Employee layoffs pose security challenges when proper provisioning and exit protocols are not in place. Learn more about the state of layoffs and how to implement these best practices.
Preparing for a downsizing
If your management team is planning a reduction in force (RIF), it’s imperative that you protect company data while doing so, because layoffs are often accompanied by a surge of departing employees taking customer records, source code, product designs, and more. There’s a strong incentive for disgruntled employees to try to take this information to your competitors to land a new job or to leak it to the media. Data also shows that employees take sensitive company information well in advance of a layoff, requiring a two-pronged strategy to protect sensitive information.
Top questions to ask if you’re planning layoffs
If you’re planning a reduction in force, there are several important security considerations you’ll need to make:
- At a foundational level, what are your sensitive data repositories? Which assets are processing sensitive data? Building or referencing an asset inventory can help with this.
- What tools and processes do you have in place to stop an employee from taking sensitive company data with them on their way out the door?
- What corporate data have employees already transferred outside the company's walls, whether maliciously or for convenience, to use in other apps or devices?
- How do you ensure data privacy compliance to prevent penalty fines, or loss of reputation with customers over mishandled data?
- How do you defend against external attackers looking to take advantage of stale SaaS app accounts of departed employees?
- How do you prevent remaining employees from proactively taking copies of data after witnessing their colleagues' dismissal?
Why establishing a secure offboarding process is important
Developing a robust procedure for secure offboarding is important in order to defend the company against security risks, while maintaining productivity of the organization. Enterprises need a process to:
- Revoke access – companies should revoke access to accounts and SaaS applications in a timely manner and rotate API/SSH keys within code repositories or secret stores.
- Physically collect devices – retrieve laptops, phones, tablets, etc. as soon as possible.
- Ensure continuity of operations – develop a plan to delegate projects and handoff accounts and data.
Additionally, careful coordination between various teams is required to prevent insider data leaks. An optimal approach involves collaboration between HR, legal, IT, information security and physical security with each playing a key role:
- Human resources finalizes departures and notifies employees
- IT deprovisions and revokes access to applications and ensures company devices are locked and wiped in a timely manner. Ideally, the HR system can serve as an authoritative source of identity, wherein offboarding in the HR system would also remove access to downstream systems via platform integrations.
- Physical security disables access to company facilities and in some cases escorts departing employees from facilities
- Information security monitors for unusual behavior, network log-ins, and data exfiltration attempts.
- In a remote world, the HR team organizes a recovery of corporate laptops/phones and, in cases where devices can’t be retrieved, data is wiped remotely.
The timing of these tasks should be coordinated amongst teams. According to Sounil Yu, former CISO of Bank of America and author of the Cyber Defense Matrix, “timing is critical when it comes to employee departures, as the security team needs to be ready and able to terminate someone’s access to all systems and devices as soon as the layoff happens. You want to synchronize the revoking of access all at the same time. That includes the obvious things around network log-ins or access to various enterprise services, but [security teams] often forget about cloud services or service accounts.”
In addition to navigating RIFs with a secure offboarding process, it’s important to take sufficient preventative measures prior to layoffs. In our Insider Risk Report, we observed that when people are laid off or fired, they are more likely to take data.
There is an increase in data exfiltration attempts the day before an employee’s termination — Employees who are fired are 23.1% more likely to exfiltrate data the day before they were fired and 109.3% more likely to exfiltrate data the day they are fired. But data taken on these two days is dwarfed by the data taken every day.
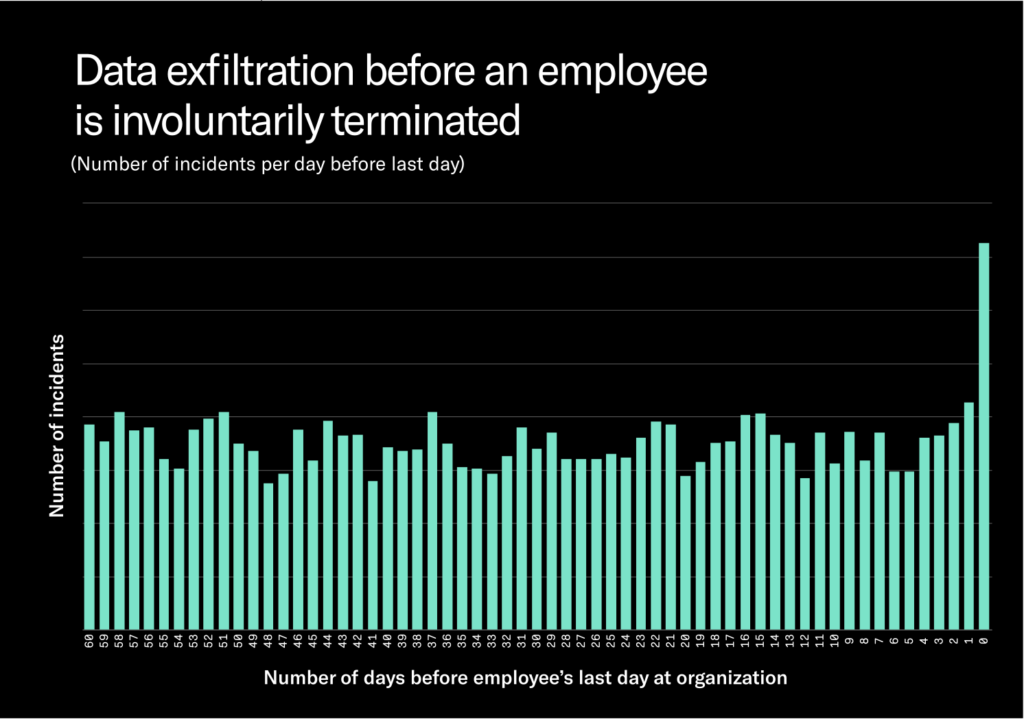
So the important considerations boil down to:
- What data have insiders already taken before they lost access to company accounts?
- What data did insiders take weeks or months ago?
- How do you get that data back or delete copies of it?
- What data do employees still have access to post-termination?
The key to answering these questions requires the ability to track the movement of your company’s data in a way that doesn’t require physical custody of a device. This is critical, because in a remote organization, you may not be able to get an employee’s laptop back in a timely manner, if at all.
Forensics tools used on a laptop in physical custody can be effective for one-off investigative purposes, as seen in the Apple Car data exfiltration case. However, for a larger RIF consisting of thousands of employees, forensics tools simply don’t scale efficiently to track data misuse in a timely manner. When it comes to preparing for layoffs, a more preventative, and programmatic solution trumps forensics tools.
Another risk to watch for is employees that regain access to accounts after they’re let go. Employee accounts should be monitored for unauthorized access. For example, a former Cash App employee downloaded reports containing customer information without permission, after their employment ended.
Two security approaches companies can take:
There are two tactical approaches companies take to prevent data loss, that we see:
- Block employees from transferring ANY sensitive data out
This is a tougher stance against exfiltrations, and requires a data loss prevention (DLP) tool that’s capable of blocking inappropriate data exfiltration – via cloud storage, email, and USB blocking, and modern sharing technologies like AirDrop. While taking a hard stance on data exfiltration offers increased prevention from insider-driven data leaks, the tradeoff is that doing so can impact your company culture. As employees become aware of monitoring tools, they might become unhappy or distrusting of security and leadership. However, regularly touching-base with employees and getting them to internalize security policies through education or coaching can help address this concern.
- The “claw it back” approach
The “claw it back” approach allows for more freedom for employees and an open and permissive culture, while still being vigilant of data movements and possible misuse of data. Leveraging a data loss prevention tool’s monitoring features is key here, in order to reveal the confidential data, an employee may have exfiltrated. In cases where unwanted data exfiltration is discovered, companies can design legal contracts to minimize their business risk. For example, offboarding contracts can include a clause that reminds employees of their confidentiality legal responsibilities, ensuring they are not taking any sensitive company information on their way out. In addition, severance agreements can be made contingent on employees returning copies of confidential files, and/or deleting sensitive data.
How to leverage security tools before and during a layoff
From an offboarding perspective, security products play a critical role in helping enterprises ensure that employees and contractors don’t have access to or copies of confidential company information after they depart the company. Important tools for secure offboarding include:
- Single sign-on (SSO) software (like Okta) – to immediately turn off access to all work applications as soon as an employee is terminated
- Mobile device management (MDM) software (like JAMF) – to remotely lock and wipe a laptop, without physical custody of corporate devices.
- Password management tools (like 1Password) – to automatically change passwords of team and shared accounts, and revoke access.
In addition to SSO, MDM, and password management tools, enterprises can also use data detection and response (DDR) products to protect data every day and in the days leading up to a layoff when the risk of data theft surges.
DDR refers to a new generation of data protection tools designed to address the limitations of today’s existing tools. Unlike DLP, which primarily identifies risk to data through content inspection and unlike insider risk management, which identifies risk through behavioral analysis, DDR leverages both.
Core to DDR is the concept of data lineage or data tracing, which allows for data to be tracked as it egresses from endpoints, applications, and even on-premises services. Data lineage creates a trace of data, every time an event happens. A record of all events taken against data is put together in a graph database, allowing admins to see a piece of data’s journey from its origination to its current location.
Using endpoint telemetry, browser plugins, and cloud APIs, data lineage can illustrate:
- Actions: copy, paste, modify, etc.
- Location: application, website/domain, machine hostname, etc.
- User: username, directory group, departure date, etc.
Data lineage is key to secure offboarding
Data lineage is critical to verifying your offboarding process is going smoothly, as you’ll be able to see in real time what actions employees are taking against data in the days and weeks before their departure and compare that to their behavior over time to understand the significance of any changes.
.jpeg)
Beyond offboarding, knowing where data originated (e.g. the customer data warehouse in Snowflake), how it was handled (e.g. the Board Meeting prep folder on Google Drive), and when employees attempt to remove it (e.g. Apple AirDrop) is now mission-critical intelligence for the coming era of sophisticated risks and threats.
This context can also allow for smart policies, or logic that can define different user actions to determine their riskiness. For example, an employee downloading open-source code from Github could be ignored, but an attempt at downloading the company’s source code could trigger an alert and investigation.
It’s important to leverage data lineage as a preventative measure, not just a post-breach forensics last resort. For context, data tracing solutions need to be deployed well in advance of a RIF. Once a RIF has occurred, it’s not possible to retroactively track what occurred before, so companies should pursue and implement solutions proactively before conducting a RIF.
The modern way to manage offboarding and RIFs
If you’re planning a reduction in force, it’s important to gain visibility around malicious and negligent misuse of data before, not after.
To recap, some important steps to take as part of your RIF security strategy include complete visibility, contextual intelligence, gentle remediation, and instant blocking. Thorough visibility, similar to a “flight recorder,” into data activity automatically across all data silos is important, to match the ever-expanding amount of new SaaS apps used by employees nowadays. Context around each data action (source, destination, people, action, content) is crucial to understand access, exposure, and intent of data usage. A gentle mode of remediation is helpful to educate employees and drive better user behavior in real time, without sacrificing productivity or security. Instantaneous blocking is critical to prevent the loss or risky spread of data – regardless of whether the intent is malicious or negligent.
As more departures at companies increase, whether voluntary or not, we anticipate the surface area for business risk will amplify. Now is the time to proactively leverage modern solutions to tackle these modern security problems.







.avif)
.avif)
