Detecting insider risks isn't enough. Stop them.
Cyberhaven combines data awareness and behavioral signals to detect and stop insider threats and protect important data.
Why traditional IRM isn't cutting it
The limits of traditional insider risk management
Until now, insider risk products have taken a passive approach – they alert you to threats but don’t stop them, and too many of their alerts are false positives.
Only analyzes behavior, not the data being handled
IRM tools look at behavior but can’t connect it to what data is being handled or events across time. They generate alerts for things that aren’t risky while missing many actual insider threats.
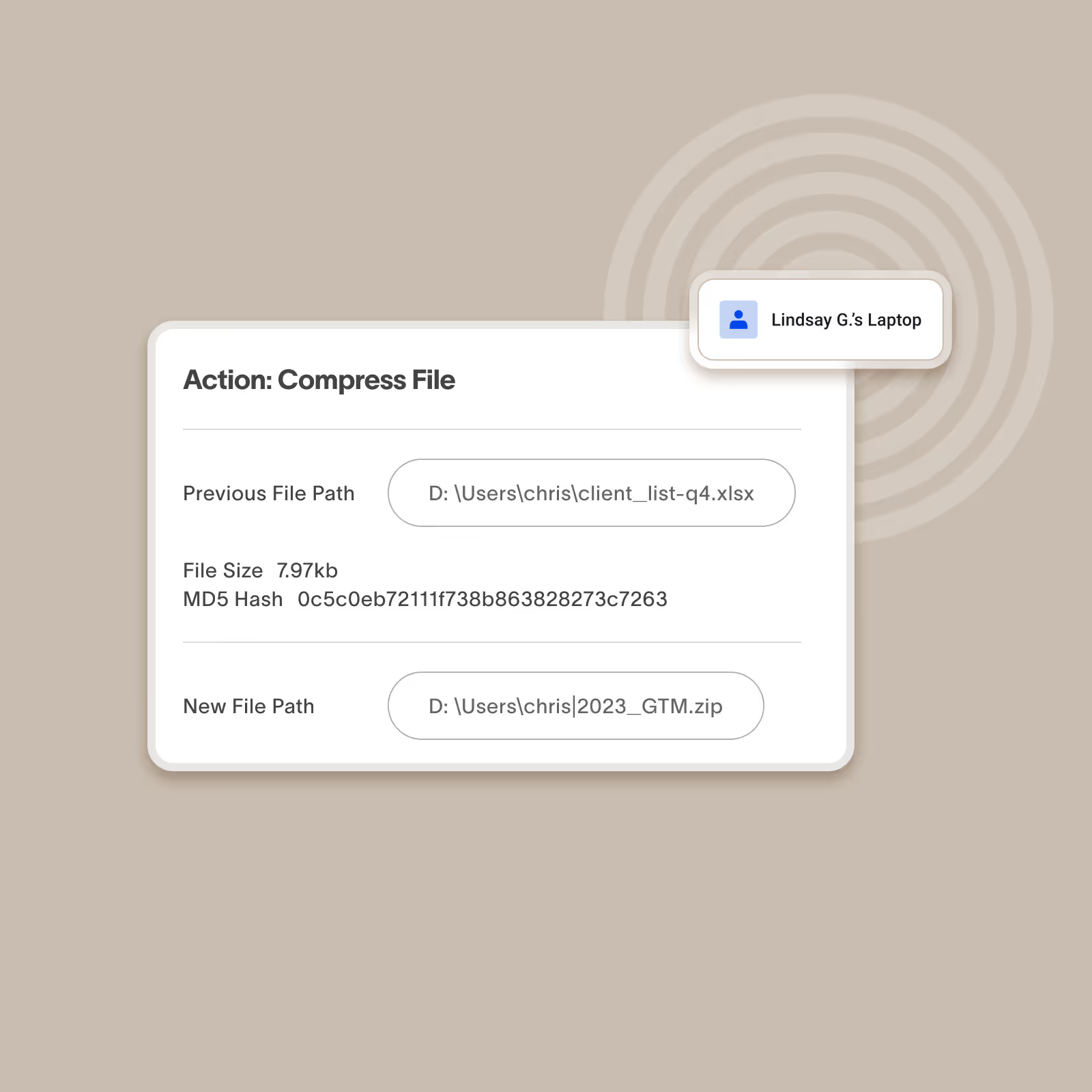
Cannot intervene and stop data from leaving
When IRM tools detect a user mishandling data, they only send an alert. They’re designed to ingest event logs and analyze them but they don’t have a footprint to take action when data is at risk.
Sends alerts that lack context to investigate
In order to understand the user’s intent, security analysts investigating a potential incident often need to hunt for additional details beyond what an alert from an IRM tool provides them.
How we're changing the game
Cyberhaven redefines insider risk management
We don’t just accurately detect insider threats. Cyberhaven intervenes the moment data is at risk to protect it, then we give security analysts everything they need to quickly investigate.
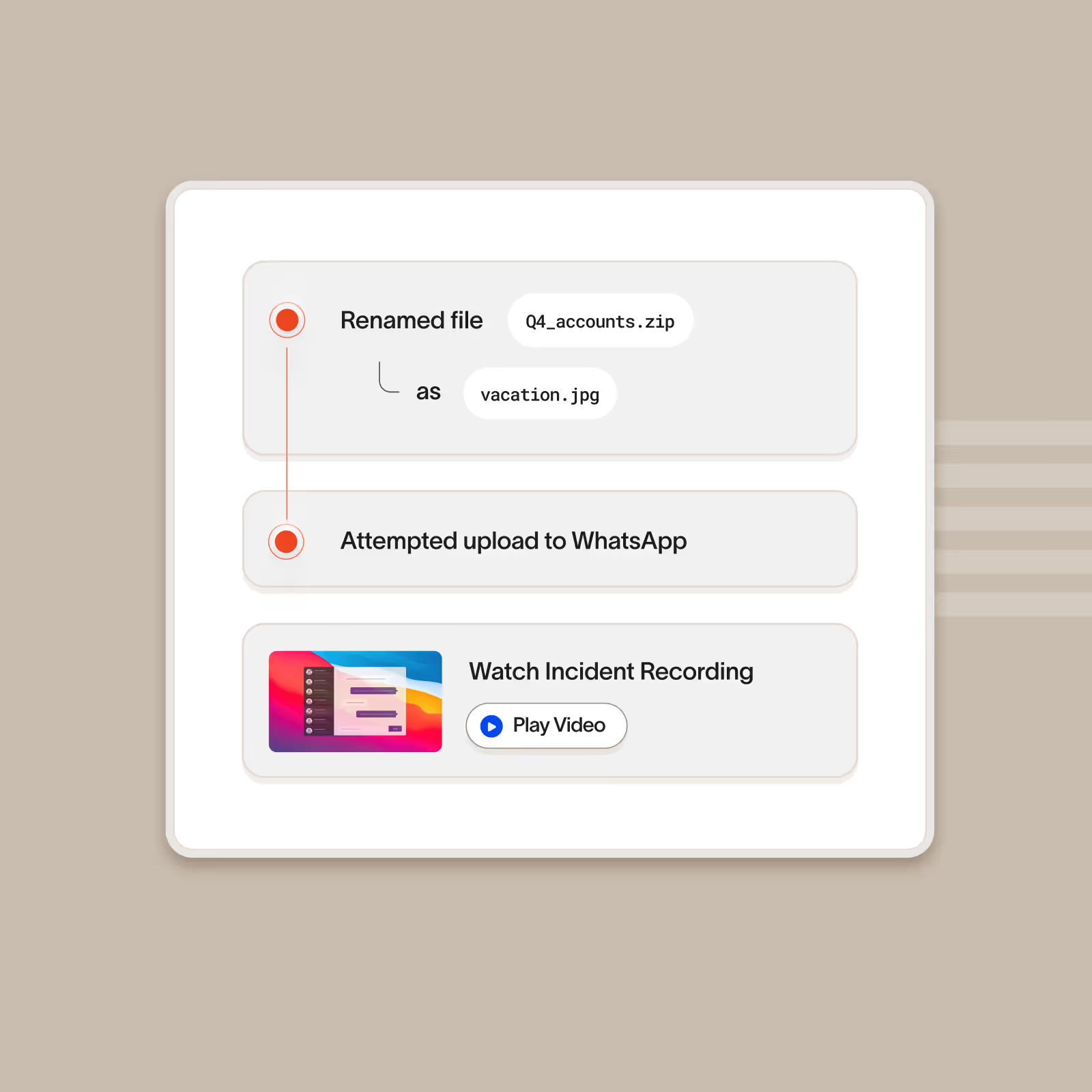
Don’t just accurately detect insider threats, stop them
Cyberhaven is built to take immediate action when there’s an insider threat in progress to prevent someone from taking important data. We block data exfiltration across all channels including cloud, email, websites, removable storage devices, Apple AirDrop, and more.
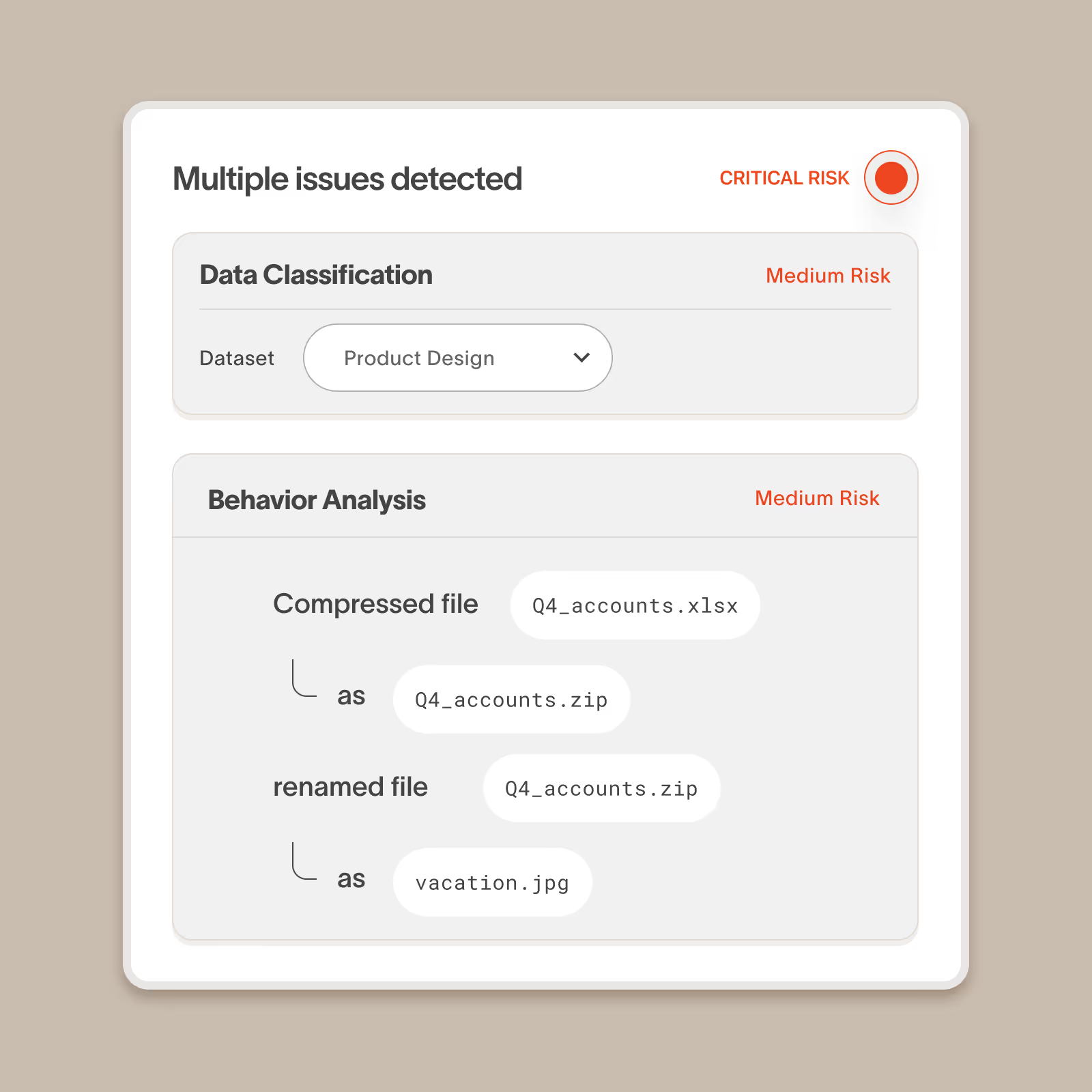
Combine behavioral analysis with data analysis to accurately detect threats
Cyberhaven precisely distinguishes between an employee performing an action with important corporate data versus personal/unimportant data. This additional dimension makes us more sensitive to actual insider threats while allowing us to ignore many everyday behaviors that aren’t risky.
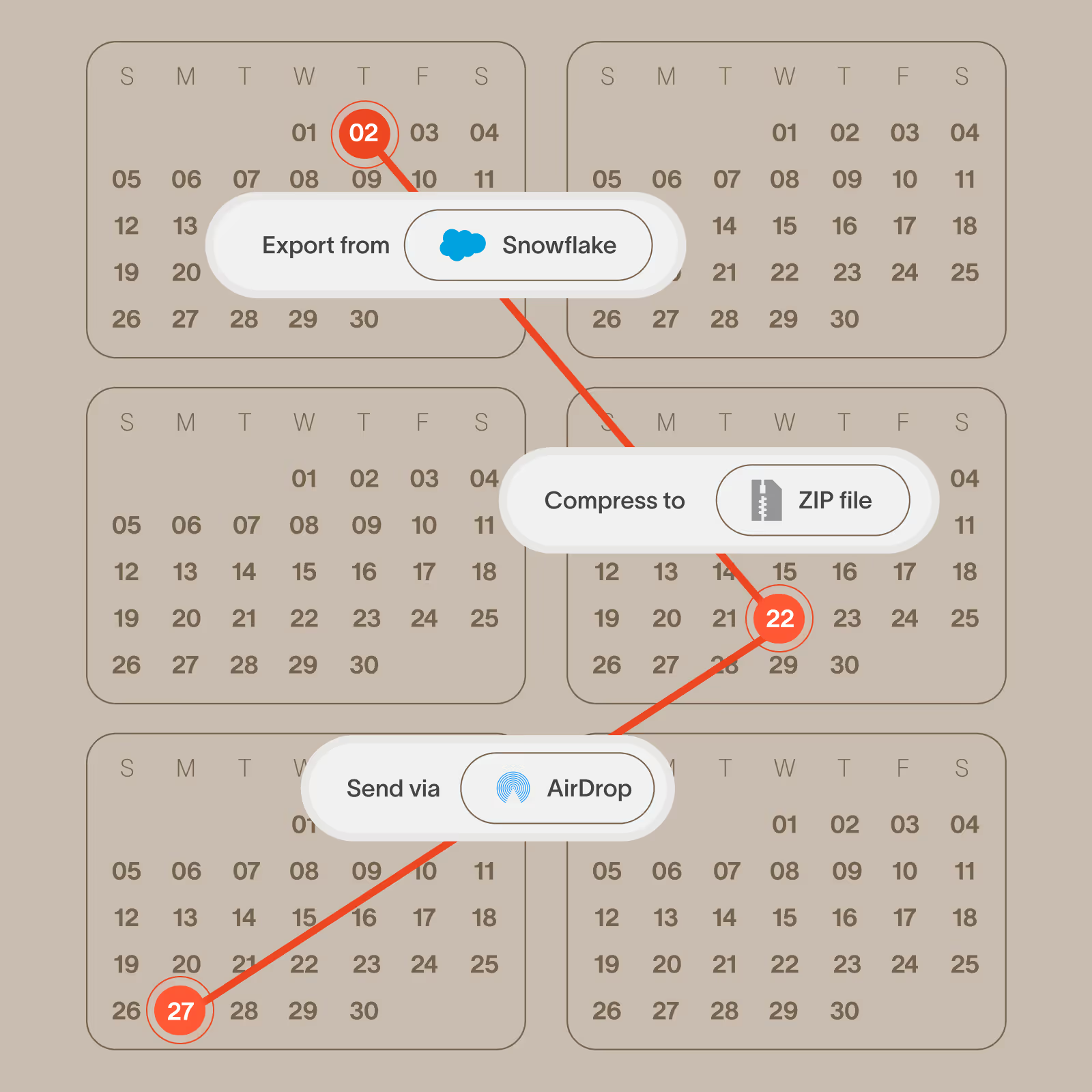
Identify threats that unfold over weeks or months, not just hours
Cyberhaven stores a record of events indefinitely and we can correlate events occurring weeks or months apart, which is how many threats happen in the real world.
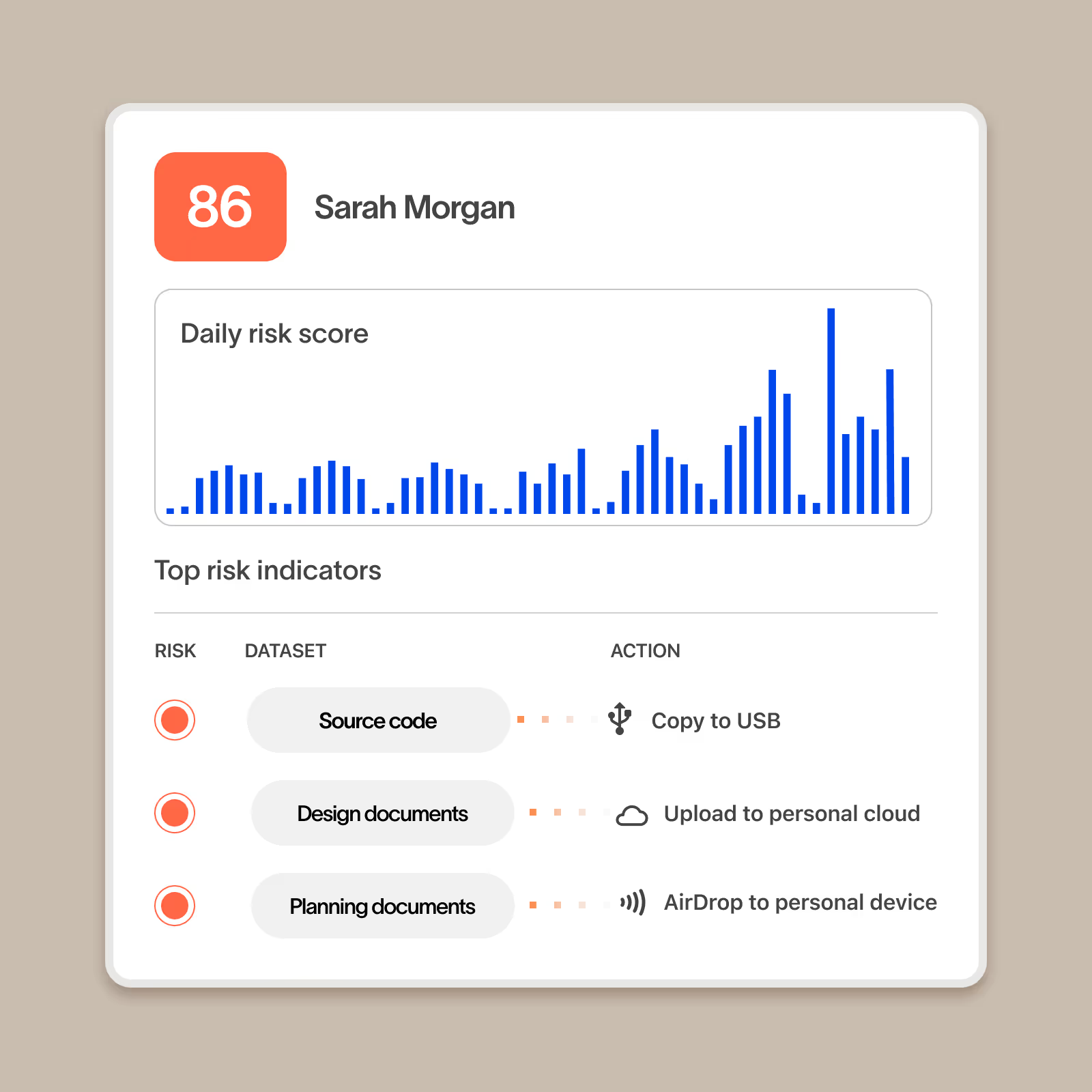
User risk scores that incorporate data sensitivity, not just behavior
Cyberhaven scores users not just on the actions they take but also what type of data is impacted. Risk scores also incorporate details about the user including watchlist membership and risk groups based on factors such as employee performance for a complete picture of a user’s risk.

Stepped up response actions for users with a history of risky activity
With Cyberhaven, you can add users with a history of risky behavior to a user group that has elevated remediation. Instead of responding based on the risk of a single incident, the product will apply elevated remediation such as blocking the risky action instead of just warning the user.
Forensics without the friction
Collect forensic-level events
without physical access to a device
We remotely capture every user action related to every piece of data and securely store it in our cloud so you can perform a post-incident investigation without needing physical possession of a device.
Everything else you expect from an insider risk management solution
When we set out to redefine IRM, we included the standard features you expect.
Collect user behavior across platforms
Collects user behavior across cloud, devices, messaging, email, apps, and more and correlates related events across platforms.
Flag filename or extension changes
Flags when a user changes the extension or name of a file that contains sensitive data and can block subsequent exfiltration.
Track changes to sharing permissions
Tracks sharing permissions to individual users and also links that can be accessed by anyone in the organization or anyone with the link.
User watchlists and elevated remediation
Add users to watchlists and apply elevated response actions such blocking upload to unapproved destinations without allowing the end user to override.
Distinguish personal and corporate app instances
Distinguish between the corporate instance of an approved cloud application and a personal instance of the same application.
User directory integration
Integrates with on-premises and cloud-based directory services to pull user details such as department, manager, and departure date.
Screenshot capture
Optionally record the user’s screen in the seconds leading up to an incident. Screenshots are stored in the customer’s cloud.
Forensic file capture
Incidents for content-based policies include a highlighted excerpt showing what triggered the policy. These matches are stored in the customer’s cloud.
Reporting and analytics
Includes out-of-the box dashboards and a fully customizable reporting engine for advanced analytics.
SIEM integration and APIs
Natively integrates to SIEM tools such as Splunk and exposes incidents through an API so you can add them to any third-party security tool.
Role-based access control
Includes standard out-of-the-box roles or create your own custom roles with any combination of permissions.
Unified visibility and enforcement
Cyberhaven AI & data security platform
One unified solution for protecting data wherever it lives and goes.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
