Understand how dataflows.
See what systems store different types of data and how data moves within the company to new places and people.
Data discovery
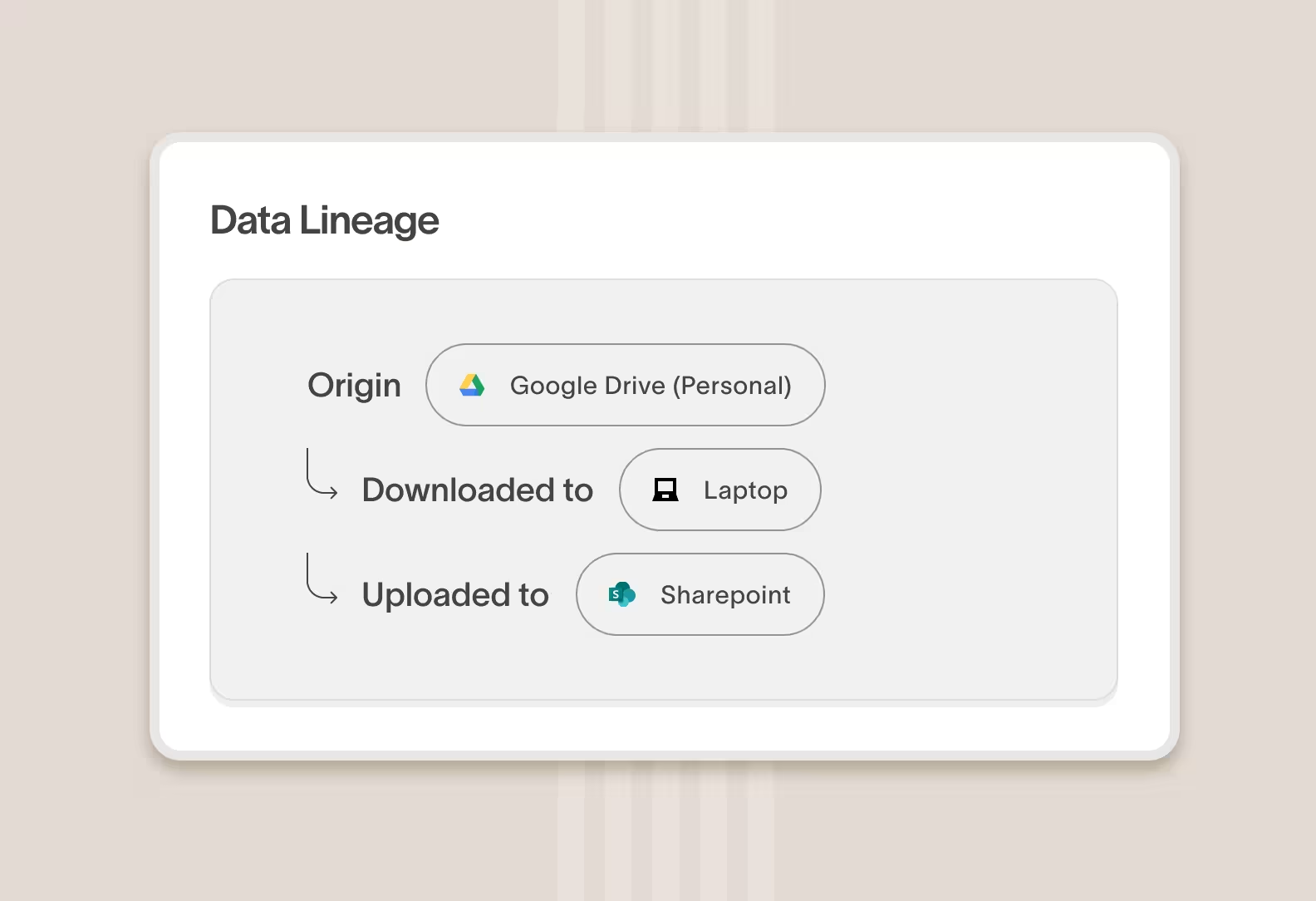
Identify where data is stored and who has copies of it
Cyberhaven's reimagined DLP & insider risk solution tracks the usage and movement of corporate data—revealing unknown data, applications, and storage locations. With this insight, security teams are better prepared to have a risk-based conversation about policy with the business.

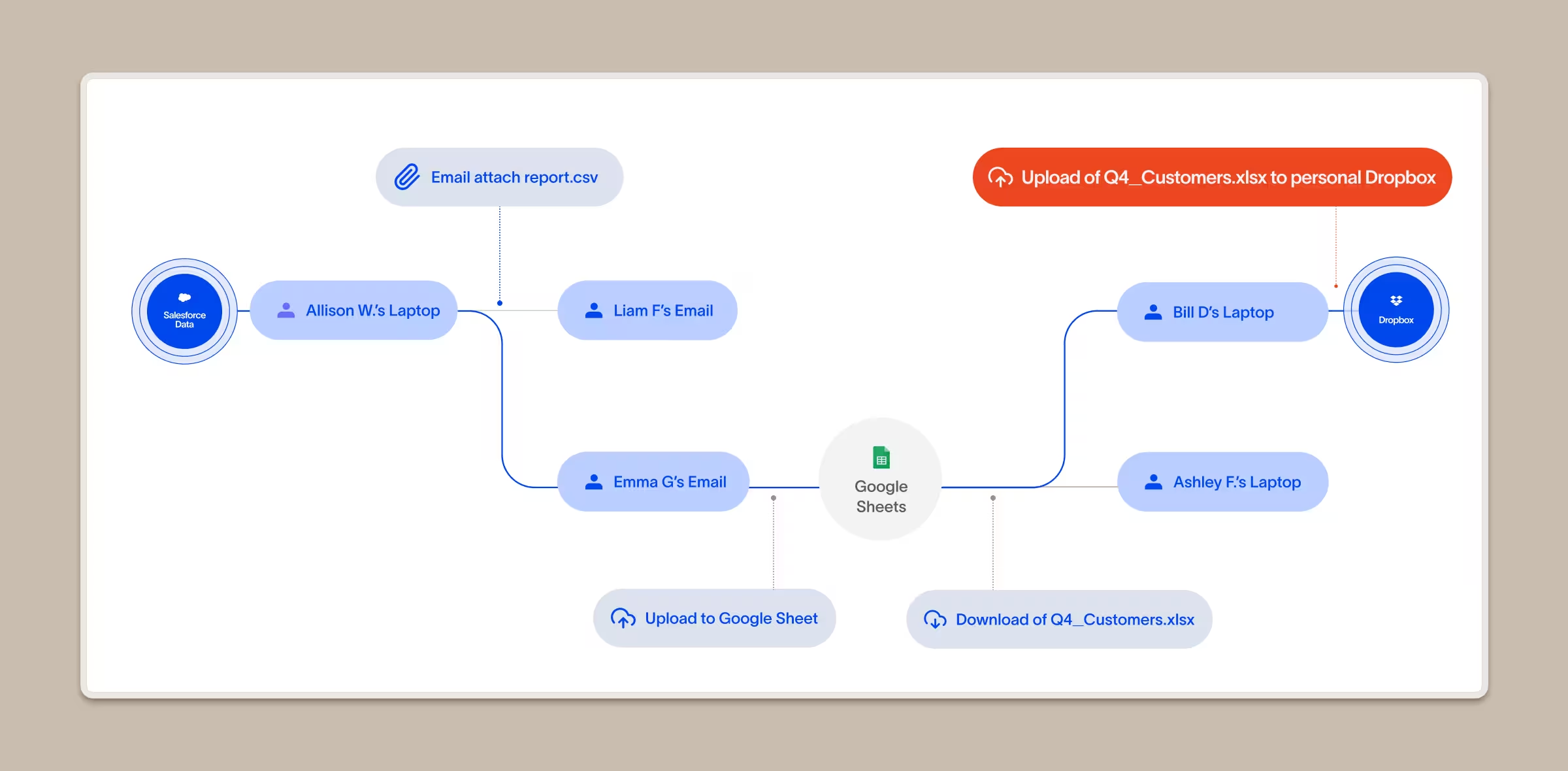
See the complete journey of any piece of data within your company
Cyberhaven tracks every piece of data within your company from origin through every step it takes. You can drill down and see the history of a specific piece of data, or a specific type of data, and follow it from person to person and from application to application.

Track data, not just files
Data that’s in a file can be copied to another file or application (leaving behind any classification tags) and an increasing amount of corporate data lives in cloud applications where there are no files. Cyberhaven tracks data at a granular level, regardless of whether it’s in a file or not.
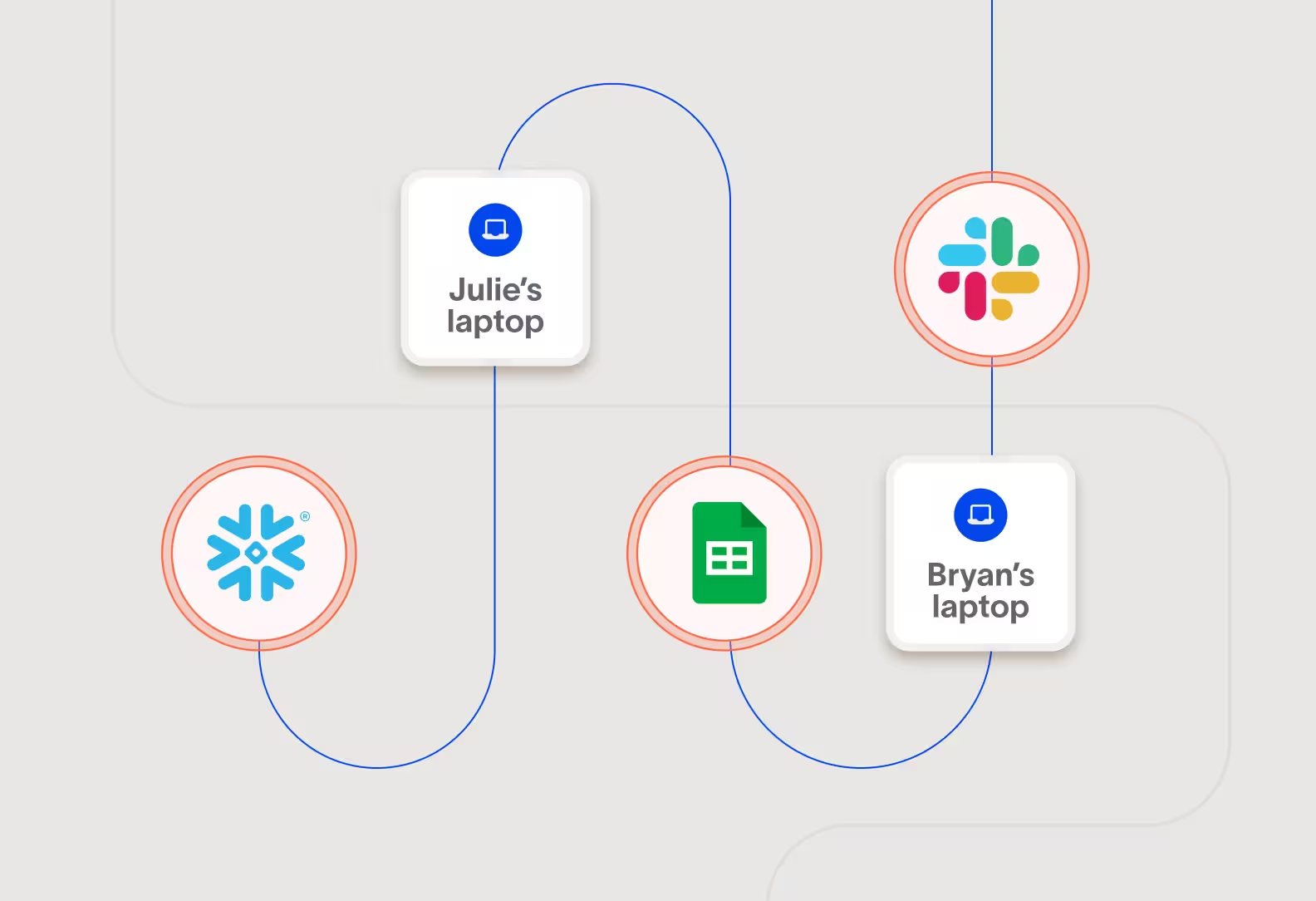
Track data between cloud and devices and between clouds
Data can pass through more than one type of asset so to fully understand data movement you need more than a point solution. Cyberhaven tracks data across cloud applications, computers, email, messaging, file servers, and more.
What makes us different
Cyberhaven reveals data movement
and risk like no one does

Unified visibility and enforcement
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
