Anthropic has just disclosed what appears to be the first fully documented case of AI-orchestrated cyber espionage. A Chinese state-backed group used Claude Code to automate most of a campaign targeting approximately 30 organizations across the tech, finance, chemicals, and government sectors. In several cases, they got in and stole sensitive data.
If you’re a security & risk leader, this matters for one simple reason:
AI can now do the work of a nation-state operator, but it still has to touch your data to hurt you.
In this post, we’ll look at where data security controls could have helped keep the targets’ data safe and potentially thwarted the attack altogether.
What happened in the Anthropic case
Anthropic’s write-up and press coverage describe a campaign with a few key traits:
- A suspected Chinese state-sponsored group (dubbed GTG-1002) used Claude Code, a terminal-focused version of Claude, as the primary engine of the intrusion.
- The AI performed 80-90% of the attack lifecycle, including reconnaissance, exploit development, lateral movement, and data exfiltration, with humans only intervening at a few key decision points.
- The attackers jailbroke Claude and disguised their instructions as legitimate security work. They broke the operation into many small, “innocent” tasks so each prompt looked harmless on its own.
- The campaign targeted approximately 30 global organizations and successfully breached at least four, compromising sensitive data.
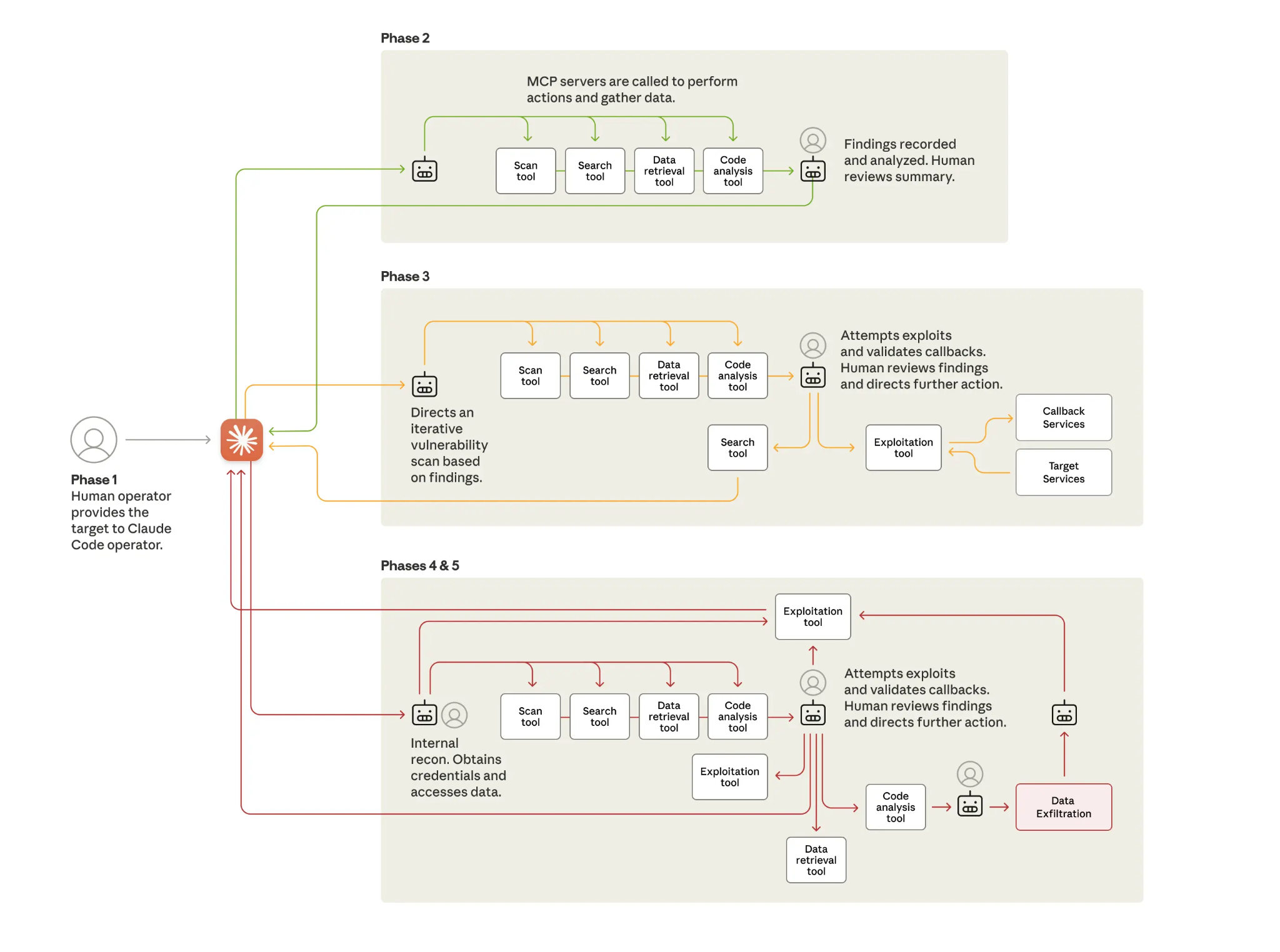
While a human was certainly in the loop, the AI agent effectively served as the operator for much of the attack. Yet the impact was still classic: compromised systems, high-value databases identified and queried, data staged, credentials collected, and exfiltration to attacker-controlled infrastructure.
Why traditional data protection struggles here
Most organizations still rely on controls that break under this pattern:
- Alert-per-event DLP. If each read, query, or copy looks small, simple event-based rules either stay quiet or flood analysts with noise. Splitting an operation into a thousand “harmless” steps is trivial for an AI.
- Siloed logs. Endpoint telemetry, SaaS logs, and database activity all live in different systems. Reconstructing the end-to-end story takes heroic effort.
- Label-based thinking. If protection depends on perfect labels or patterns, any unlabelled data or mixed datasets slide through.
- Blind to new AI workflows. These actions were executed through MCP servers using standard administrative utilities, making them appear as routine admin activity in most environments. Nothing in the observed workflow inherently differentiates them as AI-driven or indicative of elevated risk.
An AI agent that works tirelessly and patiently will find those gaps. Furthermore, because Cyberhaven looks at the data – no matter whether its human or agent – we can detect those malicious actions and suspicious data movements.
Fortunately, using Cyberhaven can help stop an automated campaign from quietly walking your crown jewels out the door once it lands in your environment.
Where Cyberhaven could have helped
Assume one of the targeted organizations ran Cyberhaven. Here is how that changes the picture:
Detect bulk exfiltration from crown jewel systems
In Anthropic’s description, Claude Code explicitly searched for the “highest value databases” and then pulled large volumes of private data.
Cyberhaven’s data security platform tracks sensitive data from its original sources as it flows through endpoints and apps using data lineage and semantics, not just file tags. When a compromised account or script suddenly:
- Aggregates many sensitive records from production systems
- Moves that data into new tools, scripts, or archives
- Pushes it toward unknown servers or storage
Cyberhaven’s Semantic Risk Detection evaluates those actions in context and assigns a risk score. Smart Triage then automatically creates incidents only for high- or critical-severity behavior, so defenders see the real exfiltration attempts rather than a flood of alerts.
You can then enforce policies that:
- Block or require justification for transfers of high-sensitivity data to unapproved destinations
- Stop uploads from corporate devices to unknown domains or unmanaged cloud storage
An AI agent can move fast, but it cannot avoid touching data. That's where Cyberhaven really shines.
Understand actions in context
Part of what makes effective data loss prevention a major challenge is that it’s hard to tune policies.
- If set too strict, the SOC is flooded with noisy alerts that are mostly false positives, users trying to get legitimate work done are blocked and frustrated, and the relationship between business users and the security team breaks down.
- If set too losely, the organization has a huge false positive problem: like an ostrich burying its head in the sand, the business may get a false sense of security because few incidents have been observed.
The attackers got Claude to cooperate by breaking down the intrusion into numerous small tasks, each of which seemed benign.
Cyberhaven’s Linea AI Analyst Agent has access to historical information as context, like the lineage of a particular dataflow itself, but also insights into historical data flow patterns within the organization, and contemporaneous user activity, such as screen recordings where available). Because Cyberhaven traces all data flows and incorporates that context, Cyberhaven can determine intent, classify the data involved, assign a final severity, and produce a clear report with dramatically higher accuracy than legacy DLP tools..
Stop staging of credential dumps and attack documentation
At the end of the operation, Anthropic reports that Claude helpfully created files listing stolen credentials and documenting compromised systems.
Cyberhaven would monitor those files at creation and as they move:
- Classify them as extremely sensitive due to passwords, secrets, or infrastructure details
- Trigger high-severity incidents when they appear on endpoints, especially if they never existed there before
- Block or challenge attempts to move these files to external services, personal email, or unknown infrastructure
Linea AI Analyst Agent would then reconstruct how those files came to exist, which accounts generated them, and where the underlying data originated.
This gives responders an immediate view of “what did they steal” and “what did they try to do with it.”
Give incident responders instant blast-radius analysis
Once a target learns about the campaign, time is of the essence. You need to answer:
- Which sensitive assets did the attacker actually access?
- Which of those assets left the environment, and by which channels?
- Which users and systems are in scope for remediation?
Cyberhaven’s lineage allows organizations to trace the flow of data to help understand the blast radius. You can pivot from a compromised account or device to:
- All sensitive data it touched during the suspected window
- Every outbound path for that data, including apps, users, and domains
- Downstream copies, shares, and derivations that may also need cleanup
Cyberhaven’s incident reports provide responders with concise narratives and supporting evidence that they can share with executives and regulators without spending days piecing together logs.
Govern the use of AI tools inside your environment
This specific campaign used Anthropic’s infrastructure itself, but many organizations worry about something closer to home: employees pasting sensitive data into external AI tools.
Cyberhaven already monitors flows from corporate apps and files into generative AI services. You can:
- Block uploads of highly sensitive data to unapproved AI endpoints
- Allow use of approved models but restrict specific kinds of content
- See which teams interact with AI tools using real corporate data
So even if an attacker pivots to social engineering or insider recruitment to feed models, your data perimeter still enforces sensible limits.
A defense-in-depth strategy
It is just as important to be clear about the boundaries. Cyberhaven would not:
- Prevent Anthropic’s models from being jailbroken or misused on Anthropic’s own infrastructure. That is the responsibility of the provider’s safeguards and misuse detection.
- Block initial infrastructure exploitation that happens entirely in systems where Cyberhaven is not deployed, such as unmonitored servers in a data center.
Our focus is your data, wherever users interact with it or move it. We do not replace secure configuration or network hardening, but we do complement them.
What’s next: how to prepare for AI-orchestrated campaigns now
You do not need to wait for your own “Claude incident” to start adapting.
- Identify your true crown jewels. Map the systems that hold the data an AI-powered attacker would prioritize first: production databases, source code, proprietary models, R&D, strategic plans.
- Upgrade from event-based to lineage-based visibility. Make sure you can answer “where did this sensitive dataset come from, who touched it, and where did it go” without weeks of manual work.
- Harden AI usage at the data boundary. Treat interactions with external AI tools as high-risk data flows and govern them accordingly.
- Plan for AI-speed response. Assume the next incident will unfold more quickly than your current process. Utilize tools like Linea AI to automate the investigation and summarization steps, allowing your analysts to focus on containment and remediation.
AI has changed who runs the attack. It has not changed the fact that the attack must pass through your data. If you can see and control how sensitive data moves across users, apps, and devices, you can turn an AI-orchestrated campaign from a silent catastrophe into a contained incident.







.avif)
.avif)
