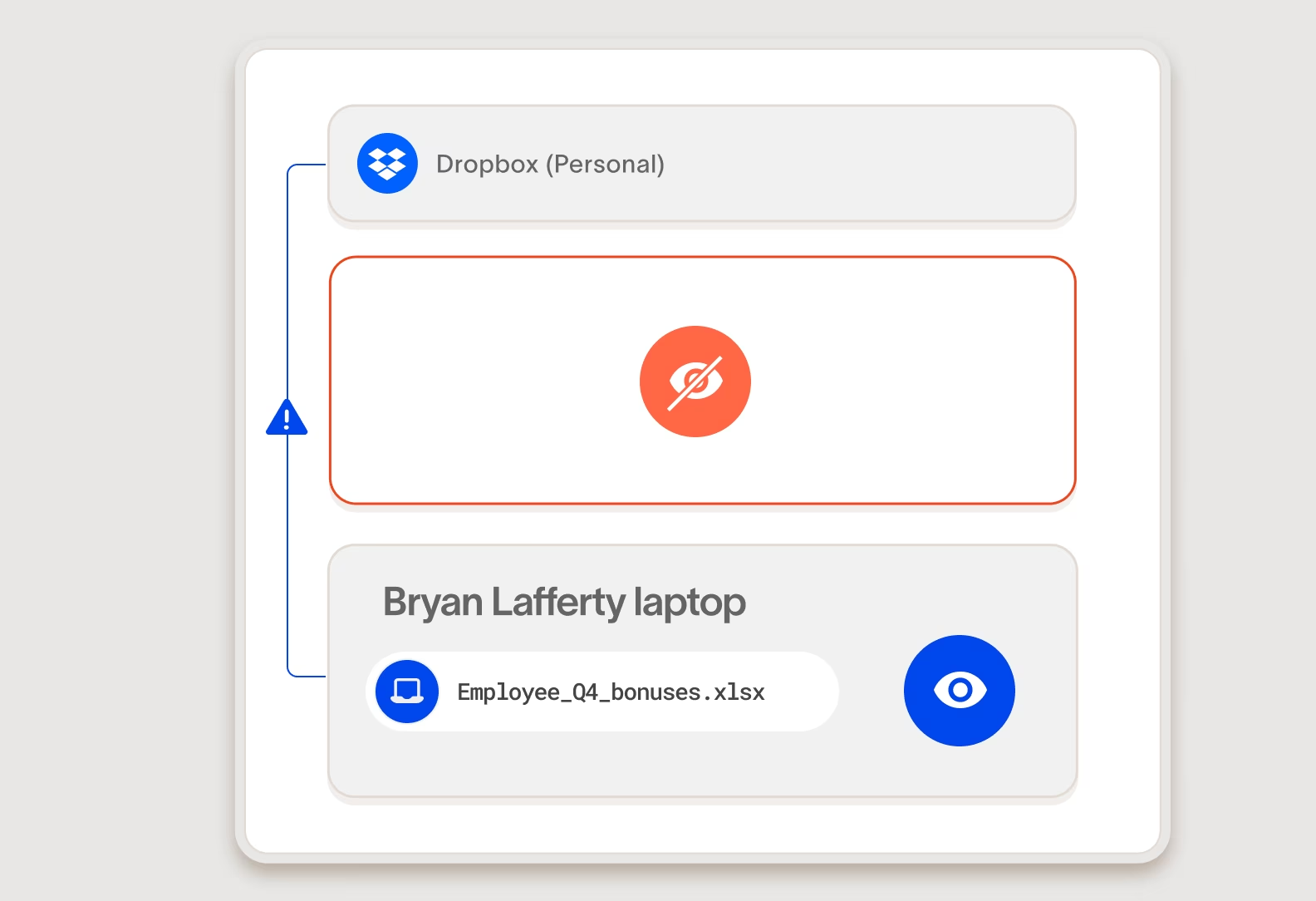
Control data movement at the most granular level
Many data security products focus on data in files. They scan content in files and apply tags/labels to files. Cyberhaven tracks and protects every piece of sensitive data, even as it's copied between files or apps where traditional tools lose track of it.
.avif)
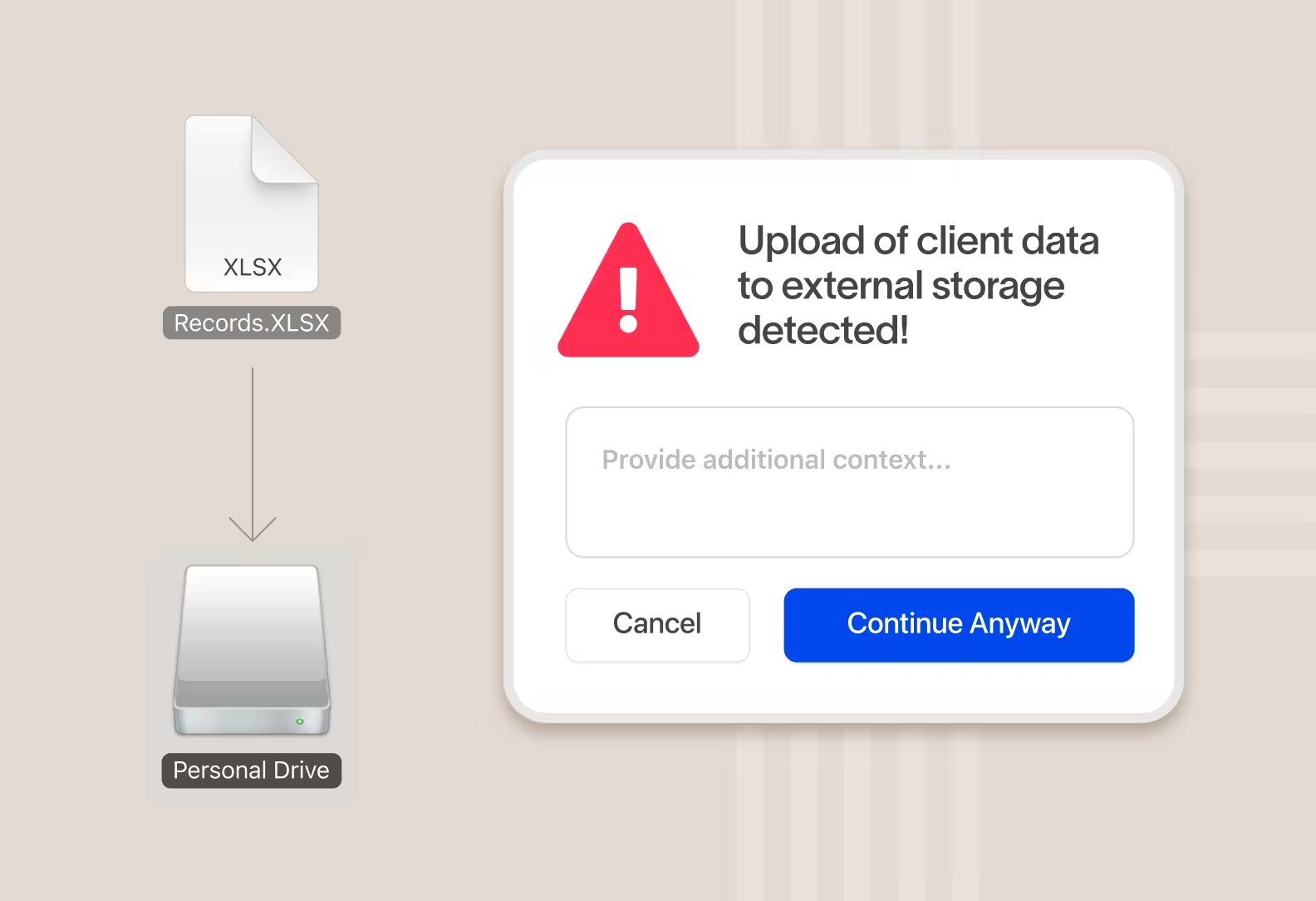
Protect data obscured by encryption and compression
Cyberhaven tracks what type of data was encrypted or compressed, so even after the data itself cannot be scanned you can track it and protect it from exfiltration
Control usage of certificate pinned and end-to-end encrypted applications
Certificate pinning and end-to-end encryption are two advances in network security that have rendered CASB and web proxy approaches to data security completely ineffective on commonly used applications like Dropbox and Whatsapp. DDR enforces controls on the device itself , protecting data before visibility is lost.
Solution section
Solving the data security problem

Unified visibility and enforcement
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
