Learn more about how Cyberhaven enables proactive Insider Risk Management from the dashboard and what this means for data protection and securing sensitive data across your organization.
In today’s digital age, organizations employ a myriad of security programs to safeguard their networks, data, and systems from external threats. Employees interact daily with firewalls, antivirus software, multi-factor authentication, and other protocols, all designed to fortify their company’s defenses. However, while these tools are crucial in thwarting external attacks, they often overlook a critical vulnerability: the risk posed by insiders.
Employees, with their extensive access and intimate knowledge of company operations, stand as both an organization’s greatest asset and most persistent source of risk. Insider threats, whether stemming from malicious intent or accidental misuse, can bypass traditional security measures, putting sensitive data at risk. The challenge, therefore, lies in empowering employees while simultaneously protecting against these internal vulnerabilities.
Traditionally, strategies to mitigate these risks have placed a substantial maintenance burden on security teams and often fall short of securing a company’s precious data. Cyberhaven offers information security teams a proactive and sensible approach to combating this risk
and safeguarding their company.
Combine data awareness with behaviors to accurately detect risk
To combat risk, you must first detect it. Easy enough in theory, but the conventional ‘anomaly detection’ approaches lead to a cacophony of alerts, many of which are false positives. Employees’ work patterns can vary dramatically, influenced by shifting business needs or personal usage of company resources. This variability can generate numerous alerts, overwhelming security teams and potentially leading to genuine threats being overlooked.
Cyberhaven takes a structured approach to detecting insider risks that results in greater accuracy. First, security teams utilizing Cyberhaven define their company’s sensitive data types by combining content based rules with the context provided by the lineage of a piece of data, such as the application it was sourced from or if certain employees produced it. With their company’s most sensitive assets defined, teams then define policies regarding acceptable use of data – what destinations data should be allowed to move to.

Cyberhaven then scores risk directly based on the severity of risk in data movement and the sensitivity of the data at play. The result of this approach is greater confidence that the users flagged by Cyberhaven actually pose risks to your company’s information security.
Deep dive into risks using data lineage
When a security alert is triggered, the ensuing investigation must be swift and decisive. However, insider threat tools often provide low-context alerts that can turn these investigations into prolonged endeavors, fraught with uncertainty and draining precious time from addressing other threats. Security teams must be equipped to promptly address the fundamental questions of any investigation— who, what, when, where, and why— to ensure swift and appropriate action.
Out-of-the-box, Cyberhaven tracks and connects the dots of data movement throughout your organization. The lineage of the data provides complete context on the lead up to a potential insider risk, not only revealing answers to simple questions like:
- Who put the data at risk?
- What data was put at risk?
- When did the incident occur?
But also allowing you to dive deeper:
- Were there attempts to obfuscate the data before it was put at risk?
- Did other employees contribute to putting data at risk?
- What locations did the data pass through before being put at risk?
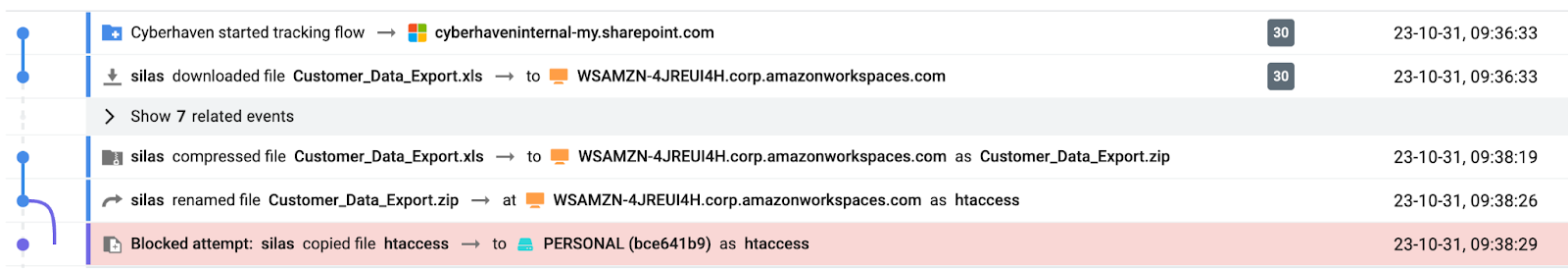
All this context can be shared with teammates, managers, and other departments to ensure proper action is taken with the employee and improvements to information security are made if needed.
Escalate restrictions with real-time enforcement options
Many existing solutions for insider risk management fall short of actually protecting your organization from insider risk due to their architectural limitations, incapable of enforcing data protection policies. While detection of potential threats is a step in the right direction, allowing sensitive data to leave the organization’s secure confines is unacceptable. This not only jeopardizes the organization’s security but also its reputation, competitive edge, and compliance with regulatory standards.
Cyberhaven utilizes one agent to detect and provide options to contain insider risk to data. Policies can be configured to not just alert your team and score risk, but also prevent the risky movement of data entirely. These controls can prevent data from flowing via most egress methods, such as email, cloud sharing, USB device, copy/paste and more.
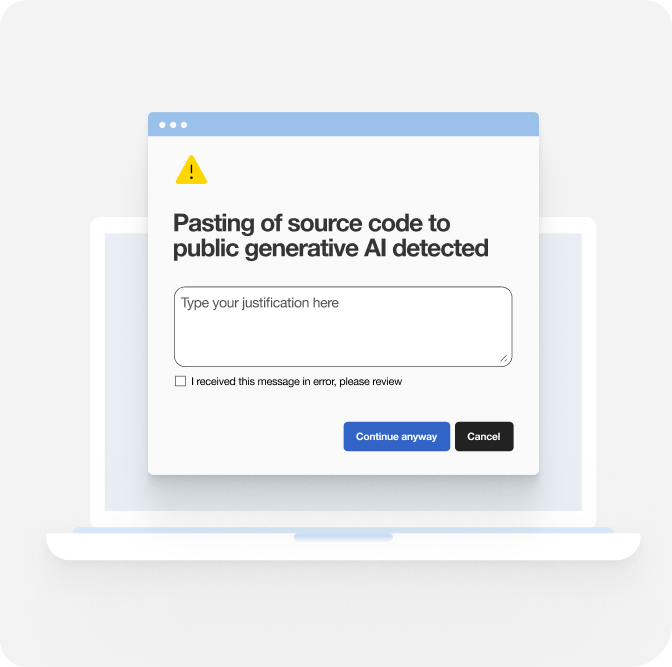
If a risky user is identified, you can place them on a watchlist with increased monitoring or restrictions on data movement. These safeguards allow your team to be proactive rather than reactive in responding and containing insider risk.

The insider risk management page in Cyberhaven allows teams to accurately detect, quickly triage, and proactively respond to insider risks. It is available in early access for all Cyberhaven customers on version 23.10 or higher. Please contact your CSM to learn more and join the early access program!

.jpeg)






.avif)
.avif)
