Cybersecurity is the foundation of digital trust, protecting data, systems, and people in an interconnected world. By understanding threats, applying best practices, and embracing new technologies, individuals and organizations can build resilience against cyber risks.
In today's hyperconnected world, cybersecurity has become one of the most critical concerns for individuals, businesses, and governments. Every click, transaction, or interaction that takes place online has the potential to be intercepted, manipulated, or exploited by cybercriminals. The rapid adoption of digital platforms has transformed the way we live and work, but it has also introduced new risks. From personal identity theft to large-scale attacks on critical infrastructure, the consequences of weak cybersecurity can be devastating. Cybersecurity has shifted from being a technical afterthought to becoming a central pillar of trust, resilience, and safety in the digital age.
What is Cybersecurity? (Quick Answer)
Cybersecurity is the practice of protecting computers, networks, data, and systems from unauthorized access, theft, damage, and disruption.
It combines technologies (like encryption and firewalls), processes (such as risk assessments and incident response), and human practices (including training and policies) to safeguard digital assets against evolving threats like malware, phishing, and ransomware. At its core, cybersecurity is about building secure environments where data and systems can be trusted.
With that foundation, the technical definition of cybersecurity is the practice of defending computers, networks, data, and systems from unauthorized access, theft, and damage. It is often compared to the locks on a house or the security guards in a business, except in this case, the goal is to safeguard digital assets rather than physical property. Cybersecurity involves a combination of technologies, processes, and best practices designed to protect against a wide range of threats. This field encompasses everything from encrypting sensitive information to monitoring suspicious network activity and responding quickly to breaches. It is not a single tool or strategy but rather a holistic approach to building secure environments where data and systems can be trusted.
Why is Cybersecurity Important?
The importance of cybersecurity cannot be overstated. As more of our lives move online, the stakes grow higher. Businesses depend on secure systems to protect intellectual property, customer information, and financial transactions. Individuals rely on cybersecurity to keep their personal data, such as bank accounts and medical records, safe from criminals. Governments view cybersecurity as essential to national defense, given that attacks can disrupt transportation systems, healthcare facilities, and energy grids. Without effective cybersecurity, the trust that underpins digital interactions begins to collapse.
In addition, the financial costs of cyberattacks are staggering. According to Cybersecurity Ventures, global cybercrime damages are projected to reach $10.5 trillion annually by 2025. The societal implications go even deeper, as breaches erode confidence in technology and can even threaten democratic processes.
Common Cybersecurity Threats and Attacks
Cybersecurity threats come in many forms, each with its own tactics and objectives:
- Malware (short for malicious software) includes viruses, worms, ransomware, and spyware. These programs are designed to infiltrate and damage systems or steal information.
- Phishing attacks use deceptive emails or websites to trick people into revealing sensitive data such as passwords or credit card numbers.
- Ransomware is a specific type of malware that encrypts a victim's files and demands payment for their release, often crippling business operations.
- Distributed denial-of-service (DDoS) attacks overwhelm systems with traffic to make them unavailable to legitimate users.
- Insider threats arise when employees or contractors misuse their access for personal gain or to damage an organization.
- Advanced persistent threats (APTs) involve sophisticated adversaries, such as state-sponsored groups, who engage in long-term campaigns to infiltrate and exfiltrate sensitive information.
The threat landscape is dynamic and constantly evolving, which is why cybersecurity professionals must remain vigilant and adaptive.
What's the Difference Between Malware and Ransomware?
While all ransomware is malware, not all malware is ransomware. Malware is the umbrella term for any malicious software designed to harm systems or steal data. Ransomware is a specific subset that encrypts your files and holds them hostage until you pay a ransom. Think of malware as the category (like "vehicles") and ransomware as a specific type (like "delivery trucks"). Other malware types include spyware (which secretly monitors activity) and viruses (which replicate and spread to other systems).
What Are the Core Principles of Cybersecurity? (CIA Triad)
At the heart of cybersecurity is the CIA Triad, which stands for confidentiality, integrity, and availability:
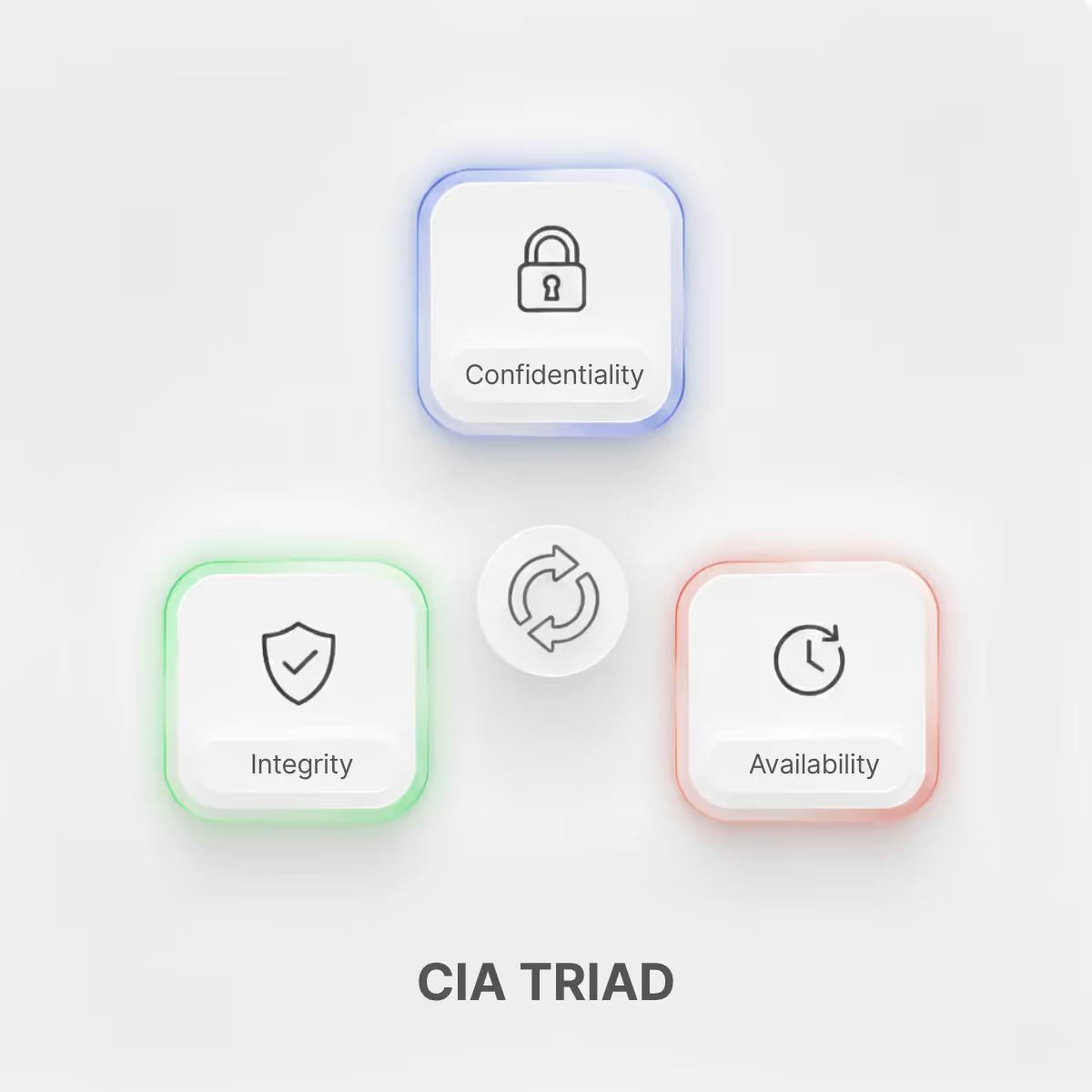
Confidentiality ensures that information is only accessible to those who have the proper authorization. This is often achieved through encryption, access controls, and authentication measures. For example, encrypting patient medical records ensures that only authorized healthcare providers can view sensitive health information.
Integrity refers to the accuracy and trustworthiness of data. It means that information cannot be altered without detection, preserving its reliability for decision-making. Blockchain technology, for instance, uses cryptographic techniques to ensure that transaction records cannot be tampered with after they're created.
Availability ensures that systems and data are accessible when needed, which is critical for businesses and services that depend on constant uptime. Companies often maintain redundant servers and backup systems to ensure that even if one server fails, services remain available to users.
These three principles work together to form the foundation of any cybersecurity strategy. Without confidentiality, private data can be exposed; without integrity, the data cannot be trusted; and without availability, the systems cannot function.
Key Domains of Cybersecurity
Cybersecurity is a broad discipline that spans multiple domains, each addressing a different aspect of protection:
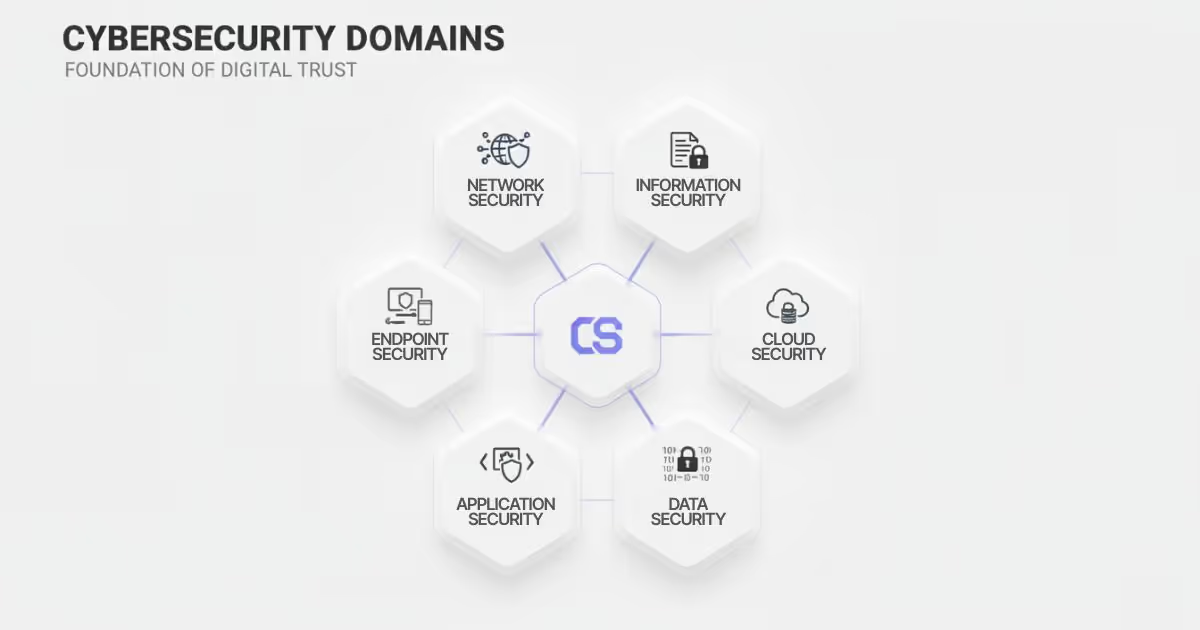
Network security focuses on safeguarding the infrastructure that allows devices to communicate, using firewalls, intrusion detection systems, and traffic monitoring to prevent unauthorized access.
Information security is concerned with protecting the data itself, whether it is stored, processed, or transmitted.
Endpoint security deals with securing devices such as laptops, mobile phones, and tablets that serve as access points to networks.
Cloud security has become increasingly important as organizations move data and applications to cloud platforms, requiring new methods to secure environments outside traditional perimeters.
Application security ensures that software is developed with security in mind, reducing vulnerabilities that could be exploited by attackers.
Data security encompasses measures such as encryption, tokenization, and data loss prevention (DLP—a set of tools and processes that prevent sensitive data from leaving an organization's control) to protect sensitive information from unauthorized access or leaks.
Together, these domains create a comprehensive defense strategy.
How Does Cybersecurity Work?
Cybersecurity operates through a layered defense model, often referred to as defense in depth. Rather than relying on a single tool or barrier, it combines multiple measures to reduce the likelihood of a successful attack.
Preventive controls such as firewalls and access restrictions are designed to stop threats before they cause harm.
Detective controls, such as monitoring systems and security information and event management tools, help identify malicious activity in real time.
Corrective controls, including incident response plans and recovery strategies, ensure that damage can be minimized and operations restored quickly.
These technical controls are supported by policies, training, and governance frameworks that align security with organizational goals. Cybersecurity works best when it is proactive, anticipating threats before they materialize, but it must also be reactive to quickly respond when incidents occur.
Cybersecurity Best Practices for Individuals and Organizations
Building a strong cybersecurity posture requires both individuals and organizations to adopt best practices.
How Can Individuals Protect Themselves?
For individuals, strong cybersecurity starts with fundamental habits. This means creating strong, unique passwords for each account and storing them in a password manager rather than reusing the same password everywhere. Enabling multi-factor authentication adds an extra layer of protection, requiring both a password and a second verification method like a text message code or authenticator app.
Keeping devices and software updated is essential, as updates often patch security vulnerabilities that attackers could exploit. Exercising caution with emails and links is critical—be skeptical of unexpected messages asking you to click links or download attachments, even if they appear to come from someone you know. Finally, backing up important data regularly to an external drive or cloud service ensures you can recover files if they're lost to ransomware or hardware failure.
What Should Organizations Do?
For organizations, best practices expand to include regular risk assessments that identify vulnerabilities and prioritize security investments. Penetration testing, where ethical hackers simulate attacks, helps find weaknesses before real attackers do. Compliance with security frameworks like SOC 2 (a standard that evaluates how well a company protects customer data) or ISO/IEC 27001 (an international standard for information security management) provides structure and demonstrates commitment to security.
Employee awareness training is essential, as human error remains one of the most common entry points for attackers. A single employee clicking a phishing link can compromise an entire network, making regular training a critical investment.
Developing an incident response plan ensures that if a breach occurs, the organization can react swiftly and minimize damage. Businesses should also back up critical data regularly and consider adopting modern security models like Zero Trust (a security model that assumes no user or device should be trusted by default, requiring continuous verification of identity and access permissions).
Cybersecurity is not just about technology; it is about creating a culture of security that permeates every level of an organization.
The Role of Cybersecurity Professionals
Behind the technologies and processes are the people who dedicate their careers to protecting digital environments. Cybersecurity professionals work in roles such as analysts who monitor networks for suspicious activity, penetration testers who simulate attacks to find weaknesses, and incident responders who mitigate breaches. Leadership roles, such as chief information security officers, provide strategic direction and ensure alignment with business objectives.
The field also includes specialists in areas like digital forensics, cryptography, and threat intelligence. With the rising demand for skilled professionals, cybersecurity has become one of the fastest-growing career paths in technology. These experts are not only defenders of digital assets but also educators, researchers, and innovators driving the field forward.
Emerging Trends in Cybersecurity
As of October 2025, the cybersecurity landscape is constantly evolving as new technologies create both opportunities and risks. Artificial intelligence and machine learning are being used to detect patterns and anomalies in vast amounts of data, improving the speed and accuracy of threat detection. At the same time, attackers are also using AI to craft more sophisticated phishing attempts and automated exploits.
The rise of the Internet of Things has dramatically expanded the attack surface, with billions of connected devices creating new vulnerabilities. The Zero Trust model is gaining momentum, shifting the approach from assuming trust within a network to requiring continuous verification of every user and device.
Meanwhile, regulatory requirements such as GDPR (General Data Protection Regulation, the European Union's comprehensive privacy law) and CCPA (California Consumer Privacy Act, which gives California residents rights over their personal data) are shaping how organizations handle and secure personal data. Staying informed about these trends is essential for organizations to remain resilient in the face of evolving threats.
The Future of Cybersecurity
Looking ahead, cybersecurity will only grow in importance as technology continues to advance.
Will Quantum Computing Break Cybersecurity?
Quantum computing poses both opportunities and risks for cybersecurity. On one hand, quantum computers could potentially break current encryption methods that protect everything from bank transactions to government communications. Many of today's encryption algorithms rely on mathematical problems that would take traditional computers thousands of years to solve—but quantum computers could crack them in hours.
On the other hand, quantum computing also enables new forms of secure communication through quantum cryptography, which uses the principles of quantum mechanics to create theoretically unbreakable encryption. The cybersecurity industry is already working on "post-quantum cryptography"—new encryption methods designed to resist quantum attacks. The transition will take years, but organizations should begin planning now for a post-quantum world.
Beyond quantum computing, automation will likely play a larger role in helping organizations keep up with the scale and speed of modern attacks. Global collaboration will be critical, as cyber threats transcend national borders and require cooperation between governments, businesses, and individuals. The future will demand not only stronger defenses but also smarter, adaptive strategies that evolve alongside the threat landscape.
Conclusion: Protecting the Digital World
Cybersecurity is no longer a technical niche; it is the foundation of trust in the digital world. By understanding the threats, embracing best practices, and investing in both technology and skilled professionals, we can build resilient systems that support innovation and progress. While cybercriminals will continue to evolve their tactics, cybersecurity offers the tools and strategies to stay one step ahead. Ultimately, protecting the digital world is a shared responsibility, one that ensures our data, systems, and connections remain secure in the face of constant change.
Next Steps: Explore related topics in our InfoSec Essentials, or dive deeper into specific areas like Data Loss Prevention, Insider Threat Management, or Cloud Data Security.
Frequently Asked Questions About Cybersecurity
What does cybersecurity protect?
Cybersecurity protects digital assets—including data, networks, devices, and systems—from unauthorized access, theft, damage, and disruption. It safeguards sensitive information like financial records, personal identities, intellectual property, and critical infrastructure such as power grids and healthcare systems.
What are the three main goals of cybersecurity?
The three main goals, known as the CIA Triad, are Confidentiality (ensuring only authorized users access sensitive data), Integrity (maintaining data accuracy and preventing unauthorized changes), and Availability (ensuring systems and data are accessible when needed).
What's the difference between cybersecurity and information security?
Cybersecurity focuses specifically on protecting digital systems, networks, and data from cyber threats like hacking and malware. Information security is broader, encompassing the protection of all information (digital and physical) from unauthorized access, use, or disclosure. Cybersecurity is a subset of information security.
What are the most common cybersecurity threats?
The most common threats include malware (viruses, ransomware, spyware), phishing attacks (deceptive emails or websites), distributed denial-of-service (DDoS) attacks that overwhelm systems, insider threats from employees or contractors, and advanced persistent threats (APTs) involving long-term, targeted infiltration by sophisticated adversaries.
How much does cybersecurity cost businesses?
The cost varies widely. Small businesses may spend $5,000–$50,000 annually on basic security tools and services, while large enterprises invest millions in comprehensive programs. However, the cost of a data breach averages $4.45 million per incident (IBM, 2023), making cybersecurity a critical investment rather than an expense.
Do I need cybersecurity if I'm just a small business?
Yes. Small businesses are increasingly targeted because they often have weaker defenses than larger organizations. In 2024, 43% of cyberattacks targeted small businesses. Even basic measures—like multi-factor authentication, regular backups, and employee training—can significantly reduce risk.
What is Zero Trust in cybersecurity?
Zero Trust is a security model that assumes no user, device, or network should be trusted by default—even if inside the organization's network. It requires continuous verification of identity and access permissions for every user and device, minimizing the risk of insider threats and lateral movement by attackers.
How does AI impact cybersecurity?
AI enhances cybersecurity by detecting patterns and anomalies in massive datasets, enabling faster threat identification and response. However, attackers also use AI to craft more sophisticated phishing attempts and automate exploits. The result is an ongoing evolution where both defenders and adversaries use machine learning to gain advantages.
What certifications should cybersecurity professionals have?
Common certifications include CISSP (Certified Information Systems Security Professional) for leadership roles, CEH (Certified Ethical Hacker) for penetration testers, CompTIA Security+ for entry-level professionals, and CISM (Certified Information Security Manager) for management positions. Specialized certifications like OSCP and GIAC address advanced technical skills.
How often should I update my cybersecurity strategy?
Cybersecurity strategies should be reviewed and updated at least annually, or whenever significant changes occur—such as adopting new technologies, experiencing a security incident, or facing new regulatory requirements. Continuous monitoring and adaptation are essential to stay ahead of evolving threats.







.avif)
.avif)
