Enterprise data has become nomadic. What once lived safely behind corporate firewalls now travels across dozens of cloud applications, gets copied into collaborative documents, flows through AI tools, and transforms as employees work from coffee shops, home offices, and airport lounges.
This shift has created a security paradox: the very data mobility that drives modern productivity also makes protection exponentially harder. Traditional security tools were designed for a world where data stayed put and users worked from predictable locations. Today's reality demands a completely different approach.
At Cyberhaven, we've reimagined DLP and insider threat from the ground up, centered on how people actually use data. Instead of only examining content, we add vital context about where data came from, who's interacted with it, and how it's been modified over time. By combining content inspection with context from data lineage, we deliver dramatically better data protection.
This summer, we're expanding that vision with four powerful new capabilities that make data security smarter, faster, and easier to operate.
What's New: Adding Intelligence Where It Matters
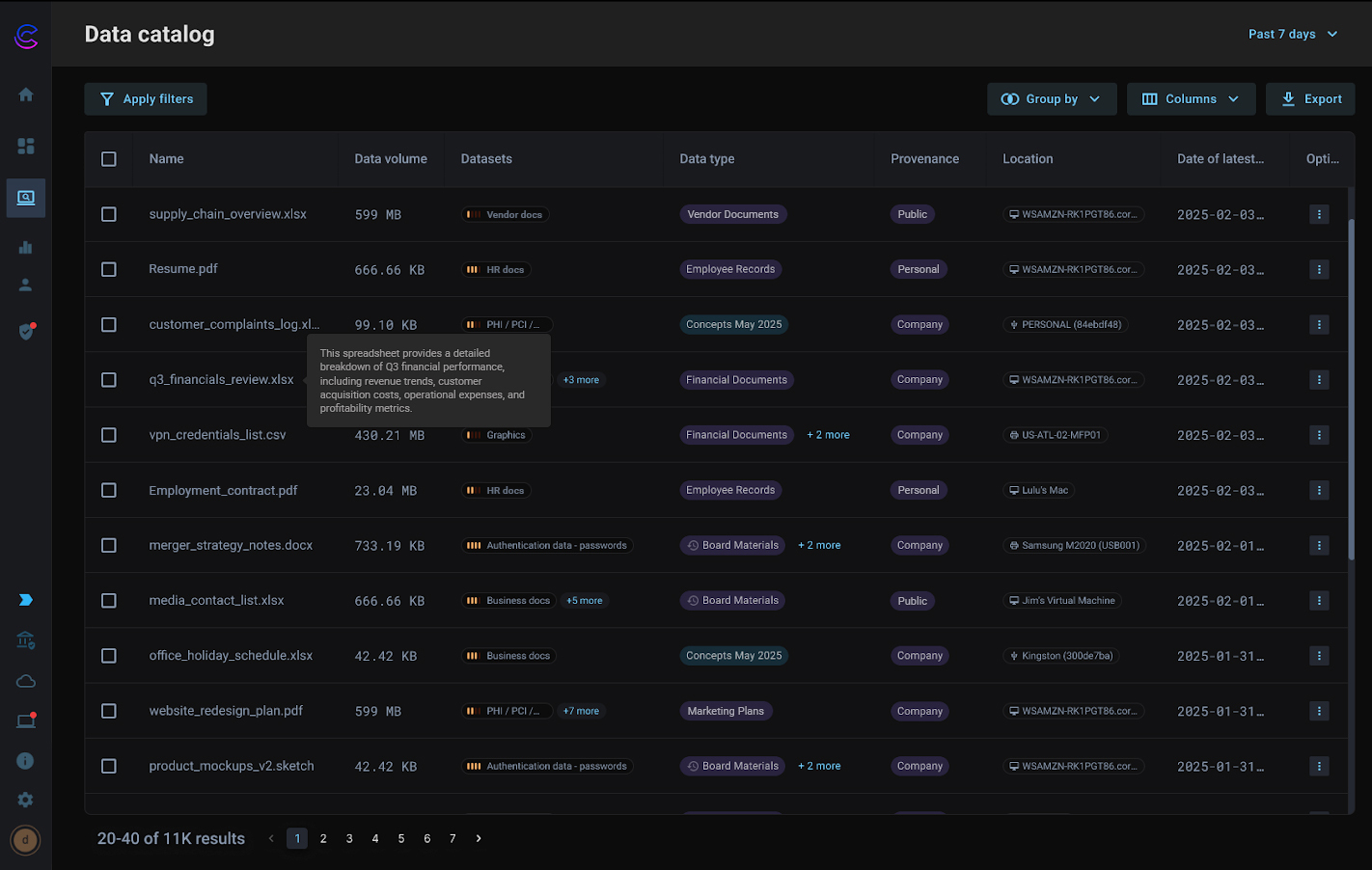
Data Catalog: Complete Visibility Into Your Data Universe
Many organizations lack visibility into what data they have, making protection nearly impossible. You can't secure what you can't see.
Data Catalog solves this by providing a centralized, searchable view of your data across endpoints and cloud. You get a unified inventory with rich metadata for each object, including where it lives, how it's been modified, and who's interacted with it.
This isn't just another data discovery tool—it's smarter visibility that helps you build better policies, identify gaps, and prioritize what you really need to protect.
Most data catalogs display a static understanding of data—the data that lives in a repository. The second data moves, they lose visibility of that data. Cyberhaven uncovers data at rest and in motion, tackling one of the most difficult challenges in data security.
AI-Powered Data Classification: Let AI Do the Heavy Lifting
Traditional approaches require security teams to write and maintain rules that inevitably become outdated the moment business needs evolve.
AI-Powered Data Classification goes far beyond automation, enabling security teams to move fast and with ease. Our AI engine deeply understands data context, generates clear summaries, and applies accurate classification to data, all without human intervention. It even identifies the data's provenance, telling you whether it's critical IP from a corporate repository or non-sensitive information from a public source.
Traditional classification outputs are rife with inaccuracies and often require manual validation. Rather than trust a mysterious black box, Cyberhaven gives you clear summaries of why data was classified a certain way, instilling confidence that your data is classified accurately.
Cloud Connectors: Extend Protection Where Data Actually Lives
Cloud applications have become the primary workspace for many enterprises, but they've also become a problematic blind spot for data security. While many cloud DLP tools can see when files enter or leave these environments, they miss the rich interactions that happen inside them.
Cloud Connectors change this by extending Cyberhaven’s data lineage tracking into platforms like OneDrive, SharePoint, and Google Drive. The system doesn't just monitor file transfers—it understands sharing patterns and suspicious data movements.
One major benefit is detecting when employees access cloud data from unmanaged devices. This isn't about blocking legitimate work, but rather understanding when business information might be at risk due to device security gaps or policy violations.
The connectors give you smarter insights into data exfiltration risk, with data lineage providing visibility into data use in the cloud, and connecting what users do on their devices with how data moves in and out of cloud apps.

Endpoint Data-at-Rest Scanning: Proactive Protection That Actually Works
Most data protection happens reactively—scanning files as users try to share them and making split-second decisions about whether to allow or block the action. This creates an impossible tradeoff between security and user experience.
Endpoint Data-at-Rest Scanning flips this model by doing the work in advance. This approach inspects data stored on user devices, building a comprehensive understanding of what sensitive information exists and where. It happens behind the scenes without disrupting the user.
When users attempt to share or transfer files, policies can be enforced instantly without scanning delays. It’s that fast. The system already knows what the data contains and can make informed decisions about whether the intended action aligns with security requirements.
Now you can anticipate and block risky activity the moment it happens, without slowing anyone down. Your data security program becomes truly proactive.

Key Business Challenges These Capabilities Solve
Together, these four new capabilities address the most pressing data security challenges organizations face today:
Lack of data visibility: Data Catalog provides the comprehensive inventory you need to understand your data landscape and build targeted protection policies.
Manual classification overhead: AI-Powered Data Classification eliminates the time-consuming process of creating and maintaining classification rules while improving accuracy.
Cloud blind spots: Cloud Connectors extend visibility and control to where data actually lives and moves in modern enterprises.
Reactive protection: Endpoint Data-at-Rest Scanning enables proactive blocking without the performance impact and user friction of traditional approaches.
Alert fatigue and false positives: All four capabilities work together to provide better context, reducing the noise that overwhelms security teams while ensuring real threats don't slip through.
Data Security that’s Smarter, Faster, and Easier
As data continues to fragment and flow across an ever-expanding set of tools and platforms, security can't just be about blocking and controlling. It needs to be about enabling innovation while maintaining protection.
Cyberhaven's summer release represents our continued commitment to reimagined data security: protection that understands how people actually work, adapts to how data actually moves, and provides the context security teams need to make confident decisions.
Whether you're dealing with regulatory compliance, insider threat concerns, or the challenge of securing AI adoption, these four new capabilities provide the foundation for a data security program that actually works in the modern enterprise.
Ready to see how reimagined data security can transform your organization? Contact us to learn more about Cyberhaven's latest capabilities and discover how we're making data protection smarter, faster, and easier than ever before.








.avif)
.avif)
