Cyberhaven for cloud.
Block important data from leaving your control via cloud, web, email, removable storage, and more.
Cloud Risk
The challenges securing cloud usage
Cloud applications drive productivity and efficiency for business of all kinds, but pose a risk of data leakage information security teams must content with.
Sensitive data exposure due to personal cloud
While cloud usage drives legitimate business needs, leaks via personal cloud accounts pose a threat to information security.
Business pressure to not block personal usage
Banning the usage of personal cloud accounts isn't an option for many security teams due to the impact on company culture and employee morale.
Rapid pace of new applications
Business teams adopt new cloud services every day, and IT teams need a security approach that can keep up in understanding and controlling their usage.
Easy-to-use
Control the flow of data to the cloud with simple, powerful policies
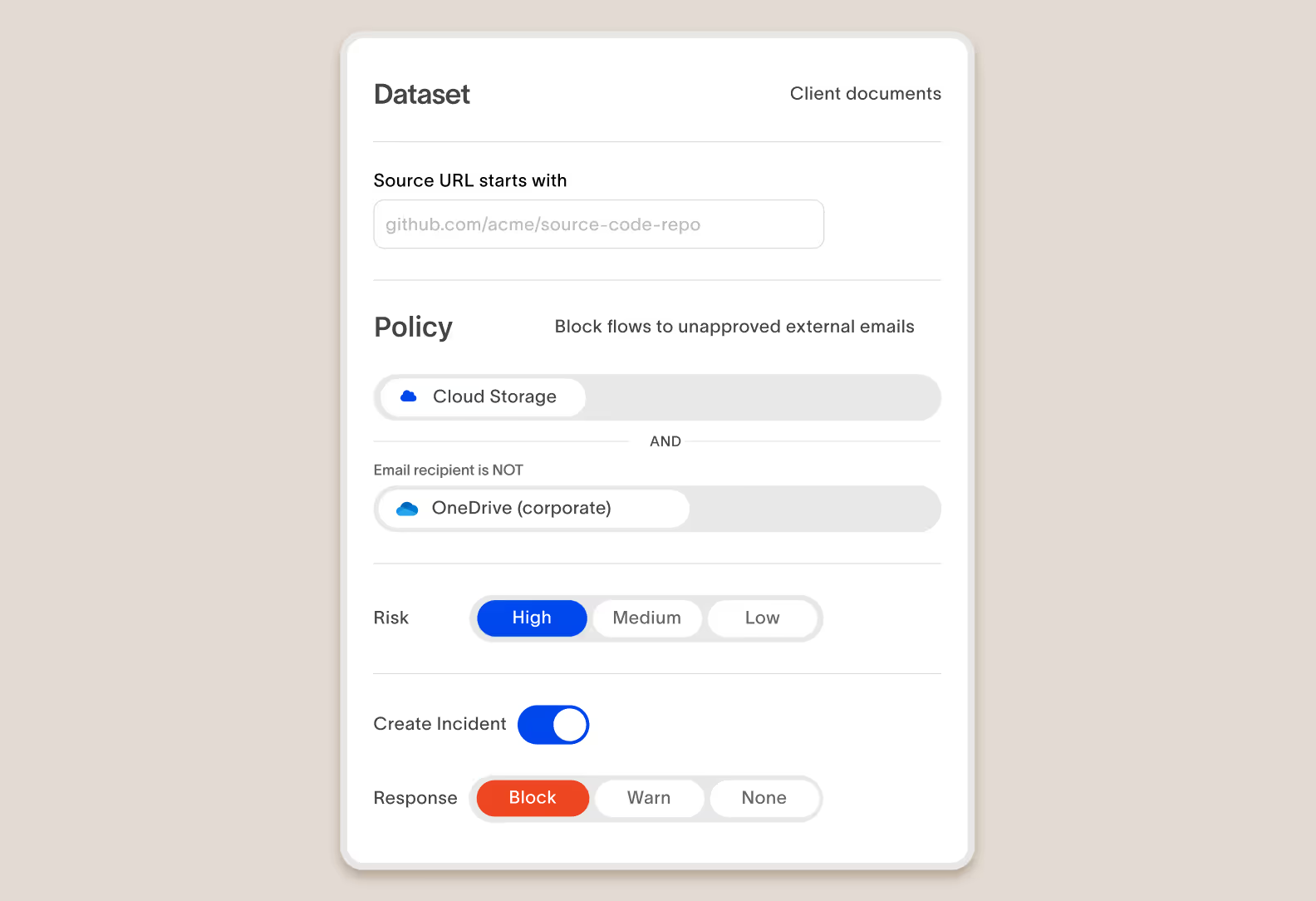
Cyberhaven makes it possible to define incredibly simple policies that prevent your sensitive data from flowing to unsanctioned cloud accounts.
Test policies on historical data to quickly preview and iterate
Cyberhaven maintains a complete record of every user action for every piece of data. When editing a policy, you can see how it would apply to historical data to quickly make any adjustments without deploying it in production and waiting for results and complaints.
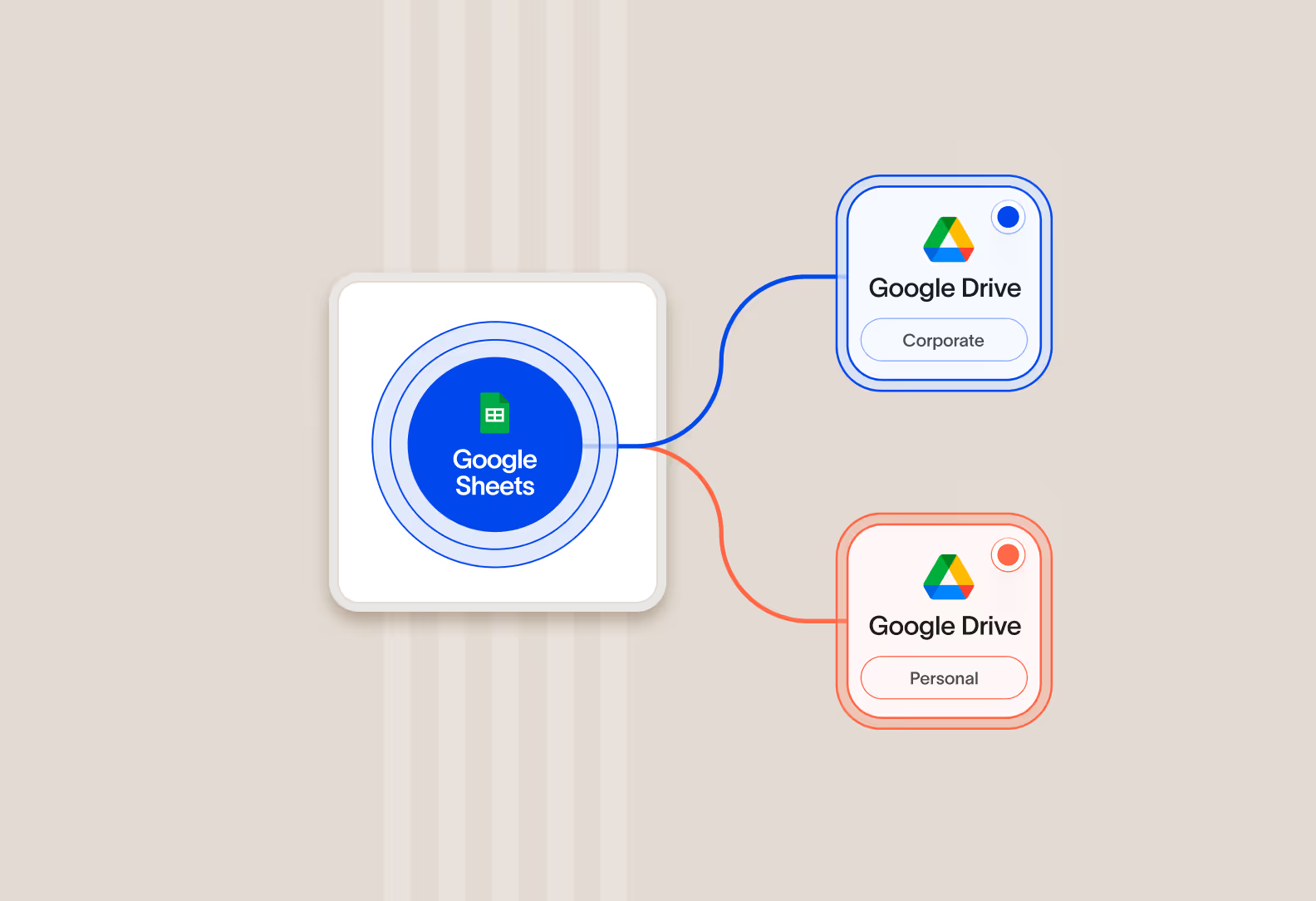
Enforce different policies for corporate and personal instances of the same app
Cyberhaven provides granular visibility and control to allow appropriate usage of corporate apps, while preventing abusive use of personal apps.
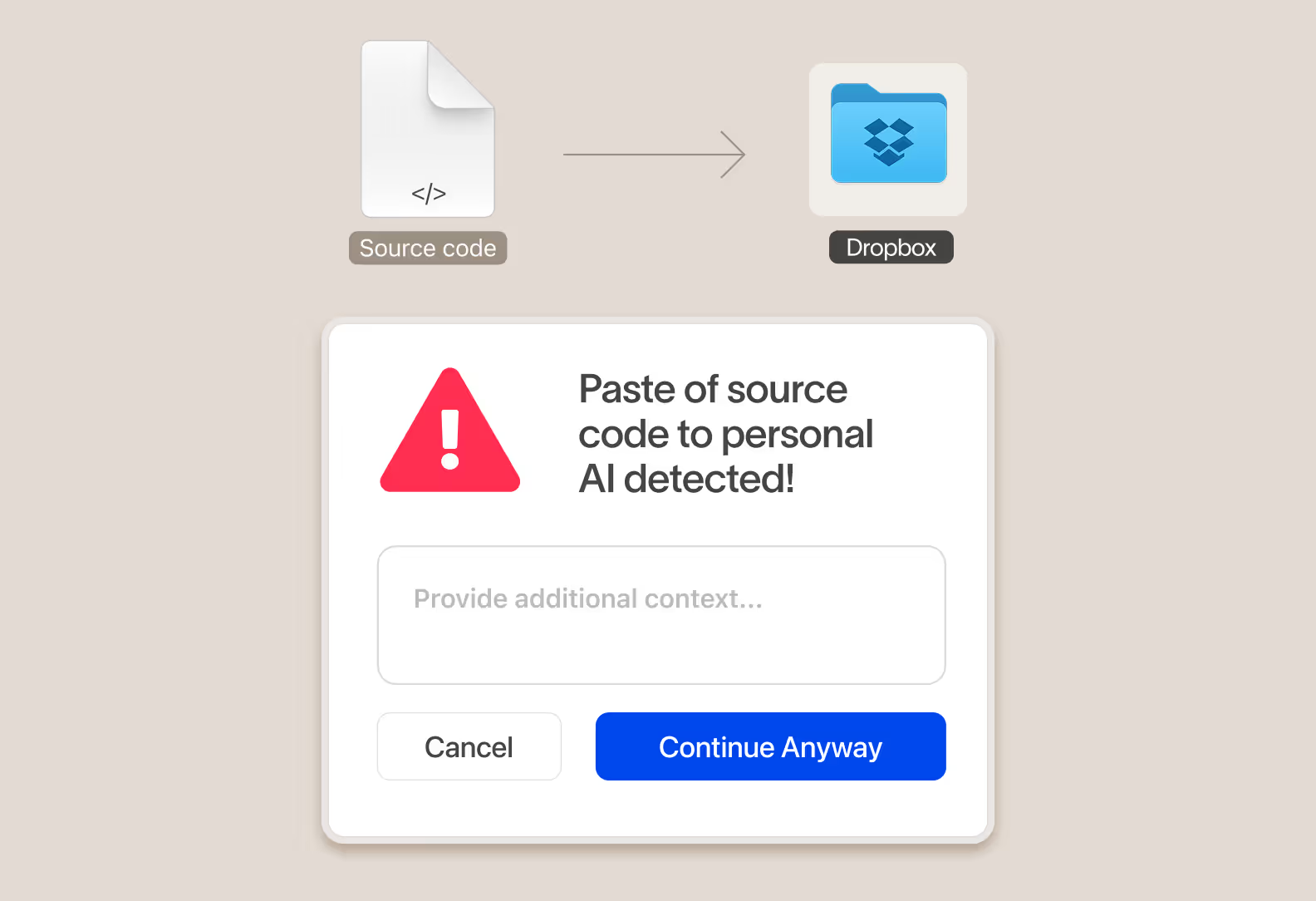
Take real-time action to protect data and educate users on the right behavior
When data is at risk instantly take action and surface a message to the user educating them on company policy and redirect them to approved alternatives.
Complete coverage
One product to protect data across
every exfiltration channel
Cyberhaven Data Detection and Response (DDR) makes it possible to stop exfiltration across all channels with one product and one set of policies.
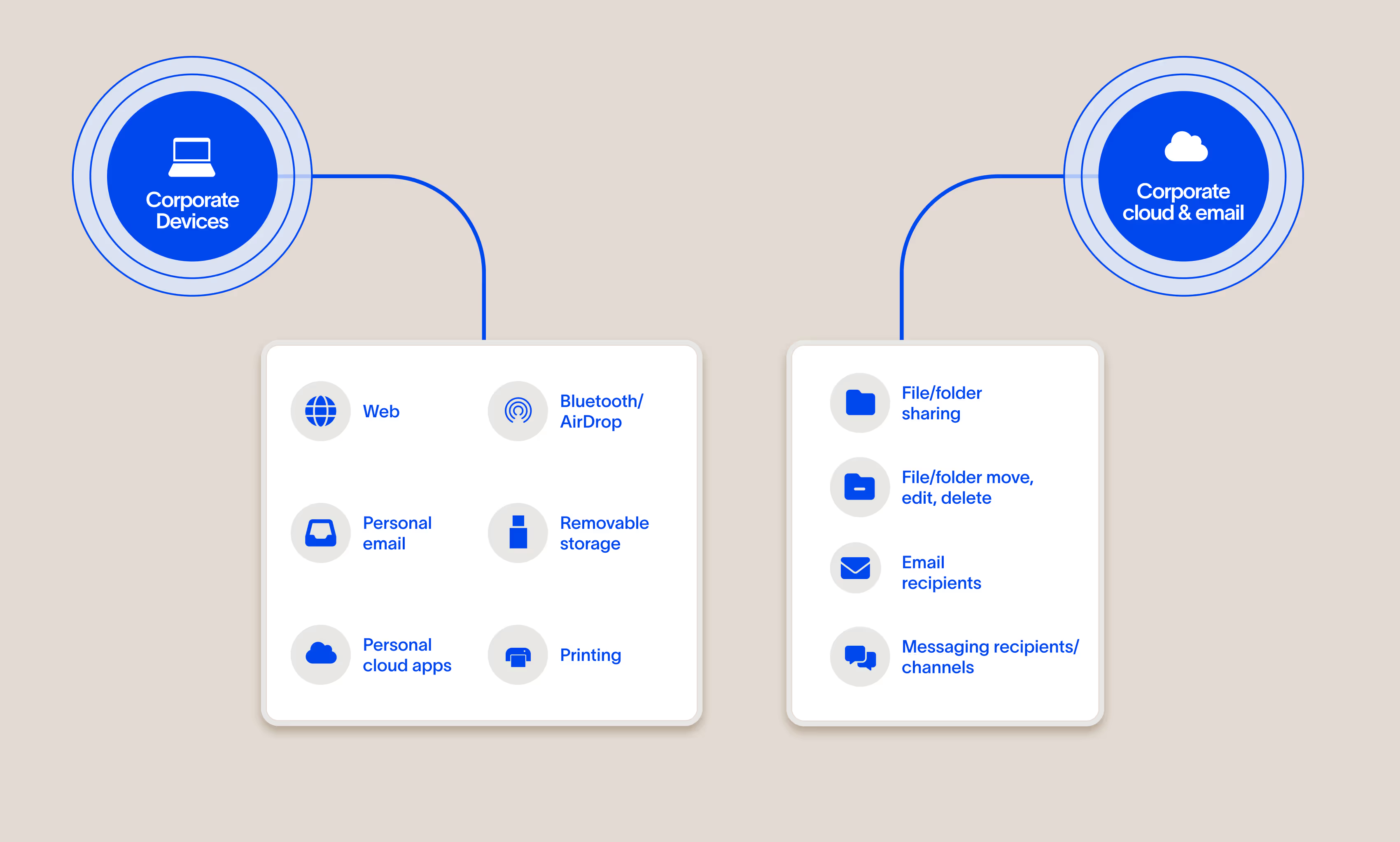
Unified visibility and enforcement
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes.
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
