Digital forensics is the scientific method of identifying, preserving, analyzing, and presenting digital evidence in a manner that is legally admissible and credible. This process applies to data from computers, mobile devices, networks, and cloud systems. It plays a crucial role in criminal investigations, cybersecurity incident response, corporate compliance, and litigation, helping to uncover facts hidden within digital information.
Digital forensics is an increasingly important field in our interconnected world, crucial for addressing the complexities of crime, espionage, fraud, and misconduct that occur within digital devices and networks. This discipline, with its powerful tools and techniques, enables investigators to uncover hidden truths within data, including recovering deleted files and tracing cyberattacks. It serves as a fundamental component of modern security and justice systems, showcasing its potential to reveal the truth hidden within digital information.
Digital forensics is not just a concept seen in spy movies; it is an essential practice in law enforcement and corporate settings. Every click, swipe, or tap we make leaves a digital footprint. Digital forensics investigators work diligently to analyze these traces, uncover past events, and contribute to law enforcement, asset protection, and network security.
How Did Digital Forensics Evolve?
The origins of digital forensics can be traced back to the early 1980s, when computers started to play a more significant role in criminal activities. At that time, there were no standardized methods or tools for collecting and examining digital evidence. Investigators often had to improvise their techniques, resulting in inconsistent results and proof that frequently failed to hold up in court.
Key milestones in digital forensics evolution
- Early 1980s: Computers were first recognized as crime tools; no standardized forensic methods existed
- Mid-1990s: Internet-related crime spurs the development of structured approaches to handling digital evidence
- Late 1990s: Organizations like the Scientific Working Group on Digital Evidence (SWGDE)—a standards body established to develop guidelines ensuring digital investigations met scientific and legal standards—emerge to create best practices
- 2000s-Present: With the increased use of smartphones, cloud computing, and the internet, digital forensics has experienced significant growth. It's now recognized as a science, with proper training, certifications, and methods that hold up in court.
As of October 2025, the field of digital forensics will have evolved into a well-established discipline, backed by global standards, professional credentials, and dedicated academic programs worldwide. This evolution signifies the maturity and progress of digital forensics as a science, ready to meet the challenges of the digital age.
What Is the Digital Forensics Process?

Digital forensic investigations follow a well-defined process to maintain the integrity of the evidence and ensure a sound chain of custody. Here are the six critical phases:
1. Identification
Investigators identify potential sources of evidence, such as computers, mobile phones, external drives, cloud services, and IoT devices (e.g., smart thermostats, cameras, or industrial sensors).
2. Preservation
To maintain the integrity of an investigation, forensic images or snapshots of the original data must be created. This critical step ensures the information remains unaltered, as any change, even unintentional, could compromise the evidence's validity in court. The 'chain of custody', which documents the handling of evidence from its collection to its presentation in court, is crucial in this phase.
3. Collection
Data is retrieved from specified sources using forensically sound methods. This process often involves more than just copying files, particularly when handling encrypted storage, fragmented data, or cloud-based services.
4. Examination
Forensic analysts examine extensive digital data, such as documents, emails, logs, and metadata, to identify pertinent information. Their goal is to find evidence that helps reconstruct the sequence of events under investigation.
5. Analysis
Investigators interpret the examined data to understand timelines, relationships, motivations, and potential impacts. It's in this stage that patterns emerge, connections are made, and the whole story begins to unfold.
6. Presentation
Digital forensic experts must clearly communicate their findings to non-technical audiences, including lawyers, judges, and corporate executives. They may also need to serve as expert witnesses in court, defending their findings under oath.
Investigations vary in time, depending on data volume, complexity, and case urgency. Time-sensitive incident response investigations often produce preliminary findings within 48-72 hours.
What Are the Different Types of Digital Forensics?
Digital forensics is a diverse discipline that encompasses specialized subfields, each with its own unique tools, techniques, and challenges.
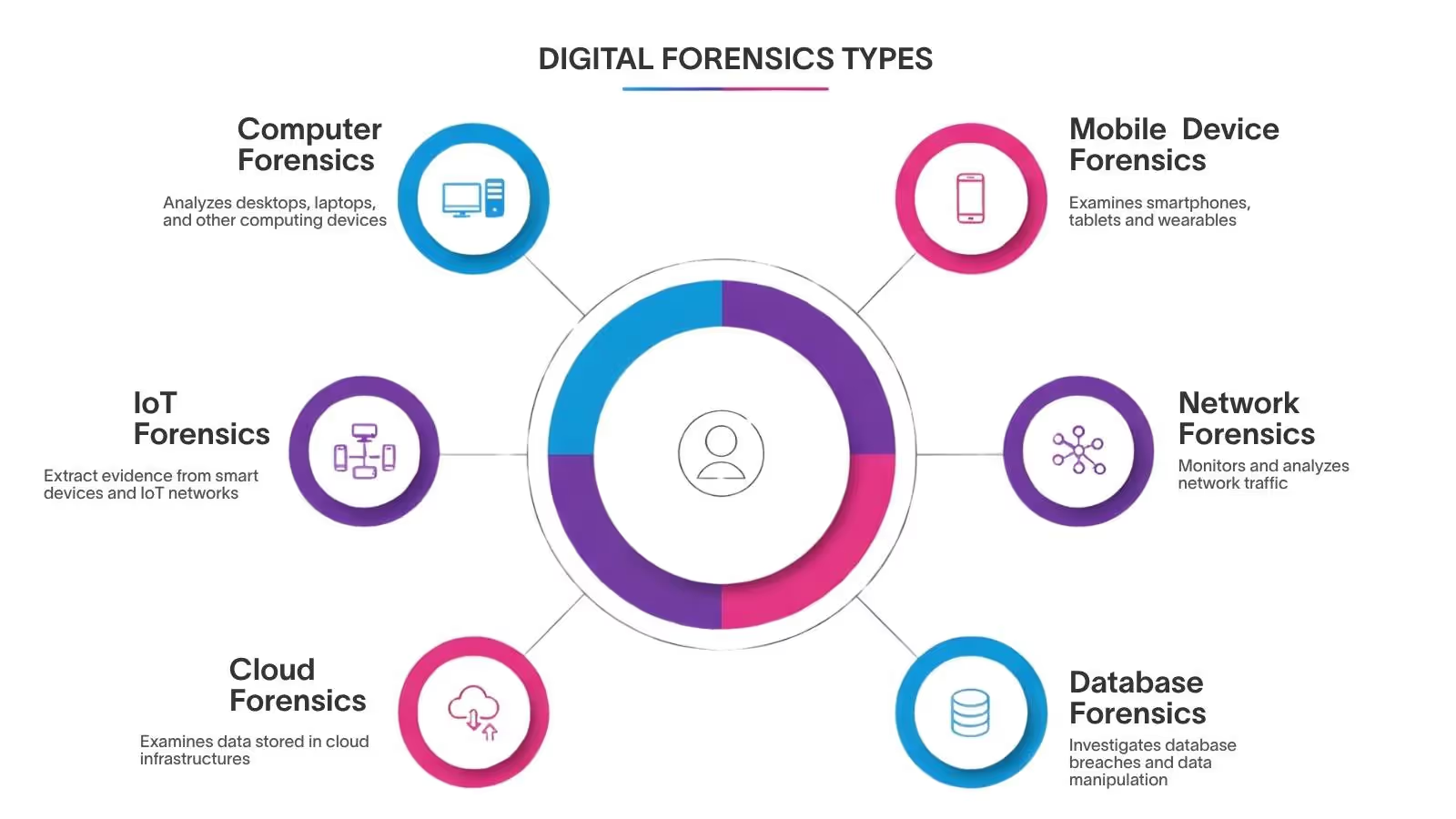
Computer Forensics
Focuses on evidence found on laptops, desktops, and other computing devices. Analysts examine file systems, deleted files, operating system logs, and application artifacts to uncover misuse or trace actions.
Mobile Device Forensics
Smartphones hold a wealth of data, including text messages, GPS location history, call logs, photos, app data, and even biometric authentication patterns. Nevertheless, security features such as encryption and sandboxing can make it difficult to extract this information.
Network Forensics
Focuses on monitoring and analyzing network traffic to detect anomalies or intrusions. Investigators analyze packet captures, firewall logs, and intrusion detection system alerts to trace unauthorized access or data exfiltration.
Database Forensics
Involves analyzing transaction logs, user access records, and table alterations to detect fraud, manipulation, or breaches. This type of forensics is often relevant in financial and healthcare environments where databases are central to operations.
Cloud Forensics
An evolving field that examines data stored in cloud infrastructures. Since cloud environments are distributed and virtualized, traditional forensic methods are often ineffective. Investigators must understand how to work within cloud providers' policies and APIs while maintaining the chain of custody and legal compliance.
IoT Forensics
As smart devices become increasingly common in homes, businesses, and critical infrastructure, they generate valuable data that can provide essential insights. These devices range from smart thermostats to industrial sensors. However, they also pose challenges related to access, standardization, and data volatility.
What Tools Do Digital Forensics Investigators Use?
Digital forensic investigators rely on a specialized toolkit to extract, preserve, and analyze data:
Commercial Solutions
- EnCase (OpenText EnCase Forensic) and Forensic Toolkit (FTK) (Exterro FTK) are widely used in law enforcement and corporate investigations due to their comprehensive capabilities and courtroom credibility.
- These tools can analyze file systems, recover deleted files, and create forensic images with chain-of-custody log.s
Open-Source Tools
- Autopsy provides a user-friendly graphical interface for forensic analysis
- Volatility focuses on memory forensics—examining RAM snapshots to find evidence of malware, rootkits, or unauthorized activity that might not be present on disk
Advanced Techniques
- Data carving: Reconstructing deleted or partially overwritten files based on their binary patterns
- Hash analysis: Quick verification of file integrity by comparing cryptographic hash values (MD5, SHA-256)
- Timeline analysis: Aggregating artifacts from various sources to construct a chronological sequence of events, especially helpful for determining the "who, what, and when" of an incident
As of October 2025, the most common tools include EnCase and FTK (commercial), Autopsy (open-source file system analysis), Volatility (memory analysis), and Cellebrite and Oxygen Forensic Detective (for mobile devices).
What Is Digital Forensics Used For?
Digital forensics has a wide range of applications across industries and use cases:
Law Enforcement
Digital evidence plays a crucial role in uncovering information related to cybercrime, child exploitation, homicide, and fraud cases. Investigators utilize digital traces to link suspects to crimes, identify accomplices, and establish timelines. In the UK, it was estimated that digital evidence is a factor in over 90% of all crimes.
Cybersecurity & Incident Response
Plays a vital role in preventing breaches. Forensic teams are called in to determine the scope, method, and impact of attacks. Their findings are crucial for remediation, prevention, and in many cases, regulatory compliance. Organizations must often conduct forensic analysis to meet GDPR Article 33 breach notification requirements (notification within 72 hours) or to comply with frameworks such as SOC 2 and ISO/IEC 27001.
Legal Proceedings & eDiscovery
Legal professionals rely on digital forensics for eDiscovery, which is the process of collecting and analyzing electronic data in civil litigation. Forensic analysis guarantees that digital evidence—such as emails, contracts, and text messages—is preserved and authenticated in a manner that is valid in court.
Corporate Investigations
Often used in internal investigations related to intellectual property theft, employee misconduct, or policy violations. Whether it's proving a leak of confidential information or verifying compliance with data access policies, digital evidence provides clarity and accountability. Digital forensics supports insider threat programs by providing the evidence needed to investigate suspicious behavior.
Data Security & DLP Programs
Forensic capabilities strengthen data loss prevention (DLP) programs by providing detailed audit trails and evidence of how sensitive data moved through an organization. When DLP systems flag potential violations, forensics provides the investigation layer to determine intent, scope, and impact.
Digital Forensics vs. Related Disciplines
Digital forensics often overlaps with related fields. Here's how they compare:
Incident response should be utilized when confronting an active security threat that necessitates immediate containment. Digital forensics is applicable after an incident has been contained or during criminal investigations when legally defensible evidence is required. eDiscovery is relevant in cases of civil litigation or regulatory inquiries that mandate a systematic review of electronic documents and communications. Many complex investigations, such as data breaches that result in lawsuits, may require the sequential application of all three disciplines.
What Are the Biggest Challenges in Digital Forensics?
Despite its importance and usefulness, digital forensics encounters several significant challenges:
Encryption Barriers
While encryption is crucial for ensuring privacy and security, it can also pose challenges for investigations. Investigators often encounter locked devices or encrypted files that are nearly impossible to access without the data owner's or the manufacturer's cooperation. Modern strong encryption methods, such as AES-256, are complicated to break without the correct credentials.
Anti-Forensics Tactics
Intentional tactics to obscure or eliminate digital evidence include file wiping tools, steganography (hiding data within other files), and malware that erases logs upon detection. Analysts must remain proactive in detecting and combating these techniques.
Data Volume & Complexity
The vast amount of digital data presents a significant challenge. Analyzing terabytes of data across devices and platforms requires not only advanced tools but also careful processes to ensure no details are overlooked. The complexity of modern IT environments is a significant challenge. In 2024, 40% of data breaches involved data spread across multiple environments, including public cloud, private cloud, and on-premises systems, significantly increasing the cost and time of investigation.
Legal & Ethical Considerations
Investigators must adhere to strict rules regarding privacy, consent, and jurisdiction. For example, analyzing a device without proper authorization can render the evidence inadmissible or expose the analyst to legal liability. According to guidance from the Electronic Frontier Foundation, balancing investigative needs with Fourth Amendment protections remains a constant challenge in digital forensics.
Cloud & Jurisdictional Issues
Cloud data may reside in multiple countries, each with its own distinct legal framework. The CLOUD Act (2018) addressed some cross-border data access issues for U.S. law enforcement, but international investigations remain complex.
What Does the Future Hold for Digital Forensics?
As technology continues to advance, so too must digital forensics:
AI & Machine Learning Integration
Artificial intelligence and machine learning are beginning to augment traditional methods by automating routine tasks, recognizing patterns, and identifying anomalies at scale. According to the IBM Cost of a Data Breach Report 2024, organizations that used security AI and automation extensively identified and contained breaches significantly faster than those that did not, saving an average of $1.9 million per breach.
Expanded Cloud Forensics
It will become even more critical as businesses and individuals shift more data to platforms like AWS, Azure, and Google Cloud. Gartner predicted in 2021 that more than 85% of organizations would adopt a cloud-first principle by 2025, requiring investigators to adapt to virtualized environments, multi-tenancy, and complex service-provider audit capabilities.
Standardization & Certification
There's a growing push to establish universal standards for tools, methodologies, and practitioner certifications. Organizations such as the International Organization on Computer Evidence (IOCE) and the NIST Computer Forensics Tool Testing (CFTT) program are working to increase consistency, reliability, and trust in digital investigations across borders and sectors.
Quantum Computing Implications
While still emerging, quantum computing poses both opportunities and threats. It may enable faster analysis of massive datasets but could also render current encryption methods obsolete, fundamentally changing how evidence is secured and accessed.
Conclusion
Digital forensics, a critical discipline bridging technology, law, and security, is essential for solving crimes, responding to cyber incidents, and safeguarding sensitive information. In our increasingly digital world, experts in this field are indispensable. As threats grow in sophistication and data expands exponentially, digital forensics must evolve. This evolution requires new tools, techniques, and frameworks to uncover the truth embedded in digital information.
For organizations building modern data security programs, forensic readiness should be a key consideration. The ability to quickly and effectively investigate incidents, prove compliance, and support legal proceedings can mean the difference between a controlled response and an organizational crisis.
Frequently Asked Questions About Digital Forensics
What is digital forensics used for?
Digital forensics is used to investigate cyberattacks, support criminal prosecutions, conduct internal corporate investigations (such as intellectual property theft or employee misconduct), respond to data breaches, comply with legal discovery requests in litigation, and provide expert testimony in court cases involving digital evidence.
How long does a digital forensics investigation take?
Investigation timelines vary significantly based on data volume, complexity, and the urgency of the case. A basic mobile device examination might take 2-5 days, while a multi-terabyte enterprise breach investigation can span weeks to several months. Time-sensitive incident response investigations often produce preliminary findings within 48-72 hours.
Is digital forensics only used in criminal cases?
No. While digital forensics plays a critical role in law enforcement, it's equally important in civil litigation (eDiscovery), corporate compliance audits, insider threat investigations, cybersecurity incident response, intellectual property disputes, and regulatory investigations. Many organizations maintain forensic readiness programs for proactive risk management.
What's the difference between digital forensics and incident response?
Incident response focuses on quickly containing and remediating active security incidents to minimize damage. Digital forensics is the detailed, methodical examination of digital evidence to determine what happened, how it happened, and who was responsible—often supporting legal proceedings. Forensics is typically part of the "post-incident analysis" phase of incident response.
Can encrypted data be examined in digital forensics?
It depends. If investigators can obtain encryption keys, passwords, or cooperation from device owners, encrypted data can be decrypted and examined. However, modern strong encryption (such as AES-256) is difficult to break without credentials. Forensic teams may use other methods, such as analyzing unencrypted metadata, memory dumps, or cloud backups.
What tools do digital forensics experts use?
Standard tools include EnCase and Forensic Toolkit (FTK) for comprehensive investigations, Autopsy for file system analysis, Volatility for memory forensics, Cellebrite and Oxygen Forensic Detective for mobile devices, Wireshark for network traffic analysis, and X-Ways Forensics for disk imaging and recovery.
Do I need a digital forensics expert for a minor business data breach?
Suppose you manage sensitive customer data, such as personally identifiable information (PII), protected health information (PHI), or payment details, and are subject to regulations like GDPR, HIPAA, or PCI DSS. In that case, it is crucial to engage a qualified forensic professional. They can ensure proper handling of evidence, conduct accurate root cause analyses, and provide defensible reports for regulators or insurers.
How is digital forensics different from data recovery?
Data recovery focuses on restoring lost or damaged files to ensure business continuity. Digital forensics takes it a step further by preserving evidence in a legally defensible manner, maintaining a chain of custody, documenting every action taken, and producing reports suitable for legal proceedings. Forensic methods ensure the integrity of evidence, while data recovery prioritizes the restoration of files.
What is the chain of custody in digital forensics?
Chain of custody is a documented, chronological record that tracks who collected, handled, transferred, analyzed, or stored digital evidence at every step. It proves the evidence remained secure and unaltered from collection through presentation in court or regulatory proceedings. Breaks in the chain of custody can render evidence inadmissible.
Can deleted files be recovered in a digital forensics investigation?
Often, yes—unless the storage space has been overwritten. When a file is deleted, the operating system typically marks that space as available but doesn't immediately erase the data. Forensic tools can "carve" these deleted files from unallocated disk space. Solid-state drives (SSDs) with TRIM enabled and encrypted storage make recovery more challenging.







.avif)
.avif)
