DLP Reimagined
We questioned every assumption and built a DLP solution from the ground up to protect data in a better way.
Why old-school DLP falls short
The limitation of traditional DLP
Traditional data loss prevention tools fail to protect important data, block normal activity, and use outdated technology that makes life painful for administrators and end users.
Relies too much on content inspection
Relying entirely on content analysis, DLP tools don’t accurately identify important data. They also generate false positive alerts that waste the time of analysts.
Creates a bad experience for end users
Because false positives block users from doing their work, the prevention features of DLP tools often aren’t turned on. Their outdated technology also slows down computers and breaks cloud apps.
Is time consuming to
deploy and manage
Security teams need to invest a lot of time and resources fine tuning DLP content policies to reduce false positives. Older DLP tools also require on- premises software and databases.
Next-generation DLP
Cyberhaven redefines data loss prevention
We identify important data that traditional DLP tools can’t and protect that data across all exfiltration channels with one product and one policy.
Combine content analysis and data lineage to reduce false positives
We combine content analysis with data lineage – where the data originated, where it’s been, and who’s handled it – to better identify what data is important and what’s not. Our approach minimizes false positives created by common content patterns such as phone numbers and emails.
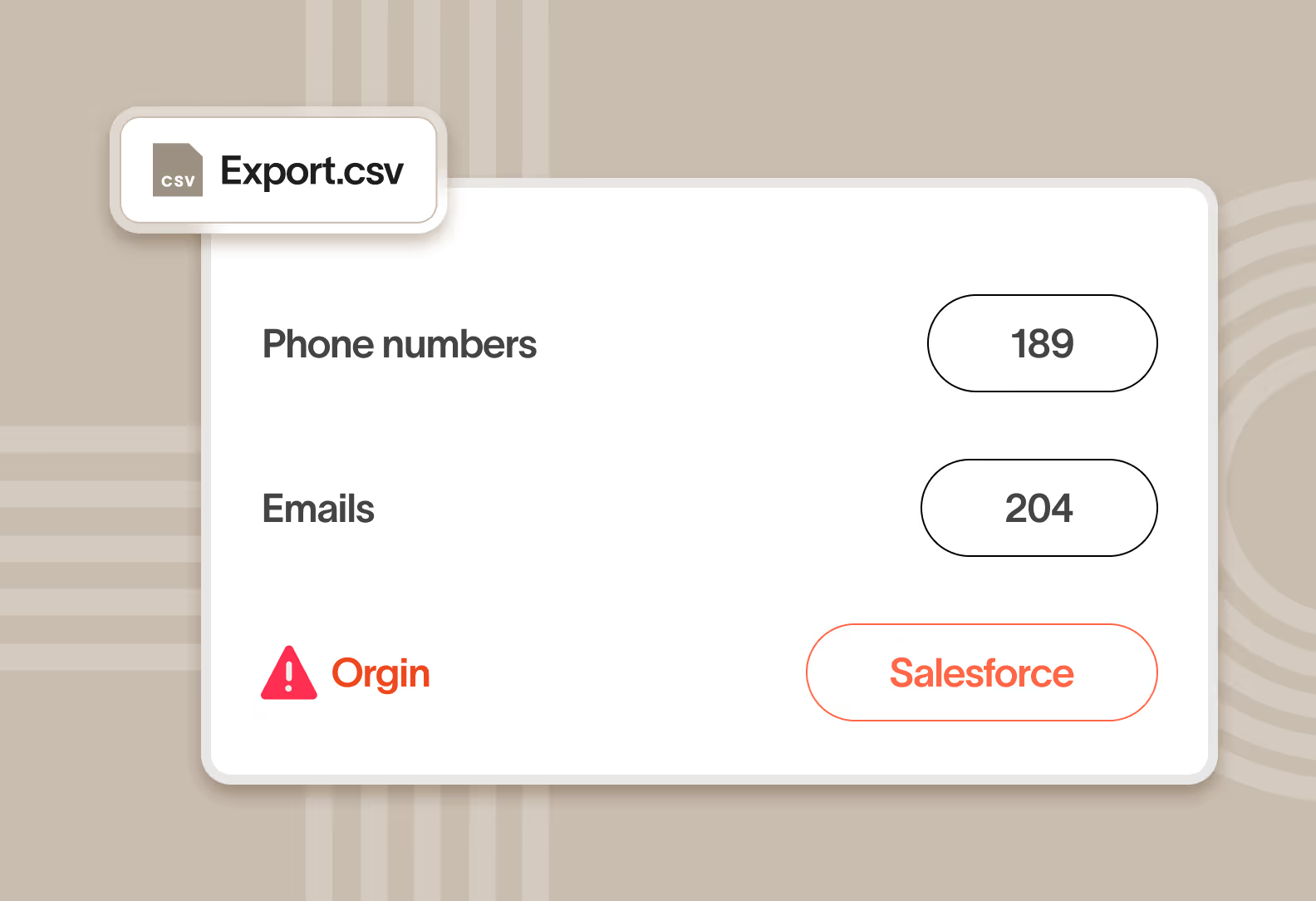
Find, follow, and protect data that eludes content analysis
Important data often contains no recognizable content pattern, and sometimes no text at all. Data lineage helps us identify what other tools miss including:
Real-time action
Take real-time action to protect data and educate users on the right behavior
.avif)
When data is at risk of being exfiltrated, instantly take action and surface a message to the user educating them on company policy and acceptable behavior. An educated employee base leads to 80% fewer incidents and reduced risk to data over time.
Investigate incidents with a full picture of the events before attempted exfiltration
Cyberhaven provides an incident response view tracing every step and action related to a piece of data leading up to an incident, including who handled it and how it moved throughout the organization so analysts can investigate and resolve incidents faster.
Outdated rules slowing you down
Simple, powerful policies that are easy to create and maintain
Cyberhaven data lineage makes it possible to define incredibly simple policies and get better results with fewer false positives than policies based on content analysis alone.
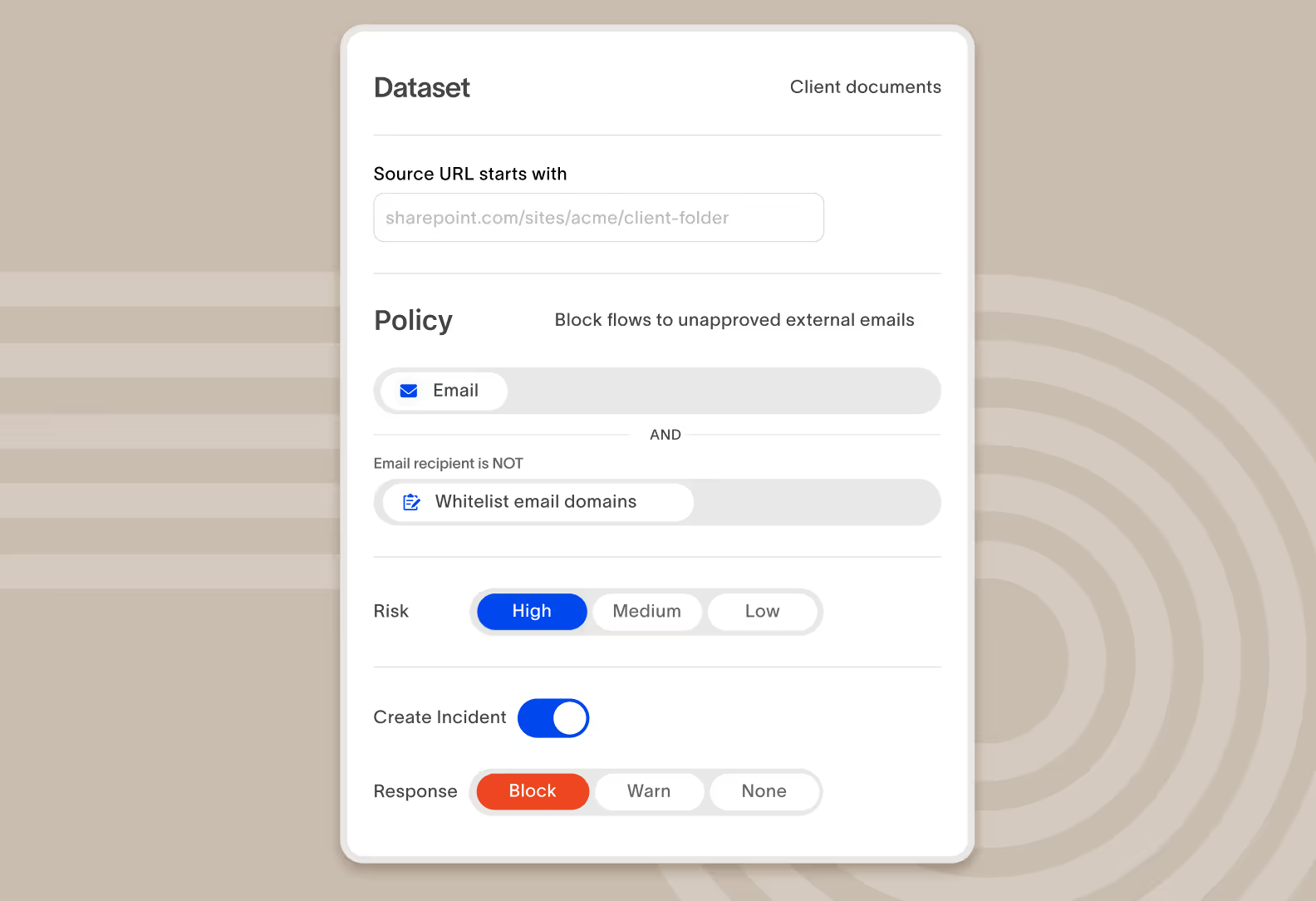
Define policies using an intuitive visual policy editor
Create and edit policies using a visual builder with built-in Boolean logic and auto-complete that pulls in historical source and destination applications, URLs, devices, user groups, and more. You can also convert any graph query to a policy in one click.
Test policies on historical data to quickly preview and iterate
Cyberhaven maintains a complete record of every user action for every piece of data. When editing a policy, you can see how it would apply to historical data to quickly make any adjustments without deploying it in production and waiting weeks for results.
.avif)
Protect data obscured by encryption and compression
Cyberhaven tracks what type of data was encrypted or compressed, so even after the data itself cannot be scanned you can track it and protect it from exfiltration.
Modern DLP delivered from the cloud
Cyberhaven’s service is delivered from the cloud, so there are no databases or application servers to manage.
Everything else you expect from a DLP solution
When we set out to redefine DLP, we included the standard features you expect.
Out-of-the-box policy templates
Get started quickly with dozens of out of the box policies for common use cases and industry-specific requirements.
Standard and custom content identifiers
Includes content identifiers for common PII, PCI, and PHI patterns, standard keyword lists, or create your own identifier with custom RegEx.
Optical character recognition (OCR)
Extracts text content in image files and PDFs and supports use of this data in content-based policies.
Recognizes third-party classification labels
Recognizes labels that classification products such as Microsoft AIP apply to files and supports labels in Cyberhaven policies.
User directory integration
Integrates with on-premises and cloud-based directory services to support granular user group and department based policies.
Match highlighting
Incidents for content-based policies include a highlighted excerpt showing what triggered the policy. These matches are stored in the customer’s cloud.
Role-based access control
Includes standard out-of-the-box roles or create your own custom roles with any combination of permissions.
Screenshot capture
Optionally record the user’s screen in the seconds leading up to an incident. Screenshots are stored in the customer’s cloud.
Reporting and analytics
Includes out-of-the box dashboards and a fully customizable reporting engine for advanced analytics.
SIEM integration and APIs
Natively integrates to SIEM tools such as Splunk and exposes incidents through an API so you can add them to any third-party security tool.
Unified visibility and enforcement
Cyberhaven AI & data security platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
